A massive campaign to steal digital identities is hitting more than 100 large organisations. Researchers at pre-emptive cyber defence firm Silent Push say the activity is driven by ShinyHunters, working in coordination with Scattered Lapsus$ Hunters as part of a broader alliance the firm tracks as SLSH.
According to Silent Push’s blog post, these hackers are not just using automated bots; instead, they are using a human-led method called voice phishing, or vishing. This involves a real person calling employees or help desks to trick them into giving up their login details.
How the trick works
The group reportedly uses a tool called a Live Phishing Panel. Most companies, as we know them, use Single Sign-On (SSO), such as Okta, which allows a worker to use one password for all their work apps. The hackers set up a fake login page that looks exactly like the real one.
When a victim enters their details, the attacker sits in the middle and watches in real-time. This allows them to steal even the special security codes sent to a user’s phone, effectively bypassing standard security. Researchers described this as a “skeleton key” that gives the criminals access to every app and piece of data in the company.
The goal of the attack
It is worth noting that these hackers have a specific plan once they get inside. According to researchers, they quickly steal sensitive files to blackmail the company. If the business does not pay, the hackers often lock the company’s data so it cannot be used. Further probing revealed that they also use stolen accounts to message other employees on apps like Slack or Teams, pretending to be a colleague to gain even more power within the system.
The list of victims spans several industries, including big names like Telstra in telecoms, Mercury Insurance, and tech companies like Canva and ZoomInfo. Even legal firms and healthcare providers have been targeted in the last 30 days.
Connecting the dots: Recent leaks
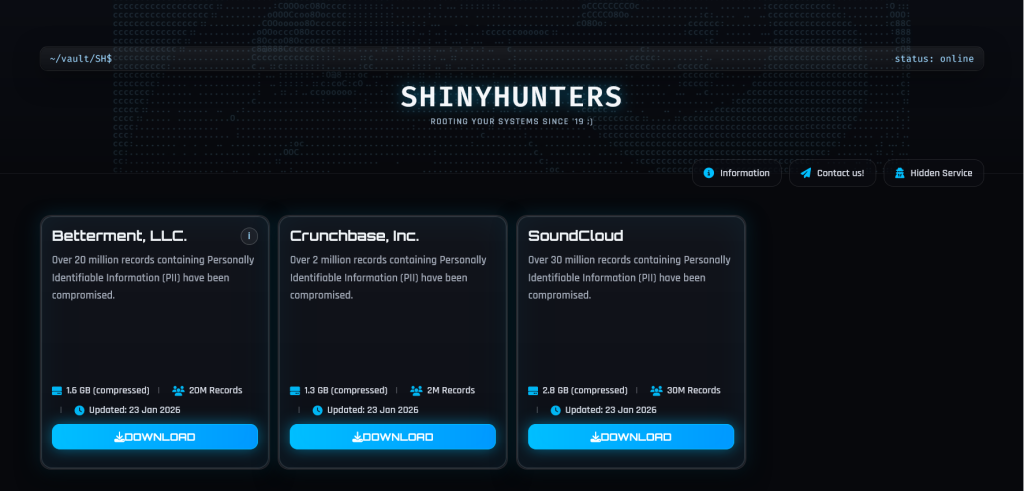
This warning from Silent Push comes at a time when ShinyHunters members are already proving how serious their threats are. Recent coverage by Hackread.com shows that the ShinyHunters faction has been particularly active, launching a new leak site on the dark web just days ago.
According to reports, the group has already begun releasing stolen data from major names like SoundCloud, Crunchbase, Betterment, and Panera Bread after their ransom demands were ignored. These latest leaks, involving millions of personal records, highlight the “pay or leak” strategy that researchers noted is central to how the SLSH alliance operates.
To stay safe, it is important to warn staff about these fake calls, and any strange requests for login help should be reported to managers immediately. Businesses should also check their security logs for any “New Device Enrolled” alerts followed by logins from unusual locations. By using an early warning system for blocking these fake domains early, companies can stop the hackers before they ever make their first phone call.
