Cybercrime can be facilitated in a myriad of ways, and one of the ways is adapting to new techniques and employing third-party services.
Recently, three online threats have come to the spotlight, and the collective attack pattern of these three is causing concerns. The Skynet DDoS provider, Anonymous Sudan, and Russian hacker groups seem to have an intricate web of criminalization.
Their inadvertently combined efforts have resulted in cyber-attacks on prominent firms such as vxunderground, Apple, Telegram, Azure, Sucuri, StackPath, and PlayStation, leaving experts scrambling to decipher the motives behind these assaults.
How Skynet Targets a Broad Spectrum of Victims
Skynet, a formidable DDoS provider, has proven its capability by launching attacks on several high-profile entities.
Its victims are tech giants like Apple and Telegram, cloud services like Azure, cybersecurity solutions provider Sucuri, content delivery network StackPath, and gaming titan PlayStation.
The scope of Skynet’s targets is expansive, highlighting its potential to disrupt operations on a massive scale. The attacks orchestrated by Skynet are believed to be endorsed by Anonymous Sudan.
This affiliation suggests a strategic collaboration wherein Skynet may facilitate low-impact attacks on various platforms at the behest of Anonymous Sudan.
The nature of this relationship raises questions about the broader agenda of both entities. Adding another layer of complexity, suspicions arise regarding the involvement of Russian hacker groups.
These groups, which exerted significant influence over Microsoft in recent months, may be experiencing a shift in their support base.
The evolving dynamics within the Russian hacker community further muddy the waters surrounding these cyber threats.
Skynet and Anonymous Sudan target Telegram
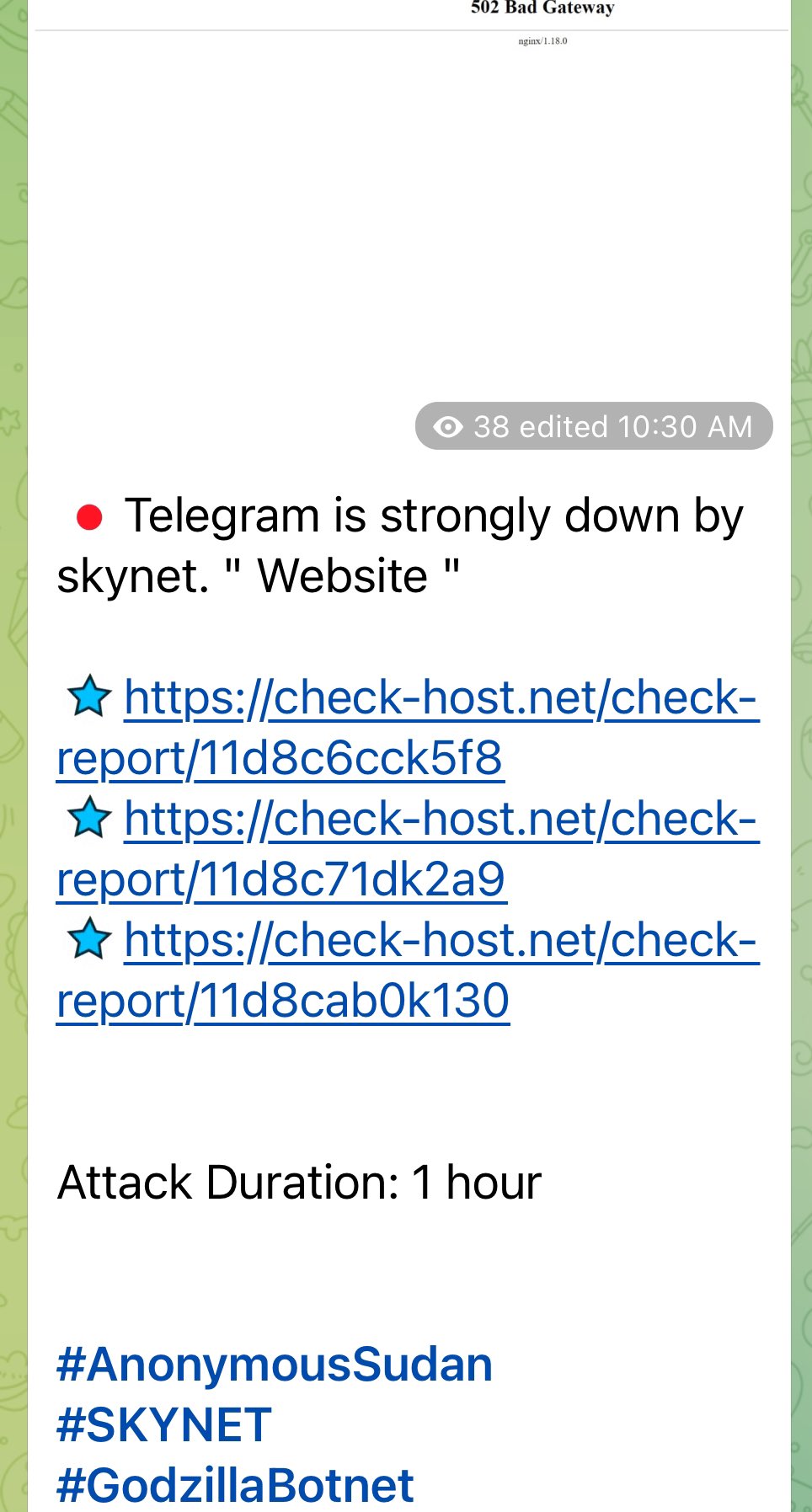
One of the most notable attacks attributed to Skynet and Anonymous was its assault on the popular messaging platform Telegram.
In a bold move, Skynet claimed responsibility and provided corroborative evidence through check-host links.
The alleged attack, which lasted for one hour, left Telegram users grappling with service disruptions, emphasizing the potency of Skynet’s capabilities. However, the authenticity of this cyber attack cannot be verified at this point.
Anonymous Sudan has openly aligned itself with pro-Russia sentiments, solidifying its membership within the pro-Russia hacktivist collective Killnet.
This affiliation is evident through the active promotion of attacks by Anonymous Sudan, the primary Killnet Telegram channel, and the Anonymous Russia Telegram channel.
Skynet has maintained a decade-long presence on the Tor Network, utilizing data center facilities to launch DDoS attacks.
The Tor network is the conduit for commanding the Skynet botnet, with its Command and Control (C&C) servers accessible exclusively within this anonymizing framework. This covert infrastructure further complicates efforts to trace and mitigate Skynet’s activities.
Anonymous Sudan employs a multi-faceted strategy, utilizing public cloud server infrastructure to generate traffic and launch flood attacks.
Additionally, they leverage free and open proxy infrastructures to obfuscate the origins of their attacks.
Their primary vectors include defacement attacks, Distributed Denial of Service (DDoS) attacks, and compromise of email accounts, with DDoS attacks emerging as the preferred method for disrupting targeted organizations.
While connections between Anonymous Sudan and Skynet remain elusive, the notoriety of both entities cannot be ignored.
The evolving narrative surrounding these threat actors is one that The Cyber Express continues to monitor.
Updates will be provided as more information surfaces, potentially shedding light on the intricate interplay between Skynet, Anonymous Sudan, and Russian hacker groups.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
