TheTruthSpy, a seemingly harmless surveillance application, has been secretly gathering sensitive data from users worldwide, despite its advertised purpose of monitoring children or employees. A flaw in the system allows unrestricted access.
TheTruthSpy, a consumer-grade spyware operation, got hacked twice in 2022 and may have broken a world record by being hacked for the fourth time in the same manner, making around 50,000 Android devices vulnerable to cyberattacks. TheTruthSpy has been reportedly monitoring large clusters of victims across Europe, India, Indonesia, the US, and the UK, the latest data being from December 2023.
Switzerland-based hacker Maia Arson Crimew wrote in a blog post published on 12th February 2024. In December 2023, two independent hacking groups ByteMeCrew and SiegedSec discovered and exploited an IDOR vulnerability in the 1Byte-owned TheTruthSpy stalkware, which allows data retrieval directly from TheTruthSpy servers without verifying the client’s right to do so.
Originally reported by TechCrunch, this yet unfixed vulnerability allows for easy enumeration and scraping of data that is typically difficult to access otherwise.
The hacking led to granting access to over 140,000 mobile devices. The affected data includes application logs, text logs, call history, contact logs, browser history, location info, photos, notes, call recordings, IMEI, phone OS, and version.
Maia, who, according to their blog post, had exclusively received a cache of breached data from ByteMeCrew, collaborated with tech journalist Zack Whittaker to investigate the issue. Whittaker reached out to server hosts and payment providers, forcing the company to switch to a Moldovan host company called AlexHost, and via crypto, they moved checkouts to p2p payments through their support portal.
Their investigation involved monitoring a daily English pronunciation training app website using Firefox developer tools. Multiple IDOR vulnerabilities were found, allowing access to user data and analytics tracking data without authentication. Matching this data with employee names provided personal email addresses and phone numbers.
TheTruthSpy app is known for its advanced surveillance capabilities, with the ability to stay hidden on home screens, but fails to prioritize the security of the data it steals, as it continuously uploads the victim’s phone contents to a dashboard accessible to the abuser.
SiegedSec and ByteMeCrew reportedly, discovered Android device identifiers of every phone and tablet compromised by TheTruthSpy up to December 2023, totaling approx. 50,000 new devices. TechCrunch expanded its free spyware lookup tool to identify more compromised devices.
In their Telegram post, the hacking groups stated they would not disclose the data for being highly sensitive as it includes IMEI numbers and advertising IDs of thousands of Android phones.
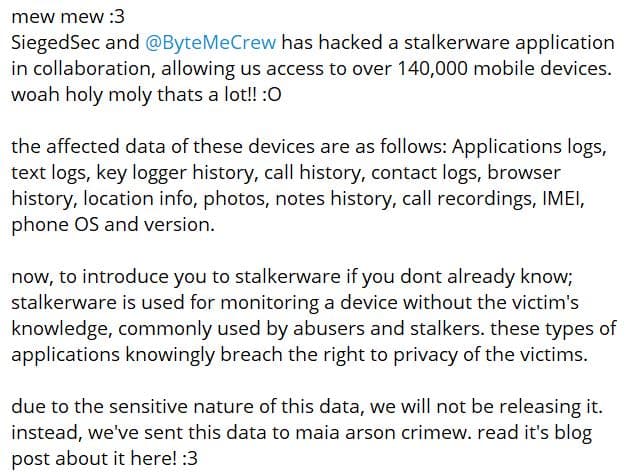
For your information, stalkerware is malicious software that monitors a victim’s device without their knowledge, often used by abusers and stalkers to track activities, knowingly violating their privacy rights.
The investigation reveals that 1Byte’s stalkerware platform and other ventures, including educational tools under the VardyTest brand, are gravely insecure. TheTruthSpy is posing a serious security and privacy risk to thousands of Android users due to a simple security flaw that its operators have not fixed. Given the number of times it got hacked, the only way forward is to shut down operations and disband to show user safety, Maia concluded.
RELATED NEWS
- Hacker erase 1 terabyte of data from spyware developer server
- Parental spyware app Family Orbit hacked; 281 GB of data exposed
- Iranian Stalkerware ‘Spyhide’ Steals Data from 60,000 Android Devices