- Japanese cybersecurity firm Trend Micro has detected a new malware attack campaign dubbed ROMCOMLITE.
- Cyberespionage gang Void Rabisu is targeting female Politicians and government officials. with the new ROMCOM backdoor variant.
- This new variant is compact and stealthier than its predecessor.
- Attackers are using spear-phishing to distribute the backdoor through fake meeting invites.
- If the malware invades a system successfully, it can harvest data, execute remote commands, or capture screenshots.
A notorious cyberespionage group Void Rabisu, aka Storm-0978, Tropical Scorpius, and UNC2596, has launched a brand-new campaign targeting female political leaders and government officials using a revamped version of a previously detected ROMCOM backdoor.
Hackread.com had reported in July 2023 that Void Rabisu is intensifying its efforts to target politicians, citing a report from the BlackBerry Threat Research and Intelligence team about discovering a campaign where the group targeted Ukraine and NATO supporters with the ROMCOM backdoor RAT delivered via malicious documents.
The ROMCOMLITE campaign was discovered by Japanese cybersecurity firm Trend Micro. This new variant, dubbed ROMCOM 4.0 by Trend Micro and Peapod by Microsoft, allows attackers to gain unauthorized access to the target’s computers and steal sensitive data.
The backdoor was detected in early August, and the malware analysis was published on 31 October. In the report, Feike Hacquebord and Fernando Merces explained that Void Rabisu’s targets were attendees of the Women Political Leaders (WPL) Summit held in Brussels in June 2023.
For your information, Void Rabisu is a sophisticated, hybrid group that conducts espionage and financially motivated attacks and prefers using the Cuba ransomware. It also serves as an APT actor targeting government and military entities/officials.
The gang was discovered first in 2022, but researchers agree that it has been active for a long time. They also suspect this group harbours a geopolitical agenda, as most of its previous campaigns targeted the Ukrainian government/military and EU political/government governments.
In the recent campaign, Trend Micro noted that the backdoor payload was embedded in a malicious copy of the WPL Summit’s official website to improve gender equality in politics. The malicious new backdoor ROMCOM 4.0 is designed to evade detection and remain hidden on the infected system to avoid raising suspicion.
As per the report, the Videos &photos link of the original domain redirects the visitor to a Google Drive folder containing the event’s photographs. Then the fake website (wplsummitcom) directs the visitor to a OneDrive folder containing two compressed files and an executable file (titled: Unpublished Pictures 1-20230802T122531-002-sfx.exe), which is malware.
The gang created this fake website on 8 August, primarily to attract visitors from the original WPL summit domain. The executable file is signed with a valid certificate by a firm called Elbor LLC and extracts 56 photos from its resource section after the user clicks on Extract.
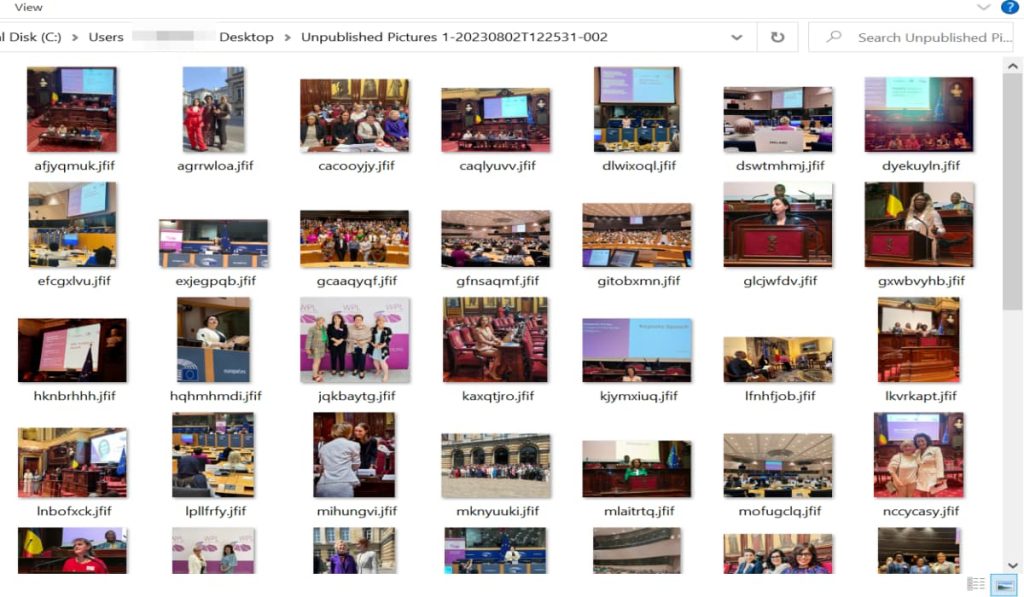
Attackers use spear-phishing tactics to lure their targets. They send fake meeting invitations and other lures so that the targets open malicious attachments or click on links containing the malware.
This is a similar tactic Void Rabisu has used in its campaign discovered in June 2023, where the gang used lures related to the Ukrainian World Congress and the July NATO summit to deliver a zero-day exploit based on an RCE vulnerability in MS Office and Windows HTML, tracked as CVE-2023-36884. Microsoft disclosed this campaign in July.
However, Trend Micro report reveals that the group has used a new tactic in this campaign involving TLS-enforcing by the RomCom C2 servers to make discovering ROMCOM’s infrastructure hard to detect.
“We observed Void Rabisu using this technique in a May 2023 RomCom campaign that spread a malicious copy of the legitimate PaperCut software, in which the C2 server ignored requests that were not conformant,” the report read.
Trend Micro claims there’s no evidence to believe Void Rabisu is a state-sponsored actor. Still, it is clear that the group is trying to benefit from the “extraordinary geopolitical circumstances caused by the war in Ukraine.”
RELATED ARTICLES
- Hackers Target Israeli Rocket Alert App Users with Spyware
- Gender Diversity in Cybercrime Forums: Women Users on the Rise
- Israeli Rabbi arrested for hacking CCTV cameras at women’ bathing suit shop
