The Storm-1575 group is known for frequently rebranding its phishing infrastructure. Recently, ANY.RUN analysts identified the deployment of new login panels, which are part of the threat actor’s ongoing efforts to compromise users’ Microsoft and Google accounts.
Storm-1575’s New Login Panels
Through analysis of their features, the team was able to link login panels to Storm-1575. Among other things, the panels share:
- Phishing domains
- Random panel page headers
- Use of website templates to mask servers
- Panel token verification request, the same font, and the panel URL
The panels also have their distinctive features:
- Target Accounts: Microsoft vs. Google
- Verification: Cloudflare for Microsoft, arithmetic CAPTCHA for Google
- Encryption: Strong AES CryptoJS for Microsoft, weak obfuscation for Google
The findings confirm that these panels are operated by Storm-1575, a group that previously used the same infrastructure with other phishing platforms such as DadSec, Phoenix Panel, and Rockstar2FA Portal.
How to Proactively Discover New Storm-1575 Attacks
To stay ahead of Storm-1575’s latest phishing tactics, cybersecurity professionals can use ANY.RUN’s Threat Intelligence Lookup.
This powerful platform offers a centralized repository of threat data from ANY.RUN’s malware sandbox sessions, enable users to investigate emerging threats with access to indicators of compromise, network activity, and file behaviours.
One example of Storm-1575’s phishing infrastructure is the domain menlologistics.com. By submitting this domain to the TI Lookup platform, users can uncover key details about its malicious activity.
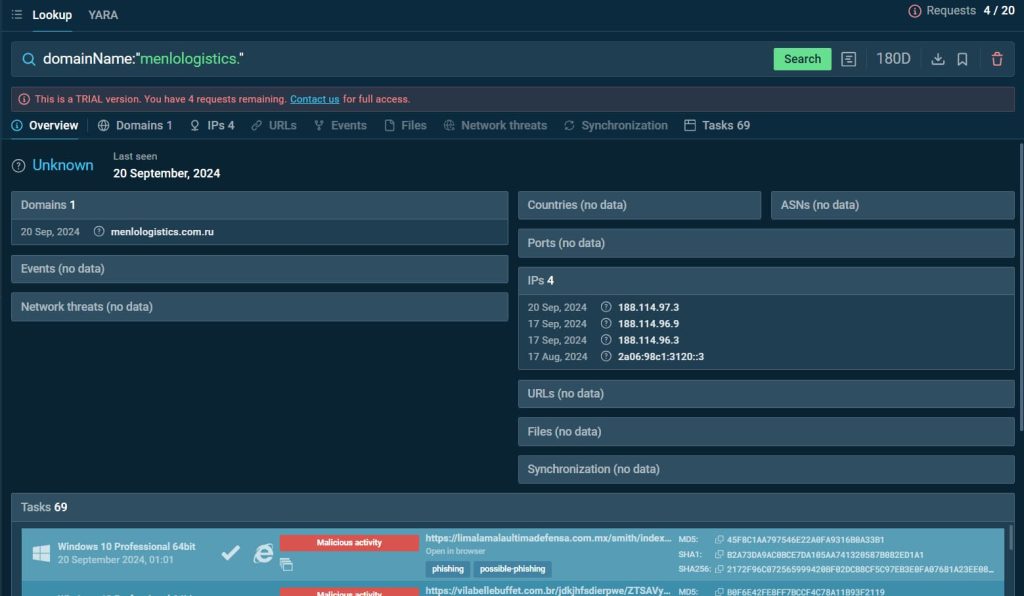
A search query for domainName:”menlologistics.” revealed 4 associated IP addresses and 69 sandbox sessions in ANY.RUN, most of which were linked to phishing activities.
Analysts can also investigate by threat name using threatName:”storm1575″, granting direct access to any recorded session where this threat was detected in the ANY.RUN sandbox.
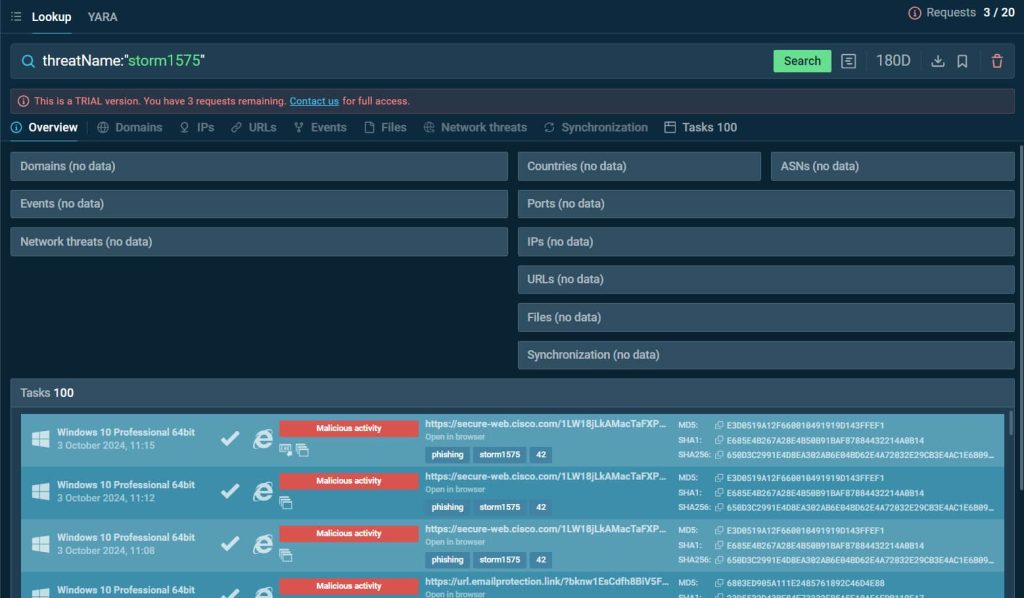
This integration between TI Lookup and the sandbox provides a comprehensive view of the threat landscape, enabling users to review real-time phishing tactics and infrastructure in action.
ANY.RUN Threat Intelligence Portal
If you’re looking to enhance your threat intelligence capabilities, explore ANY.RUN’s TI portal to gain deeper insights into the world of cyber threats and strengthen your defences.
Test ANY.RUN’s Threat Intelligence Lookup to see how it can improve your threat-hunting efforts.
RELATED TOPICS
- Analysis of Top Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- Tycoon and Storm-1575 Linked to Phishing Attacks on US Schools
- ANY.RUN Upgrades Threat Intelligence to Identify Emerging Threats
- StormBamboo APT Targets ISPs, Spreads Malware via Software Updates
