Thousands of gamers found themselves locked out of their accounts this week after a major security flaw forced Ubisoft to pull the plug on its hit game, Rainbow Six Siege. For those who don’t follow the gaming world, Siege is a massive tactical shooter game where teams work together to storm or defend buildings. It is a flagship title for Ubisoft, but over the holiday weekend, it became the most visible victim of a newly discovered vulnerability in MongoDB software, dubbed MongoBleed.
What is happening?
To put it simply, MongoDB is a popular database software used by thousands of companies to store everything from customer addresses to game progress. The problem, officially tracked as CVE-2025-14847, involves a tool called zlib that MongoDB uses to “shrink” data for faster travel.
A mistake in the code allows an outsider to send a corrupted message that tricks the server into “bleeding” out fragments of its own internal memory. Because this happens before the system even asks for a password, it allows unauthenticated hackers to sneak out sensitive information from anywhere in the world. This leaked memory can expose:
- Clear-text passwords and login keys.
- Personal customer information (PII).
- Security tokens that allow hackers to impersonate real users.
The Chaos at Ubisoft
You might wonder how a database vulnerability can shut down a video game. Ubisoft uses MongoDB to store player records, like your rank or the items you’ve unlocked. According to the online malware repository, VX-Underground, different hacker groups have so far used the MongoBleed vulnerability to gain a backdoor into the game’s internal systems.
Once inside, the hackers went on a spree; they hijacked the ban ticker to show fake messages and unban their friends, unlocked every single cosmetic outfit and item for themselves, and gifted a staggering 2 billion R6 Credits (in-game currency) to players.
Ubisoft was forced to take the entire game and its Marketplace offline to stop the bleeding. While they won’t punish players who spent the “free” money, they are currently working to roll back all transactions that happened during the breach.
Active Attacks in the Wild
While the flaw was first disclosed on December 19, 2025, the situation turned critical on December 26 when researcher Joe Desimone published the attack blueprint (public exploit code) on GitHub. Since the release, experts at Wiz and Censys have noted a massive spike in attacks. They estimate that 42% of cloud setups are at risk, with over 87,000 databases currently sitting exposed on the internet.
How to Stay Protected
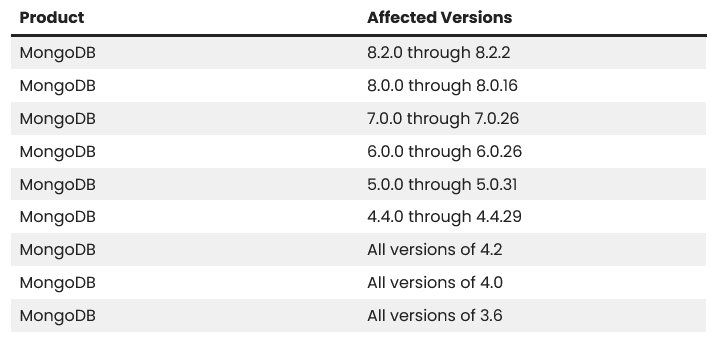
While older versions (like 3.6 or 4.2) have no official fix, newer versions have been patched. To stay safe, you must update to versions 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, or 4.4.30.
If you cannot update immediately, experts suggest turning off the zlib compression setting in your database as a temporary shield to block attackers.
Ben Ronallo, Principal Cybersecurity Engineer at Black Duck, a Burlington, Massachusetts-based provider of application security solutions, also commented on the issue, stating, “The threat actors were clever; they attacked during the holidays when many companies tend to be less responsive due to employees taking time off. Ubisoft appears to be the highest profile victim at this point.“
Ronallo also shared steps for security teams to workaround the issue, including:
- Confirm if you have any internet-facing systems with a vulnerable version of a MongoDB instance attached.
- If you find any such systems, immediately kick off your incident response efforts to identify any potential compromise and contain the damage.
- There’s this open-source tool that can be leveraged to analyze MongoDB logs for indicators of compromise.
- Any vulnerable versions should be patched immediately using official fixes from MongoDB.
