A subfield of forensic science called digital forensics focuses on finding, obtaining, processing, analyzing, and documenting electronically stored data.
Digital forensics support is essential for law enforcement investigations because electronic evidence is a part of almost all criminal activities.
The term digital forensics was first used to refer to the investigation of computer forensics, but it has since come to refer to all devices that can store digital data.
Computers, smartphones, remote storage, unmanned aerial systems, shipborne equipment, and other devices are examples of where electronic evidence can be gathered.

The typical forensic process involves the seizure, forensic imaging (acquisition), and analysis of digital media.
This is followed by the creation of a report outlining the evidence that has been gathered.
Table of Contents
- What is Digital Forensics?
- History of Digital Forensics
- What are the types of Digital Forensics?
- Challenges of a Digital Forensics Investigator
- Phases of Digital Forensics
- Important Digital Forensic Tools
- Objective of Digital Forensics
What is Digital Forensics?
In the field of forensic science known as “digital forensics,” material found on digital devices is recovered, investigated, examined, and analyzed, frequently in connection with computer and mobile device crimes.
The incident response process for businesses includes digital forensics as a critical component.
Law enforcement can use the information forensic investigators gather and record about a criminal incident.
There are many uses for digital forensics research, but the most typical is to prove or disprove a theory in court, whether for a criminal or civil case.
A computer, mobile phone, server, or network are examples of digital media, and the science behind it is to find evidence there.
The most effective methods and equipment are given to the forensic team to handle challenging digital-related cases.
It covers analytical topics like hardware, operating system, network, applications, and storage media.
History of Digital Forensics
| Year | Progress |
|---|---|
| 1978 | The Florida Computer Act |
| 1980s | Rapid growth in Digital Forensics Field |
| 1990s | Adaptive Growth, implemented in various sectors |
| 1970 & 1980 | Federal Law Enforcement |
| 1984 | Operation started by FBI Computer Analysis and Response Team (CART) |
| 1994 and 1995 | Modern British digital forensic methodology developed. |
| 1998 | Good practice guide for Digital Evidence created in the UK by the Association of Chief Police Officers (ACPO) |
The main principles that apply to all digital forensics for law enforcement in the UK are described in the ACPO guidelines.
These recommendations and best practices have gradually become standards as the science of digital forensics has advanced, and the UK’s Forensic Science Regulator now governs the discipline.
What are the types of Digital Forensics?
The process of locating, safeguarding, analyzing, and documenting digital evidence is known as “digital forensics.” It is done so that, if necessary, it can be used as evidence in court.

The scientific field of digital forensics is constantly developing and has many subdisciplines. Several of these sub-disciplines include:
Media Forensics-
Network Forensics:
- The observation, recording, gathering, storing, and analysis of network activities or events to identify the origin of security attacks, intrusions, or other problematic incidents, such as attacks by worms, viruses, or malware, abnormal network traffic, and security breaches.
Wireless Forensics:
- Wireless forensics’ main objective is to provide the tools to gather and analyze the data from wireless network traffic.
Database Forensics:
- It is a subset of digital forensics that focuses on analyzing and investigating databases and the metadata surrounding them.
Software Forensics:
- In an investigation into a crime involving only software, the branch of digital forensics deals with the identification, gathering, analysis, and presentation of digital evidence.
Email Forensics
- Focuses on recovering and analyzing emails, including deleted emails, calendars, and contacts.
Memory Forensics:
- It is also known as live acquisition when evidence is recovered from the RAM of an active computer.
Mobile Phone Forensics:
- It is a subfield of digital forensics that deals with locating, gathering, analyzing, and presenting digital proof of a crime committed using a mobile device (such as a phone, GPS, tablet, or laptop) during an investigation.
Challenges for a Digital Forensics Investigator
Today, people primarily use social media websites and online social networks to bring many aspects of their lives into cyberspace.
Unfortunately, when cloud computing is involved, gathering data to reconstruct and locate an attack can seriously violate users’ privacy and is connected to other challenges.

Typically, criminals use system commands and programs to conceal data chunks in invisible form within the storage medium.
Using a covert channel, an attacker can evade intrusion detection systems and conceal data on a network.
It served the attacker’s purpose of disguising his relationship with the compromised system.
There are no appropriate rules for gathering and acquiring digital evidence in India.
Forensic labs and investigating agencies are developing their own standards. As a result, the value of digital evidence has been diminished.
As the crime rate rises, so does the volume of data, and the burden on a digital forensic expert to analyze such massive amounts of data rises as well, because digital evidence is more sensitive than physical evidence and can easily vanish.
The emergence of Platform as a Service (PaaS) and Software as a Service (SaaS), which have brought about a number of changes to the computing structure, is the result of current technological advancements and changes in gathering forensic evidence.
There are several challenges associated with the use of new software and technology.
Multiple sources presenting conflicting timestamp interpretations, time zone references, and clock skew/drifts create a unified time-lining challenge.
To synchronize timelines from different data sources, sophisticated analytical tools are needed.
Phases of Digital Forensics
Theft or disclosure of data, misuse of the internet, hacking of networks or systems, espionage, and financial fraud are just a few of the wrongdoings that can be found and proven through a digital forensic investigation.
To ensure the accuracy of the data and its admissibility in court, it is essential to conduct a structured and procedure-driven digital forensics investigation in both civil and criminal cases.
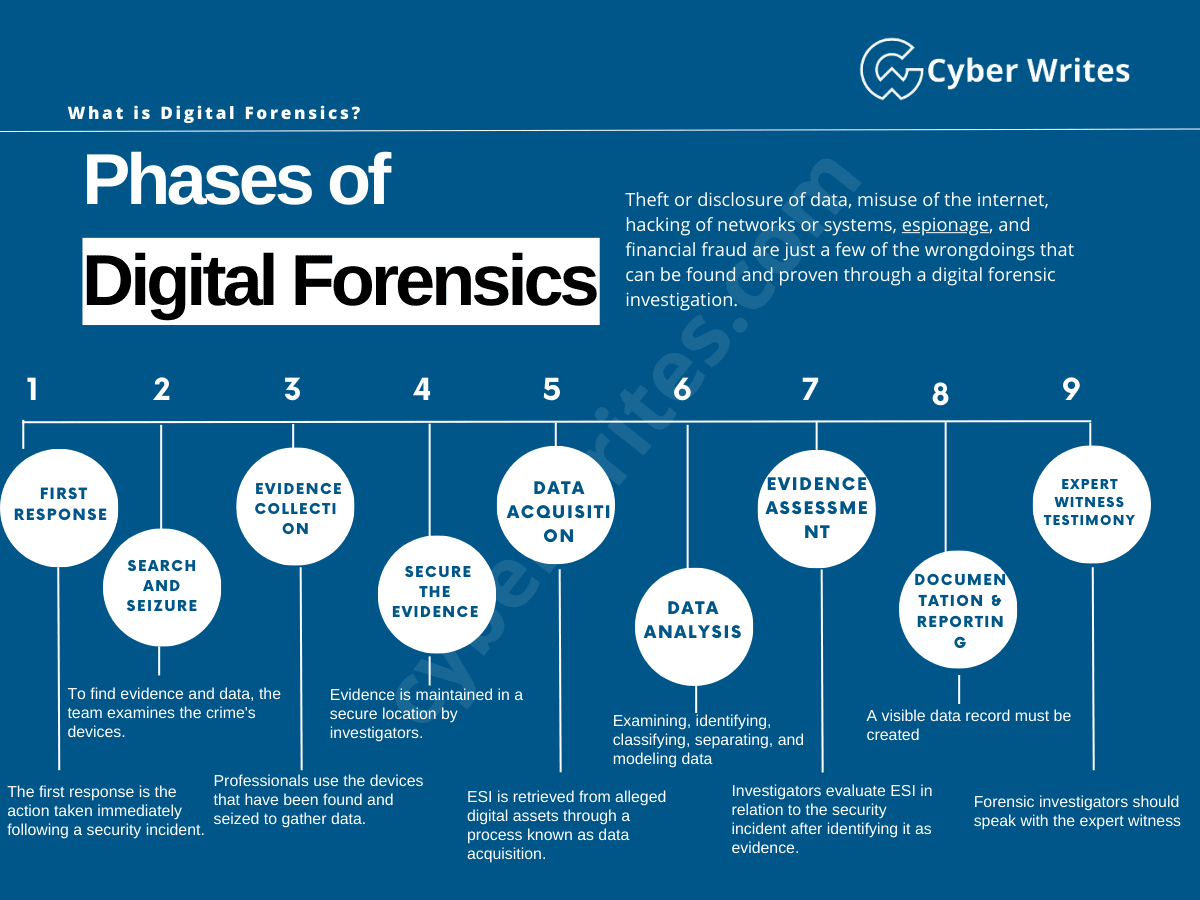
These are some of the essential phases of a digital forensics investigation:
Phase 1 – First Response
- The first response is the action taken immediately following a security incident. The type of incident will have a big impact on it.
Phase 2 – Search and Seizure
- To find evidence and data, the team examines the crime’s devices. Investigators seize the equipment to ensure the offenders cannot commit further crimes.
Phase 3 – Evidence Collection
- Professionals use the devices that have been found and seized to gather data. They use forensic procedures for handling evidence that is clearly defined.
Phase 4 – Secure the Evidence
- Evidence is maintained in a secure location by investigators. Data can be verified to be accessible, accurate, and authenticated in a secure environment.
Phase 5 – Data Acquisition
- Electronically Stored Information (ESI) is retrieved from alleged digital assets through a process known as data acquisition.
- Finding out more about the incident is helpful, but if the process is flawed, the data may be changed, compromising the validity of the evidence.
Phase 6 – Data Analysis
- Examining, identifying, classifying, separating, and modeling data are all steps in this phase that turn it from raw data into usable information.
Phase 7 – Evidence Assessment
- Investigators evaluate ESI in relation to the security incident after identifying it as evidence.
- This stage focuses on directly connecting the information gathered to the case.
Phase 8 – Documentation and Reporting
- In this process, a visible data record must be created. It helps in recreating the crime scene and reviewing it.
- It involves proper crime scene documentation, photographing, sketching, and crime-scene mapping.
Phase 9 – Expert Witness Testimony
- Forensic investigators should speak with the expert witness to confirm the evidence’s accuracy.
- A professional who looks into a crime to find evidence is called an expert witness.
Important Digital Forensics Tools
It is possible to preserve, identify, extract, and document digital evidence to be used as evidence in court.
Many tools are available to you to help you simplify and ease this process, including:
The Sleuth Kit
- With the help of the Sleuth Kit, you can examine disk images and extract files from them using a set of command-line tools and a C library.
- In Autopsy and many other open-source and for-profit forensics tools it is used in the background.
FTK Imager
- FTK Imager is a forensic toolkit created by Access Data that can be used to gather evidence. Without altering the original evidence, it can make copies of data.
- This tool can filter out unnecessary data by specifying criteria like file size, pixel size, and data type.
Xplico
- For instance, Xplico extracts every email (POP, IMAP, and SMTP protocols), every HTTP page, every VoIP call (SIP), every FTP file, every TFTP file, and more from a pcap file.
Network Forensic Analysis Tool (NFAT) Xplico is an open-source alternative to network protocol analyzers.
Paladin
- A number of forensic tasks can be made simpler using the Ubuntu-based tool PALADIN.
- More than 100 practical tools are available in this digital forensics software to examine malicious content.
- Using this tool, you can efficiently and quickly simplify your forensic task.
Prodiscover Forensic
- You can find every information on a computer disk using ProDiscover Forensic, a computer security program.
- It can be used in legal proceedings to safeguard evidence and produce high-quality reports.
- This tool can extract EXIF (Exchangeable Image File Format) data from JPEG files.
Objectives of Digital Forensics
It is helpful for the investigation agency to use the computers and related materials as evidence in court to recover, analyze, and preserve them.
Respond to an incident to prevent further loss of assets, money, and a person’s name during an attack.
Recognize and overcome the techniques and strategies used by attackers to avoid prosecution.
Creating protocols at a suspected crime scene that help you ensure the digital evidence you obtain is not tampered with.
Knowledge of the laws of various regions and areas, such as digital crimes, is widespread and far-reaching.
Assembling a computer forensic report that contains thorough details on the investigation.
The objectives of the analysis phase in the digital forensics process vary depending on the circumstances of each case.
It can also be used to look into information security incidents locally on the system or over a network and to support or disprove assumptions made about specific people or organizations.
In a criminal or civil court, digital forensics is most frequently used to prove or disprove a theory.
By simply copying your evidence drive, acquiring data allows you to conduct an investigation using the copy of the evidence drive rather than the original.