Researchers demonstrated how attackers can bypass its protections without physically tampering with the device. The exploit, known as “bitpixie” (CVE-2023-21563), was showcased at the Chaos Communication Congress (38C3) by security researcher Thomas Lambertz.
The “bitpixie” exploit bypasses Secure Boot by exploiting a downgrade attack on the Windows Boot Manager.
This vulnerability highlights a critical flaw in the default configuration of BitLocker on Windows 11, raising alarms for users relying on it for data protection.
BitLocker, Microsoft’s full-disk encryption technology, is designed to protect sensitive data by encrypting entire drives. It relies on Secure Boot and the Trusted Platform Module (TPM) to ensure encryption keys are only released to trusted components during startup. However, the bitpixie exploit takes advantage of a design flaw in this process.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
“This exploit, dubbed bitpixie, relies on downgrading the Windows Boot Manager. All an attacker needs is the ability to plug in a LAN cable and keyboard to decrypt the disk,” Thomas added.
How Does the Exploit Works?
The vulnerability arises from a failure in the Windows Boot Manager to clear encryption keys from memory during specific recovery flows. Attackers can exploit this by downgrading the bootloader to an older, vulnerable version. This process involves:
- Bootloader Downgrade: Using a network boot (PXE Boot), attackers load an outdated Windows Boot Manager that still contains the vulnerability.
- Triggering Recovery Mode: The downgraded bootloader initiates a recovery sequence, leaving the Volume Master Key (VMK)—the key required to decrypt BitLocker-protected data—in system memory.
- Memory Dump: The attacker then boots into a Linux environment and extracts the VMK from memory using forensic tools.
- Decrypting Data: With the VMK in hand, attackers gain full access to the encrypted drive.
This attack does not require opening the laptop or accessing internal components, making it particularly concerning for stolen devices.
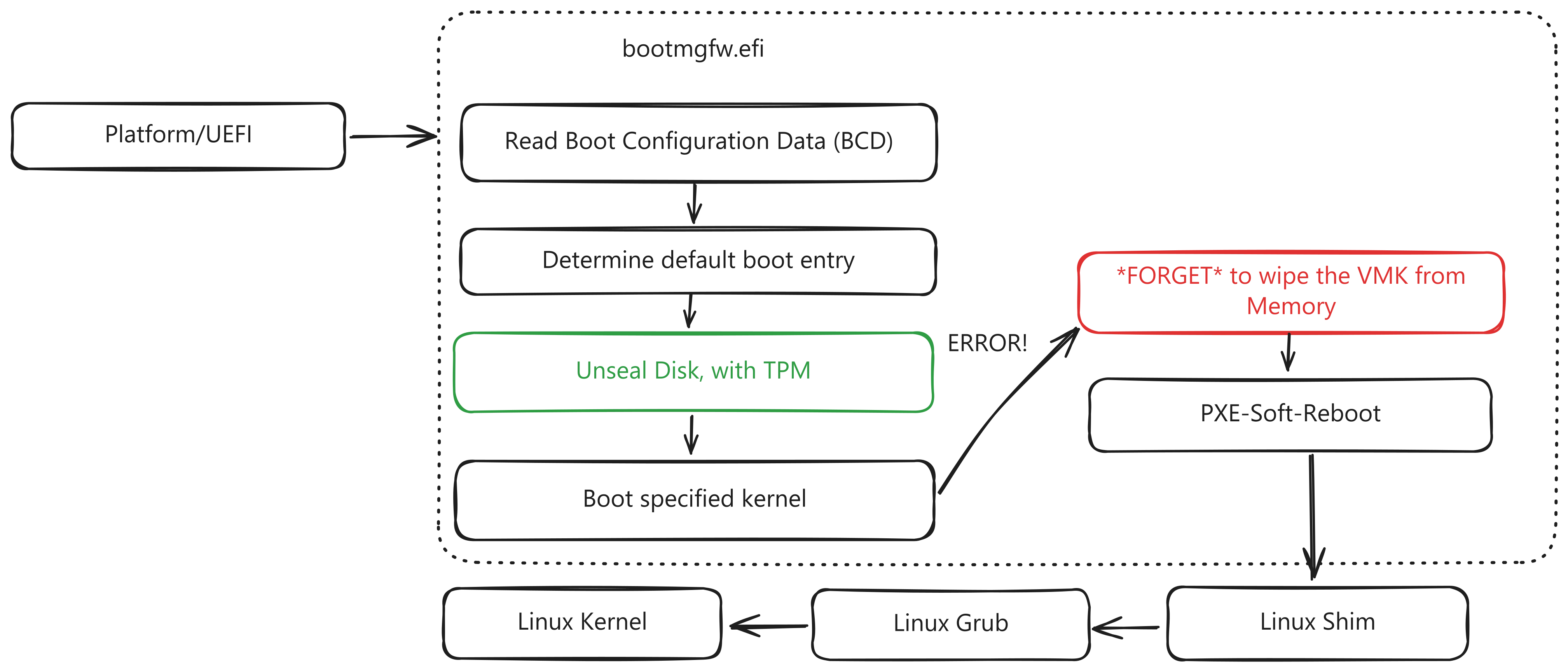
The bitpixie exploit underscores significant weaknesses in BitLocker’s reliance on Secure Boot and TPM for unattended decryption.
While these mechanisms are intended to simplify user experience by automatically unlocking drives during boot, they also create vulnerabilities when exploited.
Key concerns include:
- Widespread Applicability: The exploit affects all devices using BitLocker’s default “Device Encryption” mode, which is enabled by default on many Windows 11 systems.
- Ease of Execution: The attack requires only physical access to the device and basic tools like a keyboard and network connection.
- Persistent Risk: Despite patches issued by Microsoft in late 2022, attackers can still bypass protections through bootloader downgrades due to limitations in Secure Boot certificate revocation.
Mitigation Strategies
Microsoft has acknowledged the challenges in fully addressing this flaw. While newer bootloaders have fixed the issue, older versions remain exploitable due to Secure Boot’s inability to enforce strict downgrade protections universally. To mitigate risks, users are advised to implement additional security measures:
- Enable Pre-Boot Authentication: Configuring BitLocker with a pre-boot PIN ensures that encryption keys are not automatically released without user interaction.
- Apply KB5025885 Update: This update introduces additional Secure Boot certificates and revokes older ones, reducing exposure to downgrade attacks.
- Adjust PCR Configuration: Changing TPM Platform Configuration Registers (PCRs) to include additional measurements can prevent unauthorized key releases.
- Disable Network Boot Options: Restricting PXE boot capabilities in BIOS/UEFI settings can block one of the primary attack vectors.
The persistence of vulnerabilities like bitpixie highlights broader issues with hardware-based security implementations. Updating Secure Boot certificates across all devices is a slow process due to firmware limitations and dependency on manufacturers for updates.
Microsoft plans to introduce new Secure Boot certificates by 2026, but this leaves a significant window of vulnerability.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
