KEY FINDINGS
- A zero-day vulnerability in WinRAR has been exploited by hackers to target traders.
- The flaw lets hackers conceal malicious scripts within seemingly innocent archive files.
- The hackers have targeted specialized trading forums to distribute the malicious files.
- Once a victim opens the malicious file, the hackers can gain unauthorized access to their brokerage accounts.
- Approximately 130 traders have fallen victim to this scheme, and the financial losses are still being calculated.
Cybersecurity experts have unveiled a concerning situation involving a zero-day vulnerability in the widely-used archiving tool, WinRAR. This vulnerability, which was discovered by cybersecurity company Group-IB, has been skillfully exploited by cybercriminals to compromise the security of traders and potentially pilfer funds.
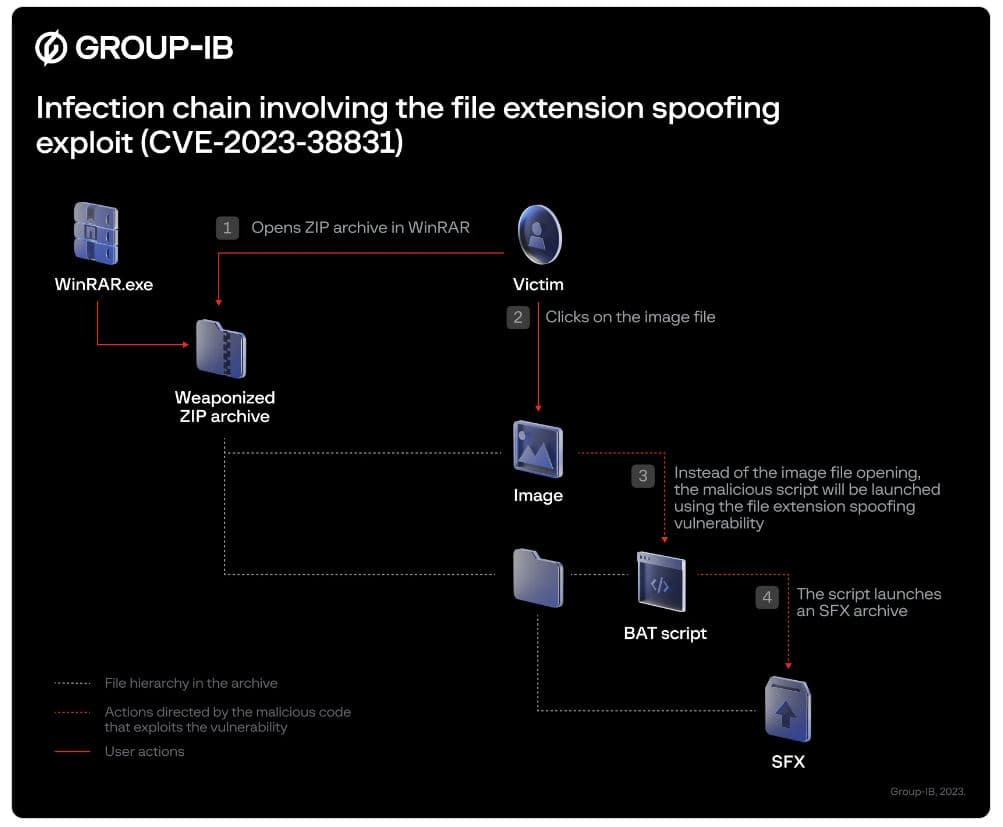
The vulnerability centers around the processing of ZIP file formats by WinRAR. Essentially, it allows hackers to conceal malicious scripts within seemingly innocent archive files, such as images or text documents, thus deceiving victims into unknowingly opening them. Group-IB first identified this 0-Day vulnerability in June, but its researchers suspect that hackers have been taking advantage of it since April.
The attackers’ modus operandi revolves around targeting specialized trading forums. These malicious ZIP archives, cleverly disguised, found their way onto at least eight public forums. Although Group-IB has refrained from disclosing the names of these forums, it has confirmed that they cover a spectrum of subjects, from trading and investments to cryptocurrency-related discussions.
One of these forums, after detecting the presence of malevolent files, issued a warning to its users and took measures to block the attackers’ accounts. Despite this, Group-IB noted that the hackers demonstrated the ability to reactivate disabled accounts, allowing them to continue spreading their damaging files either through threads or private messages.
The aftermath of an unwitting victim opening one of these files is dire. Hackers gain unauthorized access to the victim’s brokerage accounts, providing them with the means to execute illicit financial activities and potentially withdraw funds. At the time of Group-IB’s report, approximately 130 traders had fallen victim to this scheme. However, specific financial losses remain uncertain.
Remarkably, Group-IB managed to interview a victim who recounted an attempted money withdrawal by the hackers, which fortunately did not succeed. The identities of these cybercriminals remain shrouded in mystery. Nevertheless, Group-IB has identified the use of a Visual Basic trojan called DarkMe, which has previously been associated with the notorious “Evilnum” threat group.
Evilnum, also known as “TA4563,” has a track record of financially motivated activities primarily directed towards financial organizations and online trading platforms. While Group-IB recognized the DarkMe trojan, it was cautious in directly linking this campaign to the Evilnum group.
Taking responsible action, Group-IB promptly reported the vulnerability, and assigned CVE-2023-38831, to the makers of WinRAR, Rarlab. As a result, an updated version of WinRAR (version 6.23) was released on August 2nd, aimed at addressing this critical security concern.
WinRAR has been affected by vulnerabilities several times in the past. In October 2021, a remote code execution vulnerability was found in WinRAR’s free trial version 5.70, allowing attackers to execute arbitrary code on vulnerable systems. By manipulating a dialogue box, attackers could exploit the bug, potentially launching various attacks. The issue was addressed in WinRAR v. 6.02 released on June 14, 2021.
Further back in March 2019, it was discovered that WinRar has a code execution vulnerability lasting for 19 years. Over 100 exploits emerged, targeting users in the USA. Attackers could plant undetectable malware when users opened ZIP files, affecting all WinRar versions for the past 19 years. The malware activated on system reboot, with only a few antivirus programs detecting it. One exploit was disguised as a bootleg Ariana Grande album.
If you use WinRAR, update your software ASAP!
