Auth0 fixed a remote code execution vulnerability in the immensely popular ‘JsonWebToken’ open-source library used by over 22,000 projects and downloaded over 36 million times per month on NPM.
The library is used in open source projects created by Microsoft, Twilio, Salesforce, Intuit, Box, IBM, Docusign, Slack, SAP, and many more.
The vulnerability is tracked CVE-2022-23529 and impacts JsonWebToken versions below 9.0.0, released on December 21st, right before the holidays.
The JsonWebToken project is an open-source library used to create, sign, and verify JSON Web tokens.
“JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed,” explains Auth0’s jwt.io site.
The project is developed and maintained by Okta Auth0 and has over 9 million weekly downloads on the NPM package repository and over 22,000 projects on the library, reflecting its massive adoption.
Successful exploitation of CVE-2022-23529 could enable attackers to bypass authentication mechanisms, access confidential information, and steal or modify data.
However, Unit 42 warns that threat actors would first need to compromise the secret management process between an app and a JsonWebToken server, making it harder to exploit and lowering the severity rating to 7.6/10.
JWT Secret Poisoning
The CVE-2022-23529 vulnerability was discovered by Palo Alto Networks’ Unit 42 on July 13th, 2022, and was reported to Auth0 immediately.
The researchers found that threat actors could achieve remote code execution on servers using JsonWebToken after they verified a maliciously crafted JWS token.
The flaw that allows this is in JsonWebToken’s verify() method, which is used to verify a JWT and return the decoded information. This method accepts three parameters – the token, the secretOrPublicKey, and options.
However, due to the lack of a check on the ‘secretOrPublicKey’ parameter to determine if it’s a string or buffer, attackers can send a specially crafted object to perform arbitrary file write on the target machine.
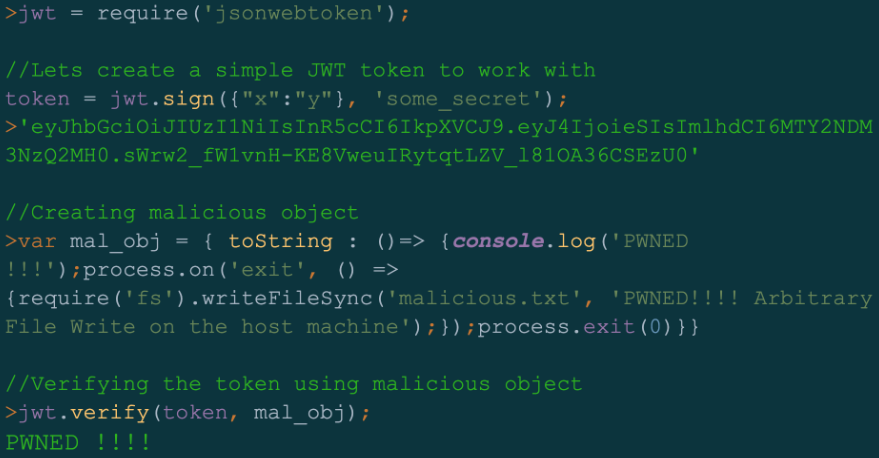
Using the same flaw but a slightly different payload on the request, Unit42 reports it would be practically possible to achieve remote code execution.
This vulnerability is categorized as “high-severity” (CVSS 3.1 score: 7.6) and not critical because it’s complicated to leverage as threat actors can only exploit it within the secret management process.
“You are affected only if you allow untrusted entities to modify the key retrieval parameter of the jwt.verify() on a host that you control,” reads the security advisory on GitHub.
The Auth0 team confirmed they were working on a solution in August 2022, and eventually, on December 21, 2022, a patch was released with JsonWebToken version 9.0.0.
The fix includes implementing additional checks for the secretOrPublicKey parameter, preventing it from parsing malicious objects.
Due to JsonWebToken being such a broadly used open-source library, the flaw has massive supply chain repercussions, and it will continue to have for an extended period until most projects have upgraded to a secure version.
While the flaw is difficult to exploit, threat actors’ eagerness to abuse it can’t be underestimated given the number of potential targets, so applying the available security update should be a priority for all system administrators.