Category: HackRead
BreachForums posts a PGP-signed message explaining the sudden April 2025 shutdown. Admins cite MyBB 0day vulnerability impacting the site, plan…
Windscribe, a globally used privacy-first VPN service, announced today that its founder, Yegor Sak, has been fully acquitted by a…
Toronto, Canada, April 28th, 2025, CyberNewsWire Dismissal affirms no-logs policy as a valid legal defense, avoiding a chilling effect on…
Darcula phishing platform adds AI to create multilingual scam pages easily. Netcraft warns of rising risks from Darcula-Suite upgrade. Cybersecurity…
Two individuals have been arrested in a joint international operation dismantling JokerOTP, a sophisticated phishing tool used to intercept 2FA…
Immersive security researchers discovered critical vulnerabilities in Planet Technology network management and switch products, allowing full device control. Learn about…
A critical vulnerability (CVE-2025-31324) in SAP NetWeaver Visual Composer puts systems at risk of full compromise. Learn how to check…
Software development is about to undergo a generative change. What this means is that AI (Artificial Intelligence) has the potential…
Enterprises using Commvault Innovation Release are urged to patch immediately against CVE-2025-34028. This critical flaw allows attackers to run code…
Interlock ransomware group claims it stole 20TB of sensitive patient data from DaVita Healthcare. While the group has leaked 1.5TB;…
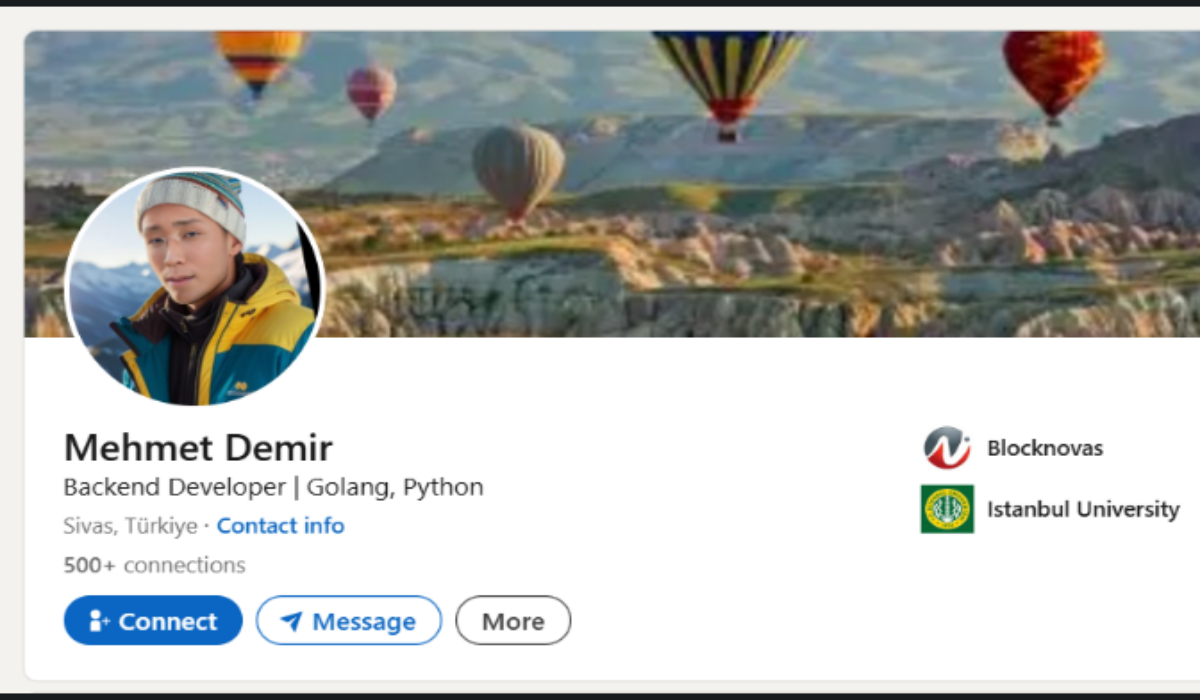
Silent Push reveals a complex scheme where North Korean hackers posed as crypto companies, using AI and fake job interviews…
XRP Ledger SDK hit by supply chain attack: Malicious NPM versions stole private keys; users urged to update xrpl package…