Category: HackRead
Blue Shield of California exposed the health data of 4.7 million members to Google for years due to a Google…
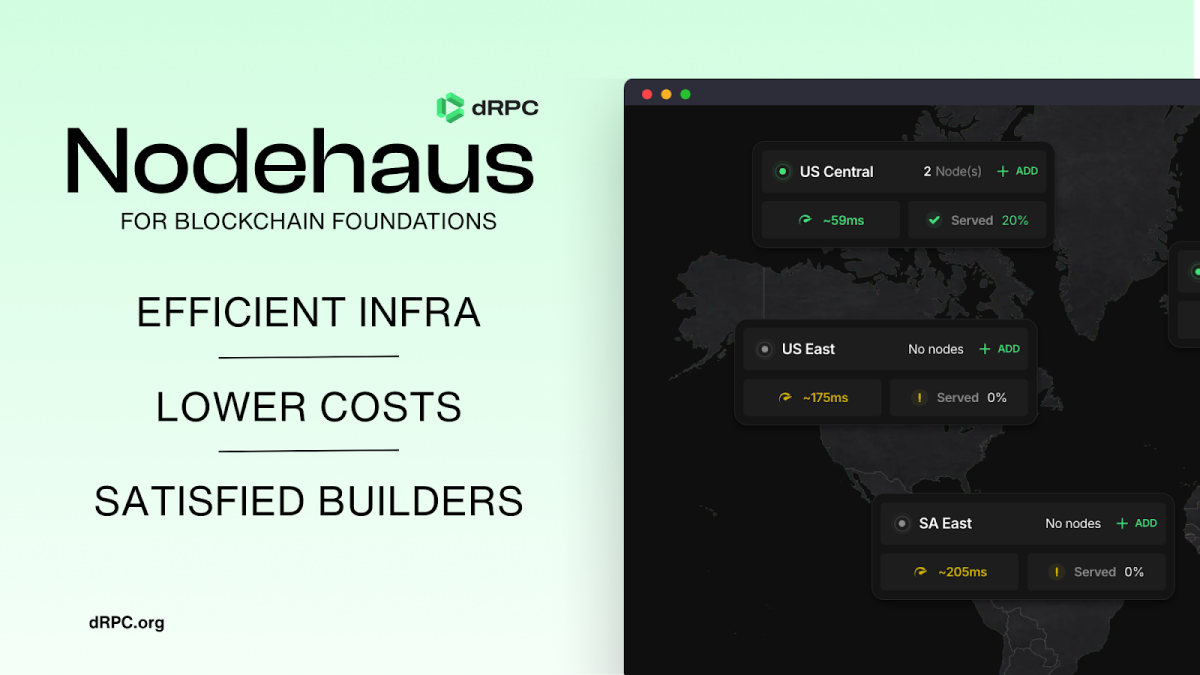
Blockchain infrastructure provider dRPC has announced the launch of a NodeHaus platform that enables chain foundations unprecedented control over their…
SessionShark phishing kit bypasses Office 365 MFA by stealing session tokens. Experts warn of real-time attacks via fake login pages…
With the rise of fintechs, accuracy alone isn’t enough, security and reliability are just as necessary. For fintech companies and…
Hackers in the Elusive Comet campaign exploit Zoom’s remote-control feature to steal cryptocurrency, and over $100K lost in social engineering…
If your iPhone feels cramped and storage alerts show up like it’s on a schedule, it’s probably time for a…
Lattica, an FHE-based platform enabling secure and private use of AI in the cloud, has emerged from stealth. The company…
AOA, DaVita, and Bell Ambulance hit by ransomware in 2025. Over 245K affected as hackers steal patient data, demand ransoms,…
Marks & Spencer (M&S) cyberattack disrupts contactless payments and Click & Collect; investigation launched as retailer apologises and claims to…
Fake Alpine Quest app laced with spyware was used to target Russian military Android devices, stealing location data, contacts, and…
An SSL.com vulnerability allowed attackers to issue valid SSL certificates for major domains by exploiting a bug in its email-based…
Terrance, United States / California, April 22nd, 2025, CyberNewsWire Joining Criminal IP at Booth S-634 | South Expo, Moscone Center…