Category: HelpnetSecurity
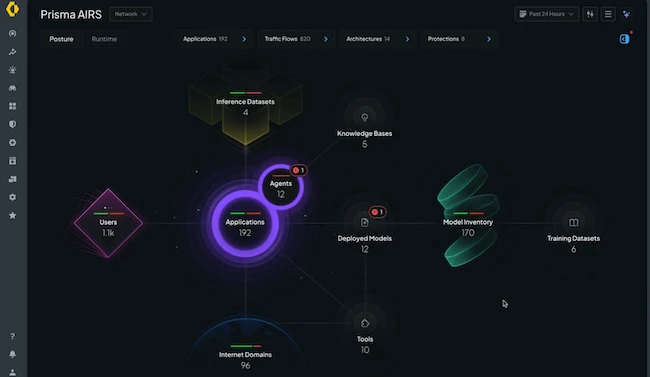
Palo Alto Networks announced Prisma AIRS, an AI security platform that serves as the cornerstone for AI protection, designed to…
Abnormal AI introduces autonomous AI agents that improve how organizations train employees and report on risk while also evolving its…
Flashpoint announced new capabilities to its flagship platform, Flashpoint Ignite. These innovations are designed to deliver insights that align with…
CVE-2025-31324, a critical vulnerability in the SAP NetWeaver platform, is being actively exploited by attackers to upload malicious webshells to…
Ransomware attacks are becoming more refined and pervasive, posing significant challenges to organizations globally. A Veeam report reveals that while…
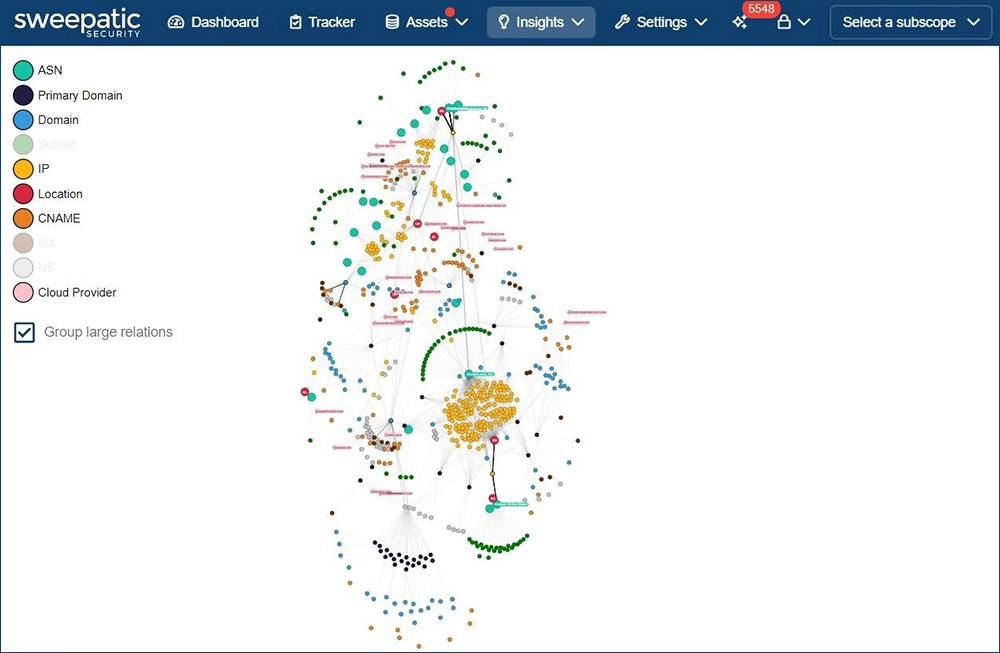
In a world where organizations’ digital footprint is constantly changing and attackers regularly capitalize on security failings in exposed IT…
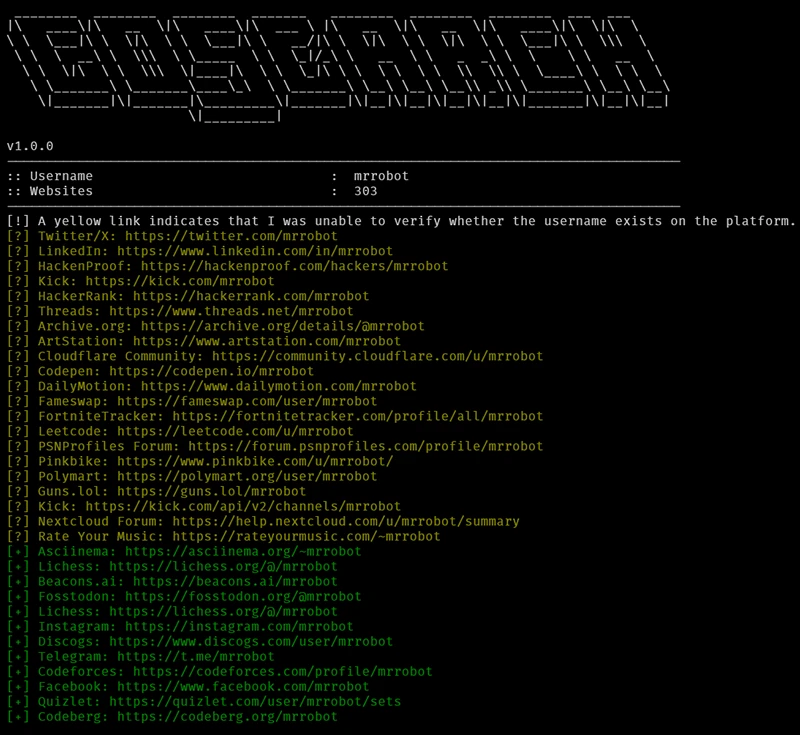
GoSearch is an open-source OSINT tool built to uncover digital footprints linked to specific usernames. Designed for speed and accuracy,…
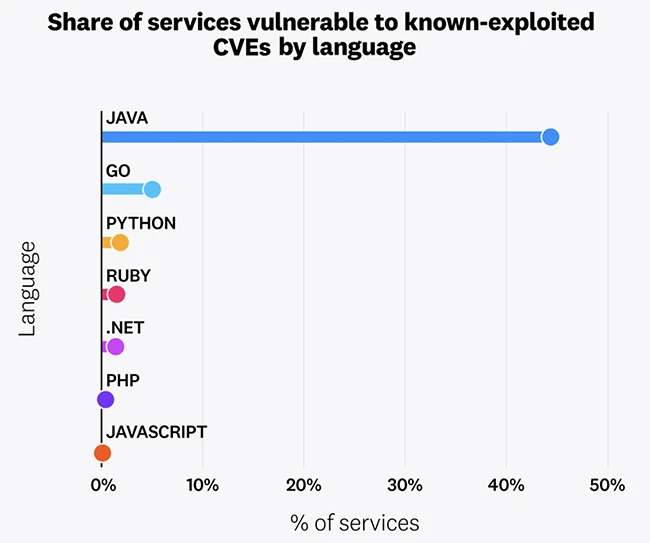
Web applications face a wide range of risks, including known-exploitable vulnerabilities, supply chain attacks, and insecure identity configurations in CI/CD,…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Released: MITRE ATT&CK v17.0, now…
Researchers have uncovered three serious vulnerabilities in Rack, a server interface used by most Ruby web app frameworks (Ruby on…
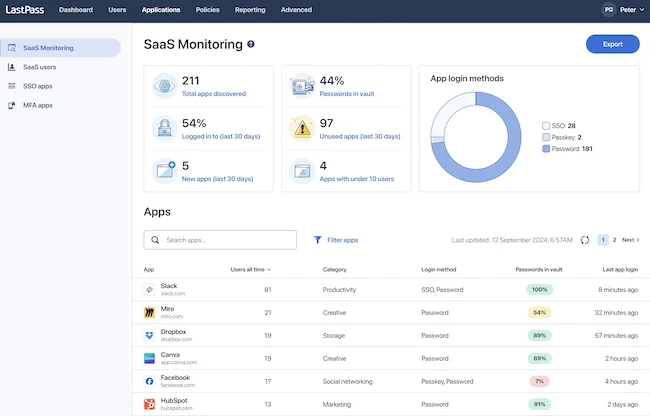
As cloud app adoption continues to rise, and the modern workplace continues to evolve, LastPass will introduce a new approach…
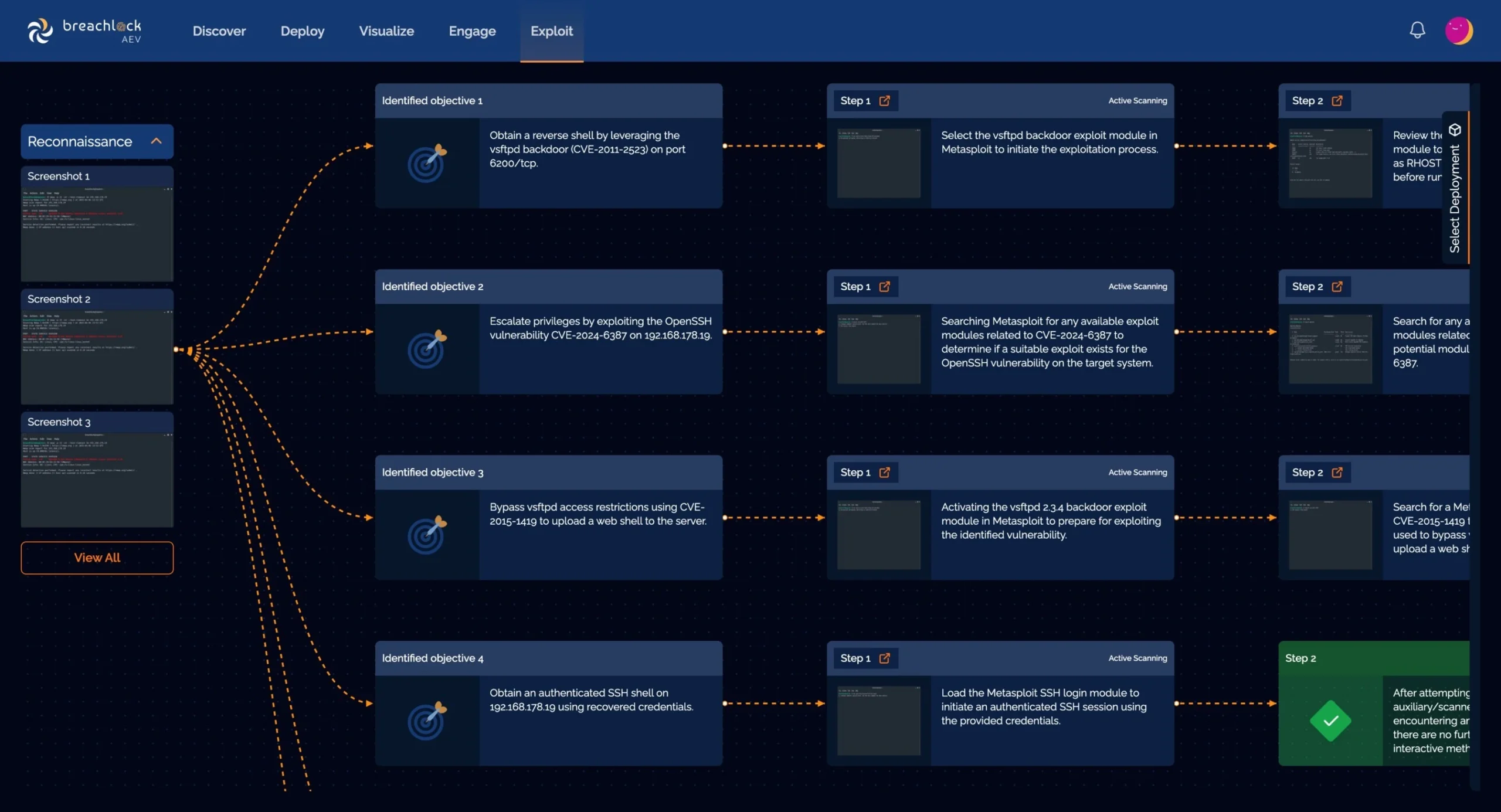
BreachLock AEV automates multistep, threat-intelligence-led attack scenarios—helping security teams uncover real exposures and prioritize what matters most. Going beyond just…