Category: Mix
Created/Updated: February 12, 2023 The killer app for AI right now is the universal “custom AI model”. Consume your whole…
The GitHub blog interviews me for their GitHub Action Hero series. GitHub recently interviewed me for their blog editorial entitled…
Nextcloud disclosed a bug submitted by ctulhu: https://hackerone.com/reports/1784681 – Bounty: $1500 Source link
Matt Atkinson | 21 January 2022 at 14:40 UTC When we launched Burp Collaborator back in 2015, PortSwigger deployed a…
chatGPT는 출시 이후 정말 많은 것들을 바꿨습니다. 물론 실제 일에 큰 영향을 준다기 보단 여러 AI가 사람들의 많은 관심을 받게되면서…
Live Hacking Events are the ultimate voyage for hackers selected to test their skills. This time our hackers had the…
TL/DR: Employees do their best work when they feel heard and valued. At Detectify, we truly understand our people—their skills,…
✅ Please subscribe to and give a 17-star review to this show on Apple Podcasts and Spotify. Thank you! SECURITY…
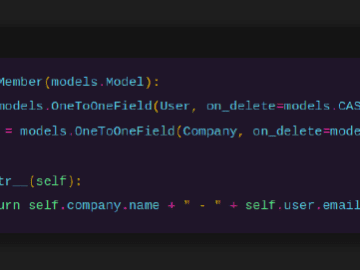
How to use Django’s views, models, and queries to build a better application. I like Django. It’s a well-considered and…
ownCloud disclosed a bug submitted by lukasreschke: https://hackerone.com/reports/1838674 – Bounty: $250 Source link
Emma Stocks | 11 March 2022 at 14:30 UTC For anyone who’s used the Web Security Academy before, you’ll be…
Blind XSS 도구 중 가장 유명하고 많은 기능을 담았던 XSSHunter가 올해까지만 운영되고 내년부터 서비스가 종료됩니다. 기업 내부에서는 보통 별도의 BXSS…