Category: Mix
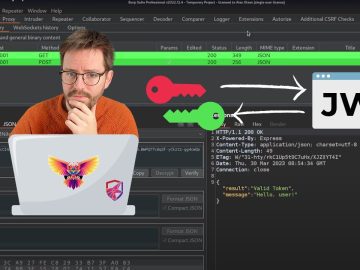
TomNomNom Demos a Ben Eater 8-bit CPU Emulator Source link
Hey there, I hope you’ve been doing well! Semgrep in EU I was a bit sleepy when I was finishing…
A Pentesters Introduction To The New OWASP API Top 10 – 2023 RC Source link
Kindred Group disclosed a bug submitted by sw33tlie: https://hackerone.com/reports/1632973 – Bounty: $5250 Source link
Attacking JWT – Header Injections Source link
Answering your questions about Superbacked Source link
Sometimes new features designed to generate revenue for a company can be rushed and sometimes not enough thought has gone…
Proof of concept Are you aware of any (private) bug bounty programs? I would love to get an invite. Please…
This is the only good CC0 image I could find If you’re not aware, I joined Dropbox’s security team last…
Q: PENTEST VS BUGBOUNTY? (Bounty Thursday’s – ON AIR) Source link
The Windows User Mode Exploit Development (EXP-301) course and the accompanying Offensive Security Exploit Developer (OSED) certification is the last…
Exploiting Markdown Syntax Markdown is wonderful. In fact, this blog post itself is written in Markdown. I don’t need to…
![[tl;dr sec] #168 – GCP and Azure Storage Threat Models, macOS Security, Red Team Resources [tl;dr sec] #168 - GCP and Azure Storage Threat Models, macOS Security, Red Team Resources](https://image.cybernoz.com/wp-content/uploads/2023/04/tldr-sec-168-GCP-and-Azure-Storage-Threat-Models-360x270.jpg)

![[www.32red.com] Reverse proxy misconfiguration leads to 1-click account takeover [www.32red.com] Reverse proxy misconfiguration leads to 1-click account takeover](https://image.cybernoz.com/wp-content/uploads/2023/04/www32redcom-Reverse-proxy-misconfiguration-leads-to-1-click-account-takeover.png)