Category: Mix
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…
Escalating Your Bugs With GDPR Impact Source link
How They Got Hacked Episode Fifty Two 52 Source link
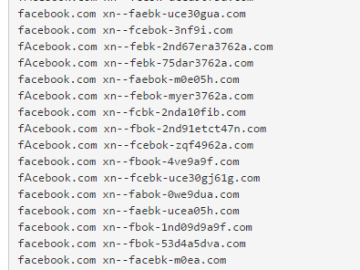
So we’re seeing homograph attacks again. Examples show how ‘apple.com’ and ‘epic.com’ can be mimicked by the use of Internationalized…
5 Discord servers for beginner hackers Source link
1 min read 💎 Cullinan :: Develop Crystal HAHWUL in cullinan develop crystal Source link
Hacking on Android With Gaurang Bhatnagar | Creator #InsecureShop | Security Engineer #vmware – 01 Source link
HackerOne Live Hacking Event Recap: Denver 2022 (H1-303) Source link
At HackerOne, we’re always looking for talented and dedicated individuals passionate about hacking and cybersecurity. That’s why we’re thrilled to…
Would you prefer a password-less login? #cybersecurity #shorts Source link
When it comes to bug bounty hunting and finding exciting areas to explore, it is vital to familiarise yourself with…
Tl;dr: We have updated our reward system to make it easier for you to know what you might earn with…