Category: Mix
Proof of concept Are you aware of any (private) bug bounty programs? I would love to get an invite. Please…
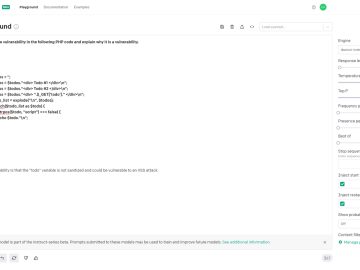
I used Google Drawings and there’s no shame in that This is a story about how I (re)discovered an exploitation…
Q: HOW do you get started in bug bounty?? How do you build your automation?! Source link
Note: This is the blogpost version of a talk I gave to the National University of Singapore Greyhats club. If…
September 22, 2015 · websec bruteforce As of late, a fair few companies and startups have been using dedicated URL…
In my free time when I’m not hunting for bugs in paid programs, I like to contribute a bit to…
As a preface, when I originally found this bug I was unfamiliar the class of “null byte buffer overflow” even…
Slides Supplemental The original (large) PowerPoint wih all embedded GIFs/Videos: https://1drv.ms/p/s!Aq5mEA03Lijrg9h-hsezBkUC5qwXag Source link
I have something that is worth sharing when you are testing for SSO system. Hope you can learn something new…
No BS Guide – ADVANCED BURP (FREE) TRICKS FOR BUG BOUNTY Source link
I was recently testing a checkout payment system. It was the type of setup where everything seemed to be locked…
Generating hacker art via AI has been a passion of mine for a few months. I was accepted into DALL·E…