Category: Mix
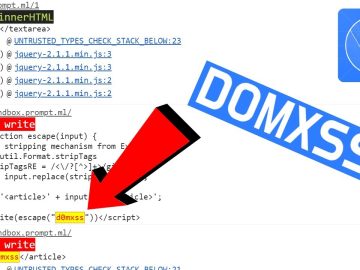
Finding DOMXSS with DevTools | Untrusted Types Chrome Extension Source link
TL;DR Sucuri is a self-proclaimed “most recommended website security service among web professionals” offering protection, monitoring and malware removal services….
Broken Access Control – Lab #9 UID controlled by param with data leakage in redirect | Long Version Source link
Why you should Close Your Files | bin 0x02 Source link
This week on a BugBounty program which I left aside I found my first SSRF, here is my writeup. Recon…
Sean Burns | 08 December 2022 at 10:45 UTC If you follow the Burp Suite roadmap, then you’ll know that…
The World’s 1st Open Source Bug Bounty Guide – Methodology, Tools, Resources by Mik317 (50+ CVEs) Source link
Cloud Hacking: The Basics Source link
Cyber Security Challenge Germany (2023) Source link
Maybe you heard about password cracking, but you don’t know what it’s all about and which risks it poses for…
You Can BUY This Hacked YouTube Channel Source link
TOOL TIME: Stream #4 Source link