The fake Ledger Live app on the Microsoft Store deceived users into downloading malware, which stole their Bitcoin and Ethereum funds.
Hackread.com has been actively following the cryptocurrency space as it has lately been a prominent target of scams and cyberattacks. Hackers are eyeing the crypto industry to steal valuable assets and even NFTs.
For this purpose, crooks devise clever tactics to lure unsuspecting users into giving away their funds and tokens. One such scam was recently reported by a pseudonymous on-chain detective and crypto sleuth, ZachXBT.
According to ZachXBT, a fake Ledger app was circulating on the Microsoft App Store. This fraudulent app masqueraded as the official Ledger Live app and tricked users into unwittingly downloading and installing malware stealing victims’ crypto funds and data.
ZachXBT’s analysis stressed the sophisticated nature of this scam, emphasizing the critical need for end-users to stay alert in protecting their cryptocurrency wallets. As of November 4th, scammers successfully collected roughly $588,000 in Bitcoin by hijacking users’ crypto wallets.
In a tweet, ZachXBT cautioned crypto users and investors with the following warning: “Community Alert: There is currently a fake @Ledger Live app on the official @Microsoft App Store which was resulted in 16.8+ BTC ($588K) stolen.”
However, on November 5th, ZachXBT received updated information from a victim, indicating a loss of $180,000 worth of ETH due to the fake Ledger app. This significantly increased the total lost payments to over $768,000.
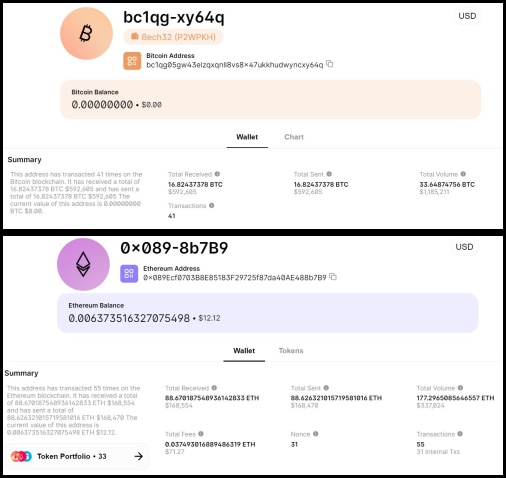
It is worth noting that in November 2023, a fake Ledger Live app was uploaded to the official Microsoft App Store that looked exactly like the original Ledger Live app. For your information, it is a popular software wallet designed to help users manage their crypto assets.
However, those who downloaded the fake version of this app ended up installing malware capable of stealing cryptocurrency by intercepting users’ recovery phrases. The attackers specifically target users who store their cryptocurrency in the Ledger hardware wallets to profit by stealing their assets.
The attackers have designed the counterfeit app quite cunningly, replicating the look and features of the authentic app, including identical logos and branding materials. They’ve gone as far as creating a fraudulent Ledger device pin verification process. This tricky similarity between the original and fake apps makes it challenging for users to differentiate between them.
The malware employs multiple methods to steal users’ recovery phrases. One involves exploiting a vulnerability within the Electron framework, which was utilized in developing the app. Recovery phrases, comprising 12 to 24 words, serve as a crucial means to regain access to a cryptocurrency wallet in case of theft or loss.
These are crucial bits of information as they enable access to manage cryptocurrency wallets on the app. When users enter these phrases into the fake app, the information is sent to the scammers. This allows scammers to hijack the victim’s crypto assets.
Nevertheless, Microsoft promptly detected and removed the fake Ledge Live app from their store. However, the damage to users is already done. The company is investigating how the fake Ledger app bypassed its app review process.
Remember that apps like Ledger, Trezor, or another hardware wallet will never ask users to enter their recovery phrases into their computers or phones. You should always enter the phrase in the hardware wallet to recover it.
RELATED NEWS
- Teen Hacks Ledger Hardware Cryptocurrency Wallet
- New DoubleFinger Malware Strikes Cryptocurrency Wallets
- All Ledger hardware wallets vulnerable to man in middle attack
- Ledger data breach: Hacker leaks stolen database on hacker forum
- Crypto wallet Ledger data breach; hackers steal 1m emails, other data
