Here’s an overview of some of last week’s most interesting news, articles, interviews and videos:
Visa fraud expert outlines the many faces of payment ecosystem fraud
In this Help Net Security interview, Michael Jabbara, the VP and Global Head of Fraud Services at Visa, delves into digital skimming attacks, highlighting their common causes, and provides insights into what measures merchants can take to prevent them.
Exchange Online will soon start blocking emails from old, vulnerable on-prem servers
Slowly but surely, Microsoft aims to make it impossible for unsupported and/or unpatched on-prem Microsoft Exchange servers to use the company’s Exchange Online hosted cloud service to deliver email.
Ransomware gangs are exploiting IBM Aspera Faspex RCE flaw (CVE-2022-47986)
Attackers are exploiting a critical vulnerability (CVE-2022-47986) in the IBM Aspera Faspex centralized file transfer solution to breach organizations.
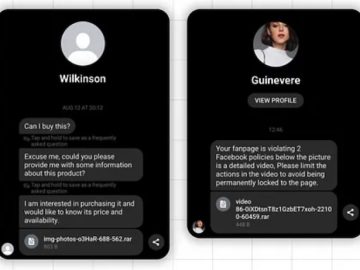
3CX customers targeted via trojanized desktop app
Suspected state-sponsored threat actors have trojanized the official Windows desktop app of the widely used 3CX softphone solution, a number of cybersecurity companies began warning on Wednesday.
Microsoft unveils AI-powered Security Copilot analysis tool
Microsoft has unveiled Security Copilot, an AI-powered analysis tool that aims to simplify, augment and accelerate security operations (SecOps) professionals’ work.
Apple backports fix for exploited WebKit bug to older iPhones, iPads (CVE-2023-23529)
Apple has released security updates for – pardon the pop-culture reference – everyhing everywhere all at once, and has fixed the WebKit vulnerability (CVE-2023-23529) exploited in the wild for users of older iPhones and iPads.
A bug revealed ChatGPT users’ chat history, personal and billing data
A vulnerability in the redis-py open-source library was at the root of last week’s ChatGPT data leak, OpenAI has confirmed.
BEC scammers are after physical goods, the FBI warns
BEC attacks are usually aimed at stealing money or valuable information, but the FBI warns that BEC scammers are increasingly trying to get their hands on physical goods such as construction materials, agricultural supplies, computer technology hardware, and solar energy products.
Understanding adversaries through dark web intelligence
93 percent of CISOs are concerned about dark web threats, and almost 72 percent of CISOs believe that intelligence on cybercriminals is “critical” to defend their organization and increase cybersecurity, according to Searchlight Cyber.
Protect your entire business with the right authentication method
In this Help Net Security interview, Tomasz Kowalski, CEO at Secfense emphasizes the significance of multi-factor authentication in the corporate landscape, highlights the use of microauthorizations to improve the security of protected applications, and much more.
Known unknowns: Refining your approach to uncategorized web traffic
Cybersecurity is such a complex field that even the best-trained, best-equipped, and most experienced security managers will sometimes struggle to decide which of several paths to take.
Prioritizing data security amid workforce disruptions
In this Help Net Security video, Chris Wey, President of Data Modernization at Rocket Software, discusses the risks organizations face and the steps they can take to mitigate disruption.
Microsoft announces Microsoft Incident Response Retainer
Microsoft has introduced Microsoft Incident Response Retainer, allowing customers to pre-pay and count on help from Microsoft incident responders before, during and after a cybersecurity crisis.
What you need before the next vulnerability hits
To prevent bad actors exploiting vulnerabilities, you must take action to reduce or eliminate security risks.
Overcoming obstacles to introduce zero-trust security in established systems
In this Help Net Security interview, Michal Cizek, CEO at GoodAccess, discusses the crucial balance between leveraging distributed resources and maintaining top-notch security measures.
The era of passive cybersecurity awareness training is over
Despite increased emphasis on cybersecurity from authorities and high-profile breaches, critical gaps in vulnerability management within organizations are being overlooked by executive leadership teams, according to Action1.
Running a security program before your first security hire
In this Help Net Security video, Matt Spitz, Head of Engineering at Vanta, talks about pragmatic security and illustrates what a small company with limited resources needs to do to lay the groundwork for effective protection.
Ignoring network automation is a ticking time bomb for security
Network and security device updates are crucial, but they are time-consuming and prone to human error when managed manually.
How cybersecurity decision-makers perceive cyber resilience
In this Help Net Security video, Max Vetter, VP of Cyber at Immersive Labs, discusses the growing pressure on cybersecurity teams to prove their readiness for new and emerging threats.
Europol details ChatGPT’s potential for criminal abuse
With the increased public interest in ChatGPT, the Europol Innovation Lab took the matter seriously and conducted a series of workshops involving subject matter experts from various departments of Europol.
The rise of biometrics and decentralized identity is a game-changer for identity verification
In this Help Net Security video, Jenn Markey, VP of Payments and Identities at Entrust, talks about how biometrics, hybrid solutions, and decentralized identity are transforming the industry and the future of identity verification.
Balancing security risks and innovation potential of shadow IT teams
Shadow IT teams, also known as rogue IT teams, have grown in popularity in recent years due to the rise of cloud-based apps and remote work.
Leveraging network automation to enhance network security
In this Help Net Security video, Josh Stephens, CTO of BackBox, shares his thoughts on how network teams at organizations can be proactive and strategic in backing up network and security device configurations.
Dangerous misconceptions about emerging cyber threats
Organizations are leaving common attack paths exposed in their quest to combat emergent threats, according to Cymulate.
New York law firm gets fined $200k for failing to protect health data
A New York law firm has agreed to pay $200,000 in penalties to the state because it failed to protect the private and electronic health information of approximately 114,000 patients.
What the food and building industry can teach us about securing embedded systems
Currently the SVP of Security Technology and Innovation at Cybellum, the Left to Our Own Devices podcast invited Adam Boulton to share his experience and his tips on building a product security strategy.
The best defense against cyber threats for lean security teams
The National Institute of Standards and Technology Cyber Security Framework (NIST CSF) is one of the most respected and widely used standards in the world.
New infosec products of the week: March 31, 2023
Here’s a look at the most interesting products from the past week, featuring releases from BreachLock, HackNotice, LOKKER, Nile, and Tausight.