Category: Mix
facts: Bug Bounty hunters has made ridiculous amounts of $$ from known DNS techniques.. Source link
DOM-based Cross-site scripting (XSS) vulnerabilities rank as one of my favourite vulnerabilities to exploit. It’s a bit like solving a…
Modern development and infrastructure management practices are fast paced and constantly evolving. In the race to innovate and expand, new…
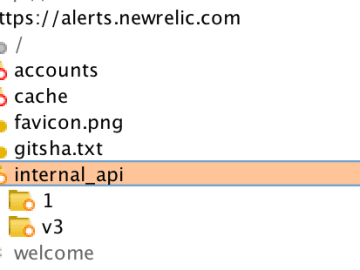
I recently found a nice insecure direct object reference (IDOR) in New Relic which allowed me to pull data from…
Ever since I was a kid I was never good at doing schoolwork. I had envied everyone that seemed to…
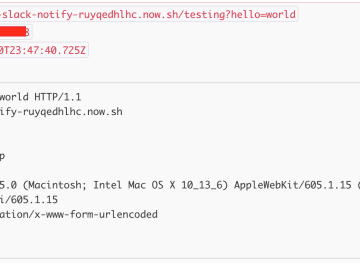
Serverless is awesome and I can’t believe this stuff is free. I’m releasing some serverless functions that I’ve developed over…
I don’t have automation in my bug hunting, no sqlmap, sublist3r or jsparser. I tried, they just don’t work out…
Bug Bounties Using only Burp & Browser – 30 DAY RESULTS (UNEXPECTED) Source link
“If you are doing a task more than twice? Then, automate it!” I hear that phrase all the time, but…
Hacking on a plane, by Midjourney AI This is a short write-up about how I could have accessed the personal…
I hacked Outlook and could’ve read all of your EMAILS! Source link
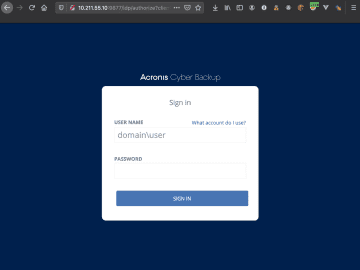
CVE-2020-16171: Exploiting Acronis Cyber Backup for Fun and Emails You have probably read one or more blog posts about SSRFs,…



![[Uber] redirect_uri is difficult to do it right – Ron Chan [Uber] redirect_uri is difficult to do it right – Ron Chan](https://cdn.cybernoz.com/wp-content/uploads/2023/03/Uber-redirect_uri-is-difficult-to-do-it-right-–-Ron.jpg)