Category: Mix
Slides Supplemental Serverless Toolkit available here: https://github.com/ropnop/serverless_toolkit Source link
From time to time we see postMessage bug in H1 hacktivity, some write ups mentioning the word postMessage, but do…
INTERVIEW WITH @_BASE_64 : 19 Y/o | TOP 150 WORLDWIDE on H1 | METHODOLOGY, MINDSET & MORE… Source link
I quite enjoy external Pentest, especially when the scope is large. There has been some really interesting stuff I have…
As a hacker and bug bounty hunter, I spend a lot of my time optimizing and improving. So, as a…
Cookie Tossing Source link
This is the story about how I’ve chained a seemingly uninteresting request smuggling vulnerability with an even more uninteresting header-based…
Broken Access Control – Lab #8 UID controlled by parameter, with unpredictable UIDs | Short Version Source link
When You Use One Wrong Javascript Module Source link
I originally wanted to name this article “The RCE that everyone missed”, but since it was too “clickbait”, this is…
Emma Stocks | 27 January 2023 at 11:11 UTC We launched the Burp Suite Certified Practitioner (BSCP) certification at the…
Dear Readers, once in a while I enjoy blogging about things unrelated to bug bounties. And so, as it happens,…






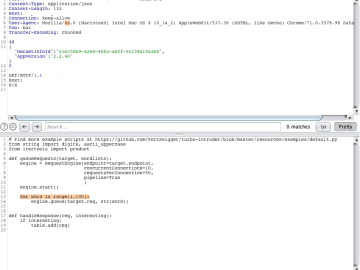

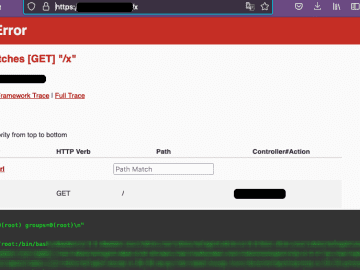

![[Research] Phishermans Friend – Getting control over a phishing backend [Research] Phishermans Friend – Getting control over a phishing backend](https://cdn.cybernoz.com/wp-content/uploads/2023/03/Research-phishermans-friend--getting-control-over-a-phishing-backend-360x270-1.jpg)