Jan 09, 2023Ravie LakshmananNetwork Security / Supply Chain In yet another campaign targeting the Python Package Index (PyPI) repository, six…
Online markets selling drugs and other illegal substances on the dark web have started to use custom Android apps for…
The Meta-owned firm also stated in its blog post that connecting via a proxy will maintain the “high level of…
[ This article was originally published here ] As practitioners know all too well, it is paramount to remain up…
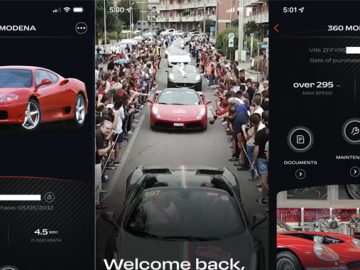
Jan 09, 2023Ravie LakshmananAutomotive Security Multiple bugs affecting millions of vehicles from 16 different manufacturers could be abused to unlock,…
Cloud Security , Security Operations , Video Troy Leach on Cloud Security Skills, Challenges and Trends Anna Delaney (annamadeline) •…
Auth0 fixed a remote code execution vulnerability in the immensely popular ‘JsonWebToken’ open-source library used by over 22,000 projects and…
As a startup owner, it can sometimes feel impossible to get the attention of your target audience, especially in a…
The world of eLearning has seen tremendous growth in recent years, with more and more organizations turning to online platforms…
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
The new trust Business has always relied upon a foundation of trust. Before we did business we looked our potential…
Jan 09, 2023Ravie LakshmananKubernetes / Cryptojacking The threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and…