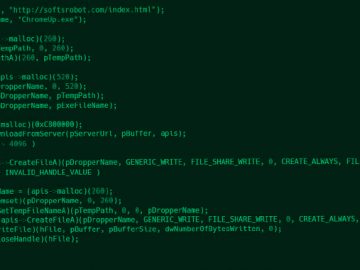
Open Source Hacking Lab | Guide on File Inclusion Vulnerability and Path Traversal Attack in PHP Source link
Mar 15, 2023Ravie LakshmananServer Security / Cryptocurrency Cybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint…
The Phoenix hacker group, which is a part of the pro-Russia hacker group Killnet has claimed to have launched several…
Does Cybersecurity Require Programming? Source link
The cybersecurity analysts at cloudSEK recently asserted that monthly YouTube videos containing links to stealer malware, such as Vidar, RedLine,…
Mar 15, 2023Ravie LakshmananCyber Attack / Data Safety A cyberespionage actor known as Tick has been attributed with high confidence…
ATLANTA, March 15, 2023: Cyble, the Y Combinator-backed leader in AI-powered global cyber threat intelligence, today announced that Mahesh Vandi Chalil, former…
Corporate leaders, managers, HR and IT need to keep teams of people working at headquarters, at customer locations, remotely or…
UMBC Cyberdawgs CTF: The Hacker One Source link
There is a consensus among MSPs and MSSPs that vCISO services pose an excellent opportunity for a new revenue stream,…
The Silicon Valley Bank (SVB) collapse on March 10, 2023, has triggered heightened cybersecurity concerns due to the emergence of…
Bypassing a WAF by Finding the Origin IP Source link