Cloud service providers fundamentally changed the way we do business in 2023. Office 365 is one of the most popular cloud-based services catering to online businesses.
The suite’s advanced collaboration and productivity features make it a go-to service for businesses that want to transition digitally. But digital transformation is anything but smooth sailing.
.png
)
Despite more businesses adopting these technologies, the increased adoption paints a target on their back. Namely, hackers and threat actors understand the value of Office 365 and similar services.
Considering these solutions can hold insurmountable amounts of data, it becomes a priority to enhance Office 365 protection.
But is Microsoft capable of protecting sensitive data, and what can we do to make our environments more secure? This article will discuss the ten experts’ best practices to enhance Office 365 security and promote a safe and secure environment. Let’s begin.
Enable MFA (Multi-Factor Authentication)
Office 365 Security
One of the most effective ways to strengthen Office 365 security is by enabling Multi-Factor Authentication. MFA improves the suite’s security by requesting additional verification from users.
The verification methods can be a one-time passcode from an authentication app, a fingerprint scan, or an email code.
So in case a threat actor has managed to compromise employees’ credentials, they would still require additional verification for full access to Office 365.
As a result, MFA is one of the more reliable security features in Office 365, capable of preventing unauthorized access to the suite and improving your organization’s security posture.
Enable Data Loss Prevention (DLP) Policies
.webp)
DLP is another potent security feature found in the Security and Compliance Center. With DLP, we can create policies to allow organizations to identify and protect sensitive information within Office 365.
The way DLP works is through rules and conditions. Administrators can define rules and conditions to detect and prevent the unauthorized sharing or leakage of confidential data, such as financial records, personally identifiable information (PII), or intellectual property.
By implementing data loss prevention policies, businesses ensure compliance with data protection regulations and minimize the risk of data breaches. For example, suppose an employee is sending financial records through email.
In that case, a DLP policy can alert them of potentially sending confidential data and, in many cases, prevent them from doing so in the first place.
Utilize Advanced Threat Protection (ATP)
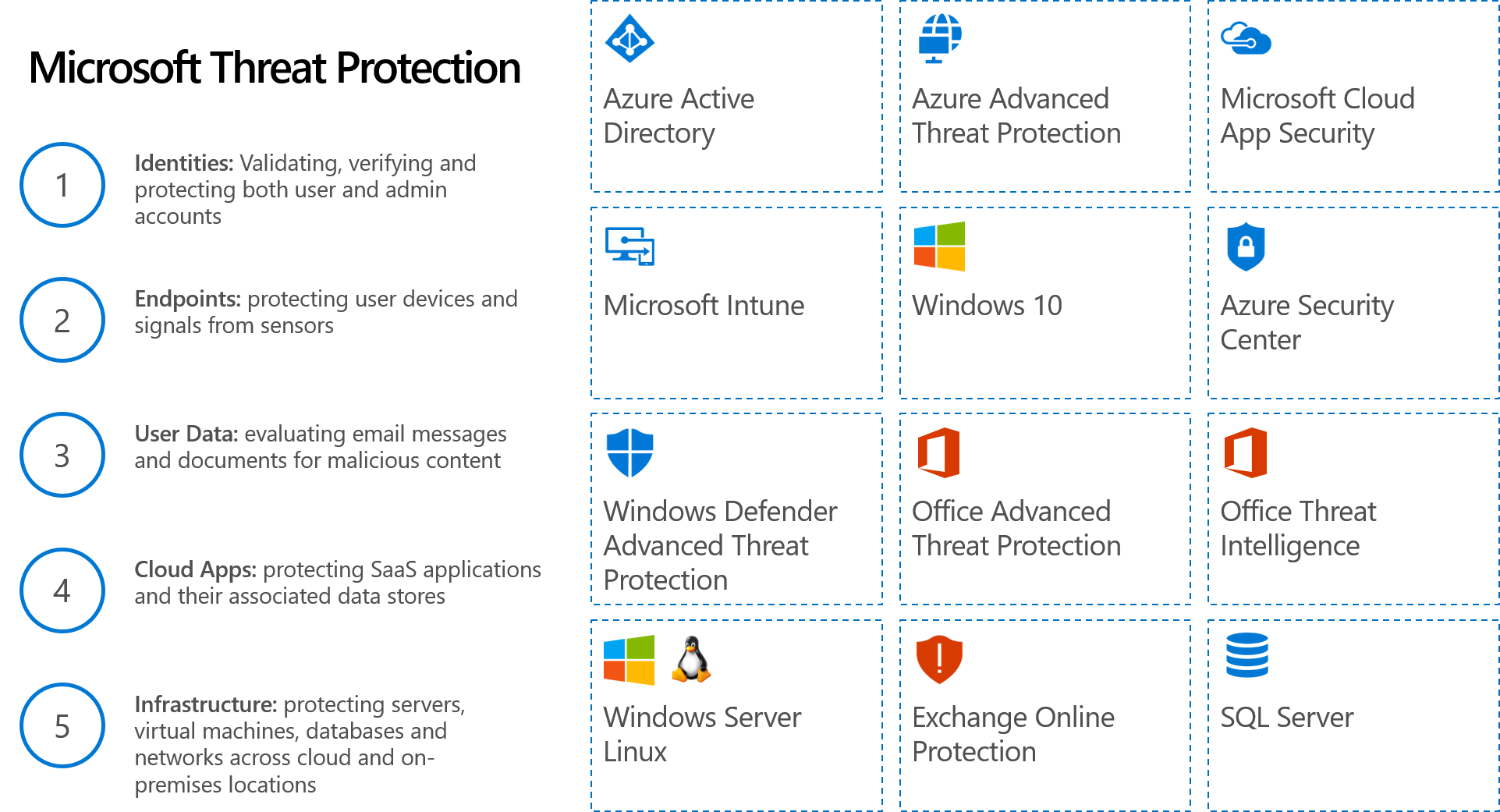
ATP is a standout security feature capable of protecting the suite against all kinds of malware and threats sent primarily through email. Advanced threat protection is part of Microsoft Defender for Office 365.
The feature aims to strengthen email accounts, defend against emerging phishing attacks and advanced threats, and utilize artificial intelligence and machine learning to stop email-based security threats. In addition, ATP is capable of stopping zero-day exploits.
With ATP, businesses use industry-leading AI that scans attachments, documents, and links to identify threats.
Enabling ATP can significantly enhance your defense against sophisticated cyber attacks, safeguarding your organization’s sensitive information.
Regularly Update and Patch Office 365

When it comes to utilizing the best practices and measures for Office 365 protection, we cannot forget the importance of updating the suite with the latest security patches.
Microsoft regularly releases updates that address vulnerabilities and strengthen the platform’s overall security.
Security updates are essential for a number of reasons, including anti-phishing protection, preventing security exploits from one of the many applications, and enhancing advanced protection.
As a general rule, tenant accounts should have auto-updating enabled. However, it is not enabled by default.
Admin accounts can go into each tenant and enable auto-updating to maintain a secure environment free of potential security exploits.
Educate Users on Security Awareness
Despite the numerous features available to you in Office 365, cyber threats can bypass your security measures and compromise your organization’s sensitive data.
Moreover, no matter how much we try, hackers find all kinds of ways to gain access to the suite and wreak havoc. In most cases, this is down to human error.
Human error remains a significant factor in security breaches. Without them even knowing, your employees are active targets for hackers and threat actors.
Therefore, educating them about security best practices and raising awareness about potential threats becomes essential.
You can conduct regular training sessions that cover topics such as recognizing phishing attempts and stopping phishing attacks, creating strong passwords, and exercising caution while sharing sensitive information.
Empowering your users with knowledge will help create a security-conscious culture within your organization.
Monitor and Analyze User Activities
Office 365 security allows you to implement robust monitoring and auditing capabilities. With the Unified Audit log feature, you can track user activities, identify suspicious behavior, and detect potential security breaches.
The monitoring features allow you to identify unauthorized login attempts, file access, and other user actions to respond to any anomalies and mitigate security risks effectively.
Employ Data Encryption

Encryption is yet another data protection and security feature and a critical aspect of the Office 365 suite. Encryption allows you to protect sensitive data by encrypting it both at rest and in transit.
Office 365 provides two encryption options that can be enabled to protect your data from unauthorized access.
Lastly, encryption works on emails, documents, and other files, adding an extra layer of security, even if they fall into the wrong hands.
Regularly Back up Office 365 Data
While Office 365 comes with built-in data redundancy features, it is still essential to have a comprehensive backup strategy in place.
Accidental deletion, retention policy gaps, malicious actions, and outages can result in costly data loss events.
Therefore, implementing a backup solution that periodically backs up your Office 365 data to an external location will prevent critical data loss and ensure you have access to the latest version.
Restrict External Sharing and Access
Review and configure external sharing settings in Office 365 to ensure that sensitive data is not inadvertently exposed to unauthorized users.
Utilize features like Azure Active Directory (Azure AD) Conditional Access and go into your Exchange Online configuration settings to control access to Office 365 services based on specific criteria, such as user location, device compliance, or IP address.
With these features, you create rules and external access policies to protect your Microsoft Office environment and ensure people only the access they need to perform their tasks.
Conduct Regular Security Assessments
Lastly, you can never be sure your Microsoft environment is fully safe if you don’t perform regular security assessments.
Through security assessments and penetration testing, we can identify vulnerabilities and weaknesses in Office 365 and take the appropriate actions to address them.
Conclusion
Enhancing Office 365 security is crucial for organizations to mitigate the ever-evolving cyber threats that target cloud environments. Fortunately, the Office 365 suite comes with advanced and robust security features.
But it requires an understanding of these features to ensure they’re implemented accordingly. These ten experts’ best practices and tips will help you do just that.
