149 million stolen usernames and passwords for TikTok, Disney+, Netflix, Roblox, and crypto wallets were found online without any security authentication. Learn about the latest massive data leak and how to secure your digital identity today.
A massive database containing over 149 million stolen usernames and passwords has been taken offline after sitting wide open on the internet for weeks. Cybersecurity researcher Jeremiah Fowler discovered the exposed cache, noting that the exposure “highlights the global threat” of data theft because it allowed anyone with a web browser to view and search the records. This research was published by ExpressVPN and shared with Hackread.com.
A One-Stop Shop for Hackers
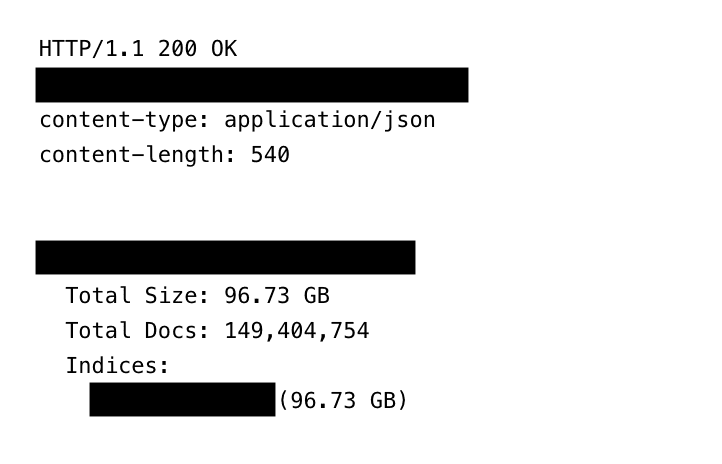
The database, totalling 96 GB, was not just a static pile of old leaks. While Fowler spent nearly a month trying to alert the hosting provider, he noticed the collection was actually growing in real-time. The sheer variety of the stolen data is what makes this discovery so troubling. The records included accounts for:
- Social Media: Facebook (17M logins), Instagram, TikTok, and X.
- Streaming and Games: 3.4M Netflix logins, plus HBOmax, Disney+, and Roblox.
- Financials: Banking portals, credit card accounts, and 420,000 Binance crypto logins.
- Sensitive Sites: Dating apps and OnlyFans accounts, affecting both creators and customers.
The database contained 48 million Gmail accounts, roughly 4 million Yahoo logins, 1.5 million for Microsoft Outlook, and 900,000 for Apple’s iCloud. Even more concerning, it contained login details for government (.gov) domains from multiple countries. Fowler noted that even limited access to these accounts could allow hackers to impersonate officials or slip into secure government networks.
The Mystery of the Infostealer
How did all this data get there? As per Fowler’s research, the culprits likely used infostealer malware, a software that infects your computer or phone and records everything you type. But this was different from previous leaks because this specific operation appeared much more organised than usual.
Such as, the system used a reversed labelling method to sort data by the specific device and the website it came from. This must’ve made it easy for criminals to search victims while helping the malware dodge basic security scans. Furthermore, every entry had a unique fingerprint (or hash) to ensure no duplicates were stored.
Morey Haber, Chief Security Advisor at BeyondTrust commented on this, stating, “Authentication best practices always recommend: unique passwords for every site, never reusing passwords, enabling MFA or at least 2FA for website (and avoiding 1FA whenever possible), using a monitoring service like LegalShield, LifeLock, etc. or even the built in password security detection built into Apple IOS to determine if credentials are exposed on the dark web so users can change their passwords – and lastly, never accepting 2FA/MFA notifications unless you have initiated them.“
“As for the source of the data, infostealing malware can come from a variety of sources, like sideloading applications, jailbreaking, vulnerabilities/exploits, etc. Users should only use verified sources for applications (AppStore) and on applicable devices, ensuring they are running anti-virus solutions with the latest updates,” Haber warned.
A Month of Exposure
Speed, as we know it, is critical when securing a leak, but Fowler hit a wall during the reporting process. It took a month of “multiple attempts” before the hosting provider finally suspended the server. However, the damage may already be done. Since the records included exact login web addresses (URLs), it became incredibly easy for criminals to automate attacks.
To stay safe, the best defence is using a password manager and enabling two-factor authentication. Keeping your operating system updated is also a vital step in patching the holes that malware uses to get inside.
