By Sheetal Pansare, President & Global CEO of Futurism Technologies
Imagine you are a CEO waking up to a Class-action lawsuit simply because your IT department failed to comply with the necessary security compliances or worse, they didn’t back up mission-critical business data exposing sensitive customer information to potential hackers.
Yes! Data breaches make hot news headlines almost every day! Many things can go haywire when it comes to containing a data breach: from outages to unplanned downtime and timely detection of an intrusion attempt to name few.
Did you know?
CEO of Optus (a leading Telco in Australia) took full accountability for a brutal data breach that jeopardized sensitive data of more than 9 million customers.
Now this can be hard for organizations that are led by leaders who undermine the importance of creating as well as maintaining a strong line of cyber defense. This is what happened with a leading French hospital last year, which was left crippled by a Ransomware attack causing abrupt downtime of its critical systems forcing the healthcare provider to shift patients elsewhere while exposing sensitive patient data of millions.
Source: PwC
Why does cyber security need to be a priority for every CEO?
Cyber criminals see a feast of opportunities in today’s highly connected and digital-first economy. They are unleashing coming-of-age attack tactics on security and network systems on organizations. This is why CEOs ought to reevaluate every aspect of their security posture including people, process and technology.
Good news is that you as a ‘CEO’ can save your company from such unfortunate mishaps. Just knowing the fundamental security practices and concepts can help you make the right decision for your company.
Here’s what you as a ‘CEO’ ought to know about cybersecurity to avoid becoming the next cyberattack cover page story.
- Good Cyber Hygiene Pays off
Always make sure that your company follows good IT and cyber hygiene practice to keep all your systems and data safe. Also, remember that when an IT system reaches its ‘end-of-life’, its manufacturer or vendor no longer supports them thus, leaving them vulnerable to attacks. So patch now or pay later!
Did you know?
The infamous ‘Log4j Vulnerability’ has been giving sleepless nights to IT and security experts worldwide since its discovery (2021).
- Don’t ignore Endpoint Security
When IT systems are removed or shut down from a network, they still tend to have personal information stored in them. To remove the data, these systems need to be ‘wiped’ before being discarded. This is where it counts to have a strong and unified endpoint management and extended detection and response (XDR) system in place.
Understand that any organization irrespective of its size is prone to cyber attacks. This is why you as a ‘CEO’ ought to assess the types of cyber risks your company faces and how those threats would impact your organization. CEOs when better understand these risks, can better tackle the impact and mitigate risks.
- Security is not IT Issue Alone!
It is important for CEOS to understand that cyber security isn’t just an IT issue, but a business issue. In fact, it is everyone’s responsibility in an organization. While your security/IT teams hustle to up your guard against potential attacks, it is the responsibility of every stakeholder in the company to stay vigilant. If a company’s information is compromised post an attack, it could lose customer trust affecting the brand’s reputation followed by a legal suit. This is why it counts to have a strong managed identity and access management solution in place, which will not only help deploy the right layers of security, but will also bring in intelligent and context -based access decisions coupled with risk-based authentication.
Did you know?
Over 70% of enterprise data breaches involve insider attacks often executed by rogue or disgruntled employees.
- Insider Threat Detection is a Must
If your security or IT teams work separate from remote locations, make sure that they have frameworks and/or protocols in place ensuring secure access to mission-critical company database and systems. Having a powerful insider threat detection system can save the day here. It is advisable to seek expert help from a managed security services partner that will act as an extended arm to your security team taking over all the critical security tasks and operations.
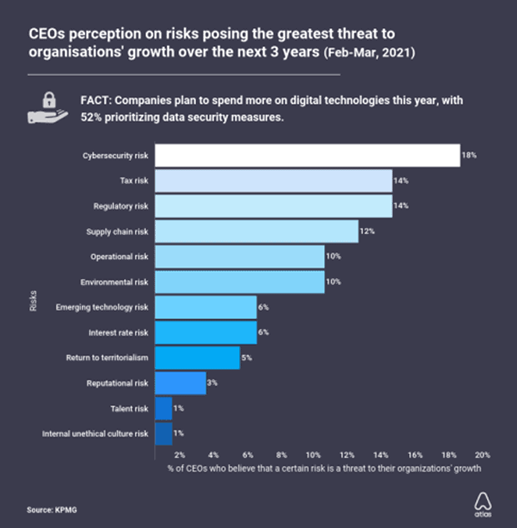
Source: Loss Prevention Magazine | KPMG
Did you know?
According to Verizon’s 2022 Data Breach Report, four out of five breaches occur due to human based vulnerabilities and/or errors.
- Cyber Awareness isn’t just a One-Time Activity!
Your employees are the ones that attackers target, manipulate and social engineer to coerce into your databases or systems. The single and most important factor in cybersecurity is the human factor. Yes! Even the most advanced security mechanism cannot protect your company if your employees fall for social engineering attack tactics. Educate your employees about the various types of attack tactics including or spear-phishing attacks, callback phishing attacks and new strands of Ransomware. Cyber awareness training needs to be a continuous process.
- Have Complete Visibility of your IT Environment
You simply can’t protect an attack if you don’t know that there exists a threat. Create an up-to-date list of your physical as well as digital assets. This is the key towards achieving end-to-end security. Understand the various types of threats and work with your IT/Security people in creating and deploying a solid incident response mechanism along with a disaster recovery plan.

Source: IBM
Make sure to bridge any communication gap between you and your IT/Security team. For instance, many small organizations such as rural or community hospitals often lack the required expertise and tools to dodge cyber threats. It is imperative for CEOs of such organizations to establish strong communication with their IT/Security teams to understand their vulnerabilities and improve their security posture.
- Security Automation is the Way to Go
Investing in the right kind of tools and expertise can go a long way in securing your organization from coming-of-age attacks. A powerful threat protection solution, Security Information and Event Management (SIEM), will not only help you employ the best-of-breed security expertise and market-winning security intel and tool, but will also help you deploy the right layers of security. It will also help you abide by the various security compliances thus, strengthening your organization’s security posture in the long run and most importantly, saving you from any kind of legal tussle.
Takeaway
Every other day, there’s a new headline about some organization falling prey to a cyberattack or breach only to repent later. In most cases, the attack was not even detected for almost a year causing severe damage and data compromise. This is why it is advisable for CEOs to think like cyber investigators. Scrutinize the attacks that are in the news. Ask yourself what if my organization falls victim to such an attack? Adjust your priorities, strategies and educate your employees.
Don’t take the bait! Be cyber smart!
The Future is Digital, The Future is Now!
About the Author
 Sheetal Pansare is the President & Global CEO at Futurism Technologies based in the United States and has been an ardent evangelist of Digital Transformation (DX). Having been in the tech industry for over two decades transforming businesses worldwide delivering digital delight, he believes that now is the right time to reimagine how we see, perceive, and secure our digital world.
Sheetal Pansare is the President & Global CEO at Futurism Technologies based in the United States and has been an ardent evangelist of Digital Transformation (DX). Having been in the tech industry for over two decades transforming businesses worldwide delivering digital delight, he believes that now is the right time to reimagine how we see, perceive, and secure our digital world.
Sheetal P can be reached online at LinkedIn and at our company website http://www.futurismtechnologies.com/.
