Agenda ransomware group, also known by its aliases Qilin and Water Galura, has been ramping up its attacks globally.
This nefarious group has focused on the United States, Argentina, Australia, and Thailand, and it has been targeting industries critical to the economy, such as finance and law.
However, a recent trend has emerged: Agenda is setting its sights on a new, highly critical target: VMware vCenter and ESXi servers.
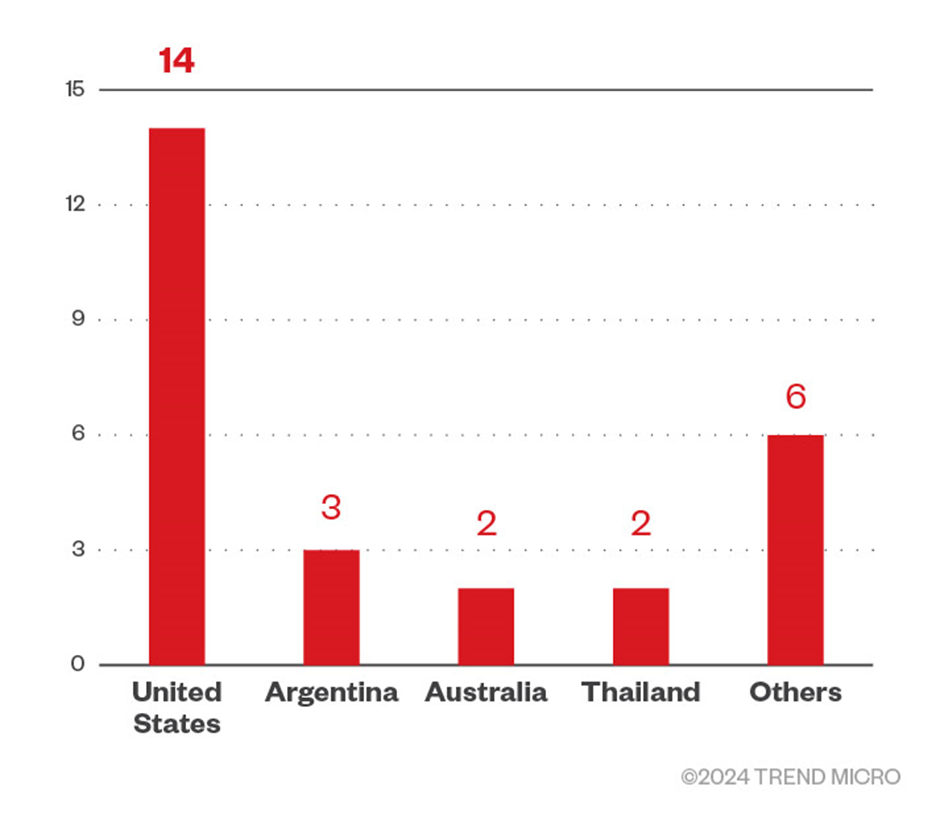
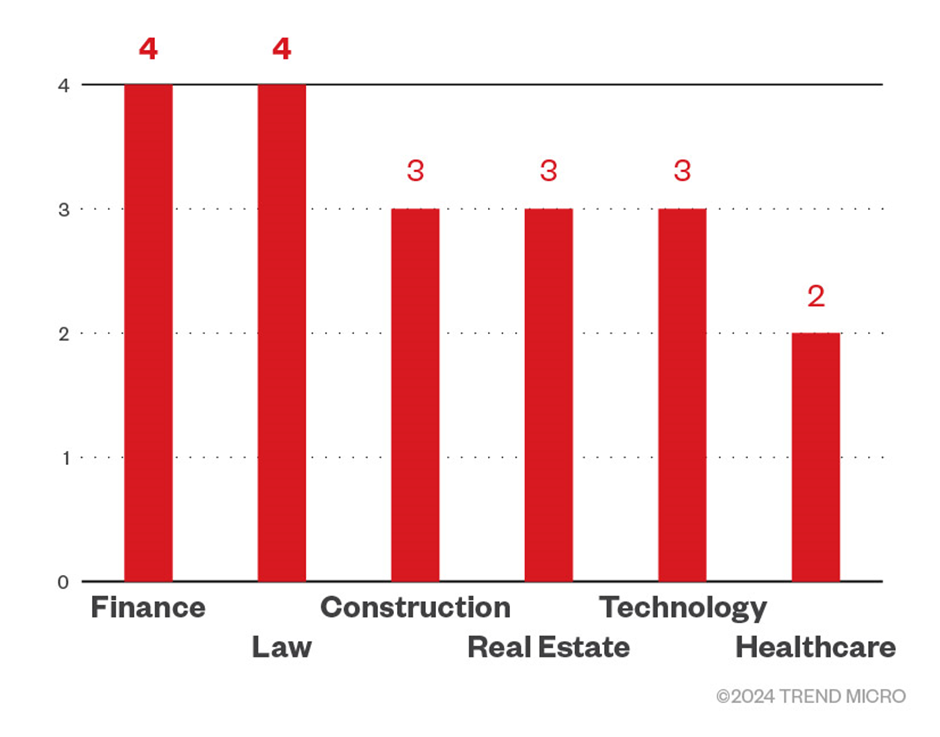
The Rise of Agenda Ransomware
First identified in 2022, Agenda has quickly evolved, demonstrating a sophisticated understanding of cybersecurity vulnerabilities and how to exploit them.
Trend Micro, a leading cybersecurity firm, has been closely monitoring the group’s activities and has noted a significant uptick in attacks since December 2023.
This surge in activity suggests that the group is either expanding its operations or becoming more effective at reaching its targets.
A recent tweet by Dark Reading reveals that a global ransomware wave has been launched explicitly targeting VMware ESXi servers.
Technical Breakdown
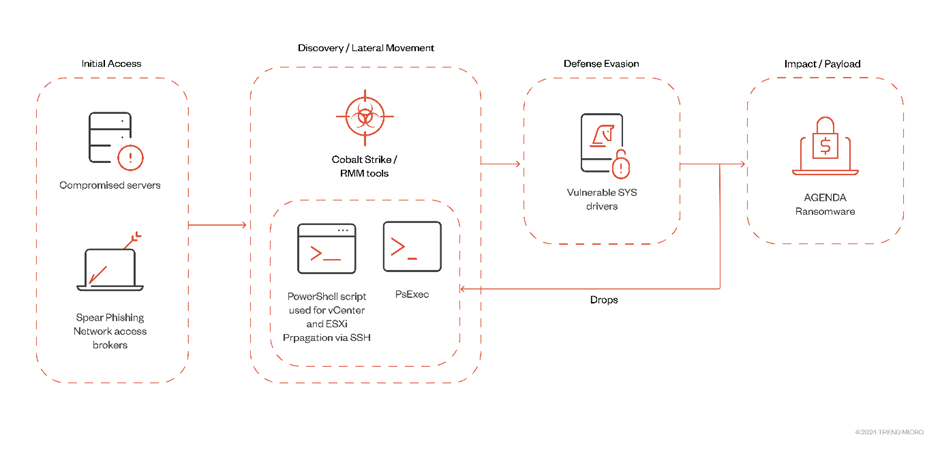
The agenda’s method of attack is particularly insidious. The group employs Remote Monitoring and Management (RMM) tools and Cobalt Strike to deploy its ransomware binary.
Once inside the system, the ransomware can propagate through various means, including PsExec and SecureShell, and employs different vulnerable SYS drivers for defense evasion.
A comparison of the command-line arguments used by Agenda in July 2023 and February 2024 reveals significant enhancements in the ransomware’s capabilities.
Notably, the addition of arguments such as –no-sandbox for disabling sandbox detection, –impersonate for token impersonation, and –spread-center for propagation in vCenter and ESXi, among others, showcases the group’s evolving sophistication.
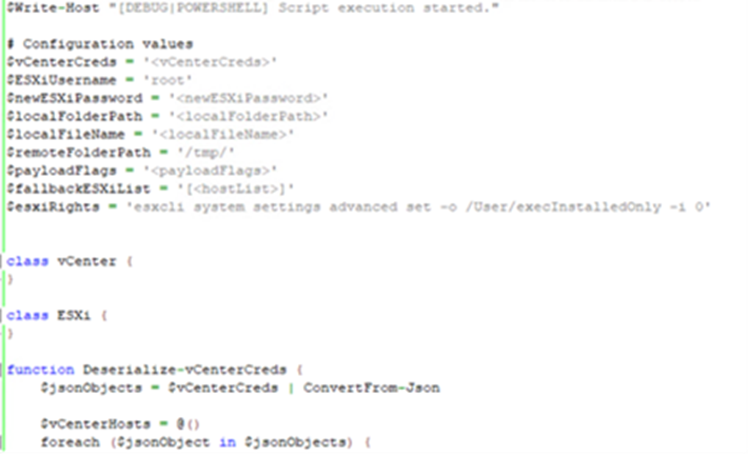
Lateral Movement: T1021.004 Remote Services – SSH
One of the most alarming developments is Agenda’s ability to spread to VMWare vCenter and ESXi servers.
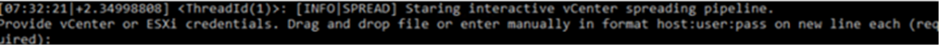
By executing a custom PowerShell script embedded in the binary, the ransomware can propagate across virtual infrastructure, potentially leading to significant data, financial loss, and disruption of services.
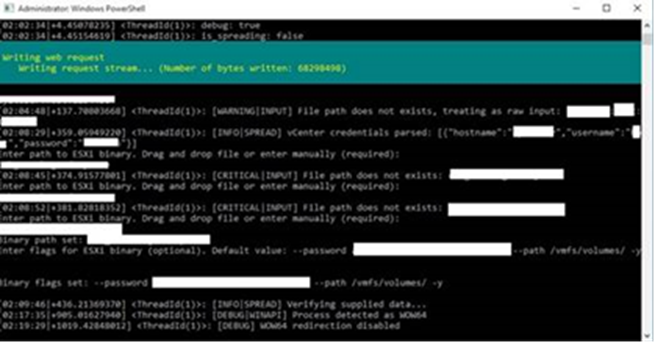
Defense Evasion Techniques
Agenda employs the Bring Your Vulnerable Driver (BYOVD) technique to evade detection, leveraging different vulnerable drivers to disable security tools.
This approach highlights the adaptability of ransomware and the challenges cybersecurity defenses face in stopping these threats.
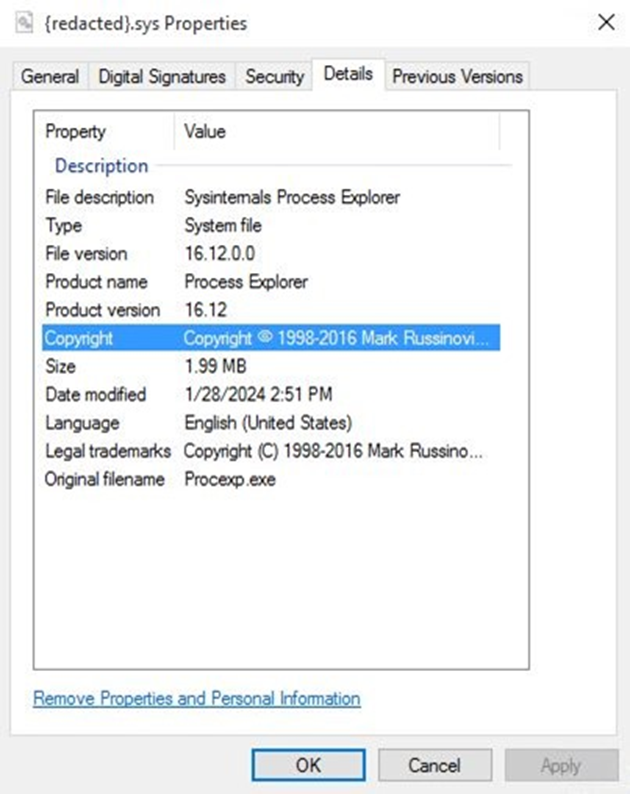
Organizations are advised to adopt a multilayered security approach to combat the threat of Agenda and similar ransomware.
This includes sparingly granting administrative rights, performing regular security scans, backing up data, practicing safe email and web browsing habits, and educating users on social engineering risks.
The Agenda ransomware group’s focus on VMWare vCenter and ESXi servers marks a significant escalation in the cyber threat landscape.
As these attacks evolve, organizations must stay vigilant and implement robust cybersecurity measures to protect their critical infrastructure from these increasingly sophisticated threats.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
