Recent investigations indicate that a potentially malicious actor has gained unauthorized access to the sensitive information of 3,200 Airbus suppliers. The data that was left accessible contains sensitive information such as names, email addresses, and phone numbers.
In addition, the person responsible for the most recent attack said that they want to carry out other strikes on Lockheed Martin and Raytheon in the near future. The person going by the name “USDoD” had already parted ways with the database for the FBI’s information-sharing system in the month of December 2022.
The “USDoD” published an advertisement for the purchase of the InfraGrad database on the previously famous “Breached” forum in December of 2022. The advertisement was tracked by the FBI, which led to the domain being seized by the authorities.
Following this, threat actors, such as “USDoD,” required a venue for selling stolen data, thus they formed “BreachForums.” The threat actor made two separate posts on the BreachForums throughout the month of September 2023. These posts consisted of two statements.
In one of the threads, it was reported that the United States Department of Defense (USDoD) has become an official member of the “Ransomed” ransomware gang, which is responsible for targeting the majority of firms during the month of September 2023. The second thread, which was about the Airbus data breach, was a great deal more entertaining.
This security flaw was caused by an employee of a Turkish airline who was in possession of an unlicensed copy of a Microsoft.NET framework. The individual had gotten the software via questionable means. In the end, this contributed to the propagation of the malicious software known as RedLine, which is programmed to gather sensitive information from users without their knowledge or agreement.
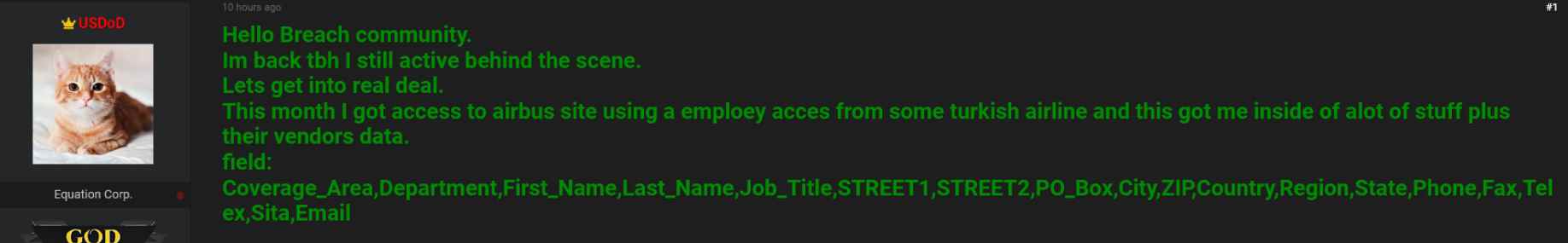
Threat actors were able to get access to the credentials of the compromised system and then utilized those credentials as the first attack vector.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
