With Android devices deeply embedded in business operations, it’s no surprise that cybercriminals are increasingly targeting them.
Businesses are now prime targets, facing threats like banking trojans, spyware, ransomware, and ad fraud, all designed to steal sensitive company data, compromise financial systems, and disrupt operations.
The problem is, that many security tools aren’t built to catch these threats fast enough, leaving people and businesses vulnerable.
To help with this, ANY.RUN has added Android OS support to its interactive sandbox. Cybersecurity professionals can now run and analyze APK files in real-time, spot threats more quickly, and get a much clearer picture of what a malicious app is doing.
Key Benefits for Cybersecurity Professionals
Android OS support enhances security teams’ efficiency in several ways:
- Simplifies malware analysis: Users can analyze Android threats, with detailed insights into network traffic, behavioural indicators, and file execution logs.
- Accelerates incident response: The interactive sandbox allows for real-time detection and mitigation of Android malware, reducing the time needed for investigations.
- Reduces costs and complexity: Security teams don’t need to juggle multiple tools. Sandboxes like ANY.RUN consolidate everything into one platform, improving efficiency and lowering operational costs.
- Enhances SOC workflows: Tier 1 analysts can quickly escalate cases to Tier 2 with comprehensive forensic data on Android malware, streamlining threat intelligence and response processes.
How Android OS Inside Virtual Machine Makes Malware Analysis Easier
Analyzing Android malware inside ANY.RUN’s sandbox is as easy as investigating threats on Windows or Linux. With the latest update, security professionals can interact with and examine Android malware in real time, making the process faster and more intuitive.
Before launching an analysis, users can select Android OS from the standard operating system menu. Once selected, they upload the APK file and begin the investigation.
Since ANY.RUN’s sandbox is fully interactive, analysts can engage with the malicious file as if they were running it on a real Android device.
In a real analysis session, you can see firsthand how easy it is to interact with a suspicious APK file inside ANY.RUN’s interactive sandbox.
Let’s take Coper, for example – a well-known Android banking trojan designed to steal financial data, intercept SMS messages, and execute commands remotely. This malware often disguises itself as legitimate banking or financial apps, tricking users into granting permissions that allow full control over the device.
View analysis session with Coper
The fastest way to determine if a file is malicious is by checking the top right corner of the screen, where ANY.RUN automatically highlights suspicious activity.
In our case, it’s marked in red, immediately alerting us that the sample is dangerous. The sandbox identifies that we are dealing with Coper, confirming that this APK is actively performing harmful actions.
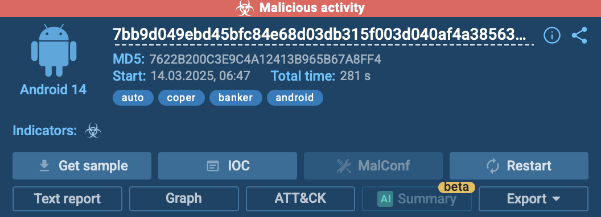
To dive deeper, analysts can inspect all processes in the Process Tree section. This view provides a structured breakdown of how the malware operates, making it easier to understand what actions it takes after execution.
This allows SOC teams, malware analysts, and threat hunters to quickly assess the impact of a threat without wasting time on manual investigation.
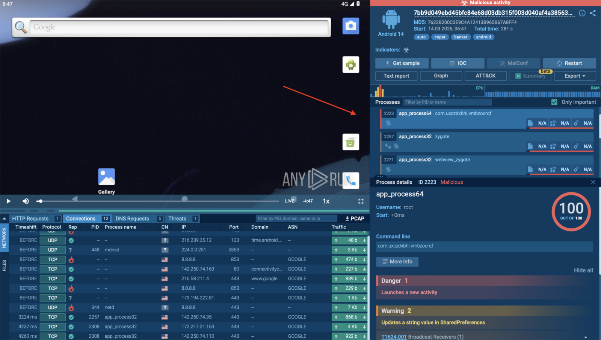
Another crucial feature is the ATT&CK Matrix section, where you can see exactly what techniques and tactics the malware is using. This makes it much easier to map threats to real-world attack patterns.
If more details are needed, users can simply click on any specific tactic or technique to get a detailed explanation of how it works and what risks it poses.
Finally, for a more structured breakdown, ANY.RUN provides a text report that compiles all findings into a well-organized format.
This is especially useful for sharing insights with the team, documenting the investigation, or conducting a deeper analysis later on.
Instead of manually piecing together information from different sources, security teams get a clear, detailed report that speeds up decision-making and incident response.
Analyze Android Threats Faster in a Secure Environment
With ANY.RUN’s new Android OS sandbox, cybersecurity professionals can now analyze APK files faster and more efficiently in a secure, interactive environment.
Whether you’re investigating malware for incident response, threat hunting, or research, this update makes the process quicker, more intuitive, and highly effective.
- Faster detection: Get real-time alerts on suspicious activity without delays.
- Easier analysis: Interact with malware just like you would on a real device and inspect its behaviour effortlessly.
- Better collaboration: Share structured reports with your team, helping everyone stay informed and respond quickly to threats.
