Arsink is a cloud-native Android Remote Access Trojan (RAT) that steals sensitive data and grants attackers deep control over infected devices.
In several builds, larger media is pushed through Google Apps Script into Google Drive, while other versions rely on Firebase Realtime Database (RTDB) and Firebase Storage, sometimes paired with Telegram for fast exfiltration.
The campaign is operating at notable scale. Analysts identified 1,216 distinct APK hashes during the observation period, suggesting many repackaged builds and frequent churn.
Researchers tracked the campaign say they observed multiple variants that abuse trusted cloud and messaging platforms to hide command-and-control (C2) traffic and move stolen files.
Of these, 774 samples included Google Apps Script or “macro” upload logic, reinforcing that Google services were heavily used for media and file transfer.
Researchers also counted 317 unique Firebase RTDB endpoints used as C2 or data sinks, and infrastructure enumeration recovered roughly 45,000 unique victim IP addresses.
Overview of the Arsink RAT Threat
Arsink spreads mainly through social engineering rather than a single exploit chain. Malicious APKs are shared via Telegram channels, Discord posts, and direct download links hosted on services like MediaFire.

The lures impersonate more than 50 well-known brands such as Google, YouTube, WhatsApp, Instagram, Facebook, and TikTok and often present the malware as “mod,” “pro,” or “premium” versions of real apps.
In most cases, the apps offer little to no legitimate functionality, display minimal UI, and quickly request sensitive permissions before running quietly in the background.
Researchers grouped observed samples into four operational variants: a Firebase + Apps Script/Drive variant that stores structured telemetry in RTDB while uploading larger content through Apps Script; a Telegram exfiltration variant that sends stolen data directly to an attacker-controlled bot; an embedded-payload dropper variant that extracts a secondary APK from the app’s assets.
Once installed, Arsink can harvest device identifiers, public IP, coarse location text, and Google account emails found on the device.
It also steals SMS messages, call logs, and contacts, and can record microphone audio and enumerate photos and files on external storage.
Mitigations
Remote commands include toggling the flashlight, vibrating the device, showing messages, text-to-speech, file operations, initiating calls, and even wiping external storage.
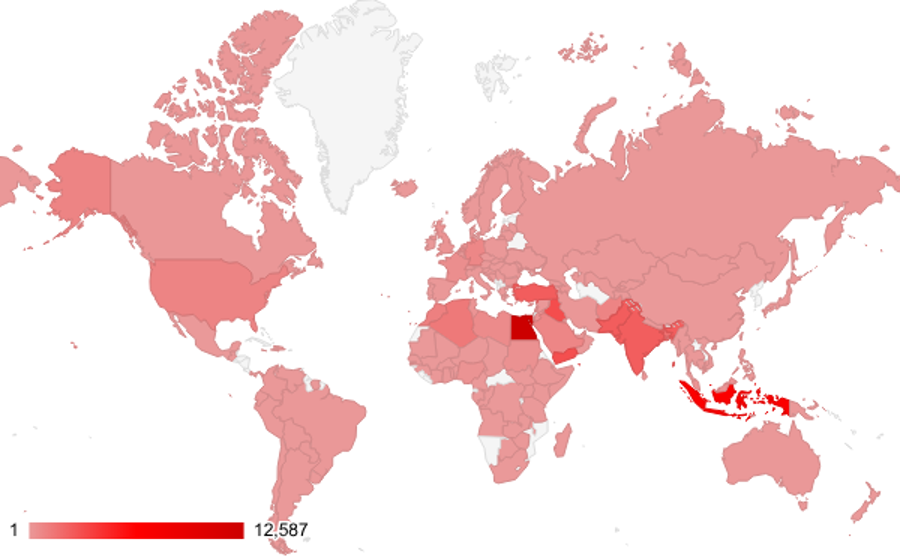
The largest concentrations were observed in Egypt (≈13,000 devices), Indonesia (≈7,000), Iraq (≈3,000), Yemen (≈3,000) and Türkiye (≈2,000).
Notable clusters also appear in Pakistan (≈2,500), India (≈2,500), Bangladesh (≈1,600), and North African countries such as Algeria and Morocco (each ≈1,000), regions.
Google also stated known Arsink versions are not on Google Play, and Play Protect can warn or block suspicious apps, including those installed from outside the Play Store.
For stealth and persistence, it can hide its launcher icon and run a foreground service with a persistent notification.
zLabs said it coordinated with Google to report abuse and disrupt malicious Firebase endpoints and Apps Script infrastructure.
However, defenders warn that rapid variant changes and flexible exfiltration paths mean users still need strong device-level hygiene avoiding sideloaded “mod” APKs and treating brand-themed download links in chat apps as high risk.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




