Author: Cybernoz
Cybersecurity researchers at Cofense Intelligence have identified a sophisticated phishing tactic leveraging Blob URIs (Uniform Resource Identifiers) to deliver credential…
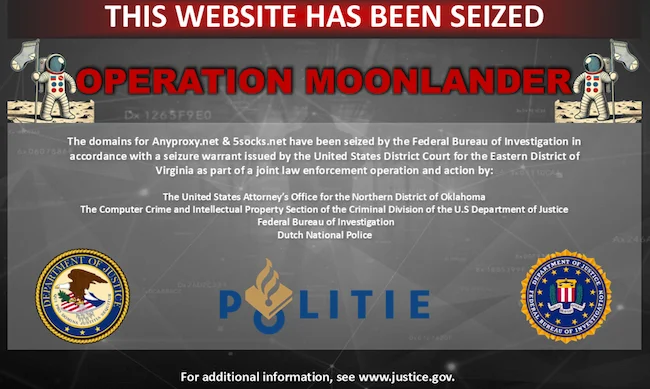
US and Dutch law enforcement, with the help of Lumen researchers, have disrupted 5socks and Anyproxy, two proxy-for-rent services that…
Federal authorities seized two domains and indicted four foreign individuals for alleged involvement in a long-running botnet service that infected…
A Türkiye-backed cyberespionage group exploited a zero-day vulnerability to attack Output Messenger users linked to the Kurdish military in Iraq….
A new information-stealing malware dubbed “PupkinStealer” has emerged as a significant threat to individuals and enterprises. Developed in C# using…
A 20-year-old criminal proxy network has been disrupted through a joint operation involving Lumen’s Black Lotus Labs, the U.S. Department…
Check Point’s April 2025 malware report reveals increasingly sophisticated and hidden attacks using familiar malware like FakeUpdates, Remcos, and AgentTesla….
Lee Enterprises said it incurred $2 million in restoration costs due to a major cybersecurity attack in February that also…
Browser extensions have become deeply embedded in employees’ daily workflows, aiding tasks from grammar checking to discount hunting. Yet, their…
Distributed Denial of Service (DDoS) attacks, once seen as crude tools for disruption wielded by script kiddies and hacktivists, have…
Moldovan authorities have detained a 45-year-old suspect linked to DoppelPaymer ransomware attacks targeting Dutch organizations in 2021. Police officers searched…
IPFire, the powerful open-source firewall, has unveiled its latest release, IPFire 2.29 – Core Update 194, packed with security enhancements,…