Author: Cybernoz
International Anti-Ransomware Day is observed annually on May 12th, following its official declaration by INTERPOL in 2022. The day serves…
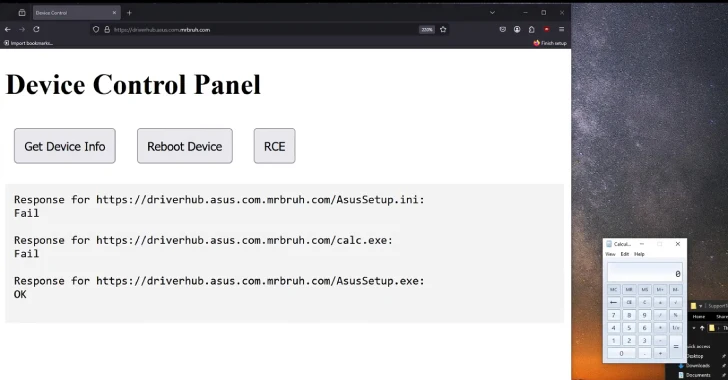
May 12, 2025Ravie LakshmananVulnerability / Endpoint Security ASUS has released updates to address two security flaws impacting ASUS DriverHub that,…
Google has agreed to a $1.375 billion settlement with the state of Texas over a 2022 lawsuit that alleged it…
UniCredit has signed a 10-year agreement with Google Cloud to “accelerate” its digital transformation by tapping into the supplier’s cloud,…
I just returned from a whirlwind weekend trip to New York with my family, and let me tell you, it…
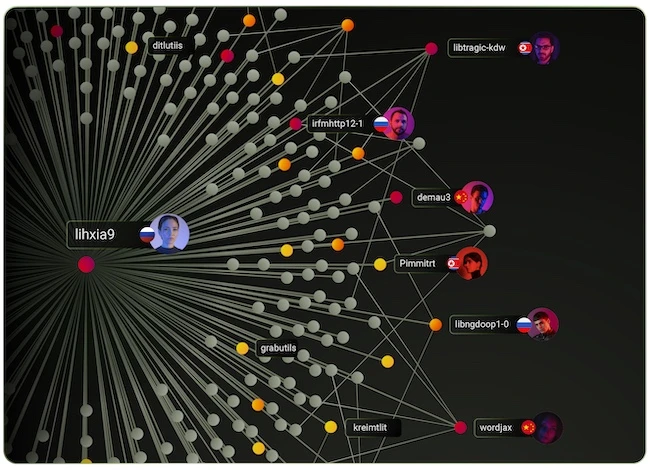
Hunted Labs announced Entercept, an AI-powered source code security platform that gives enterprises instant visibility into suspicious behavior from the…
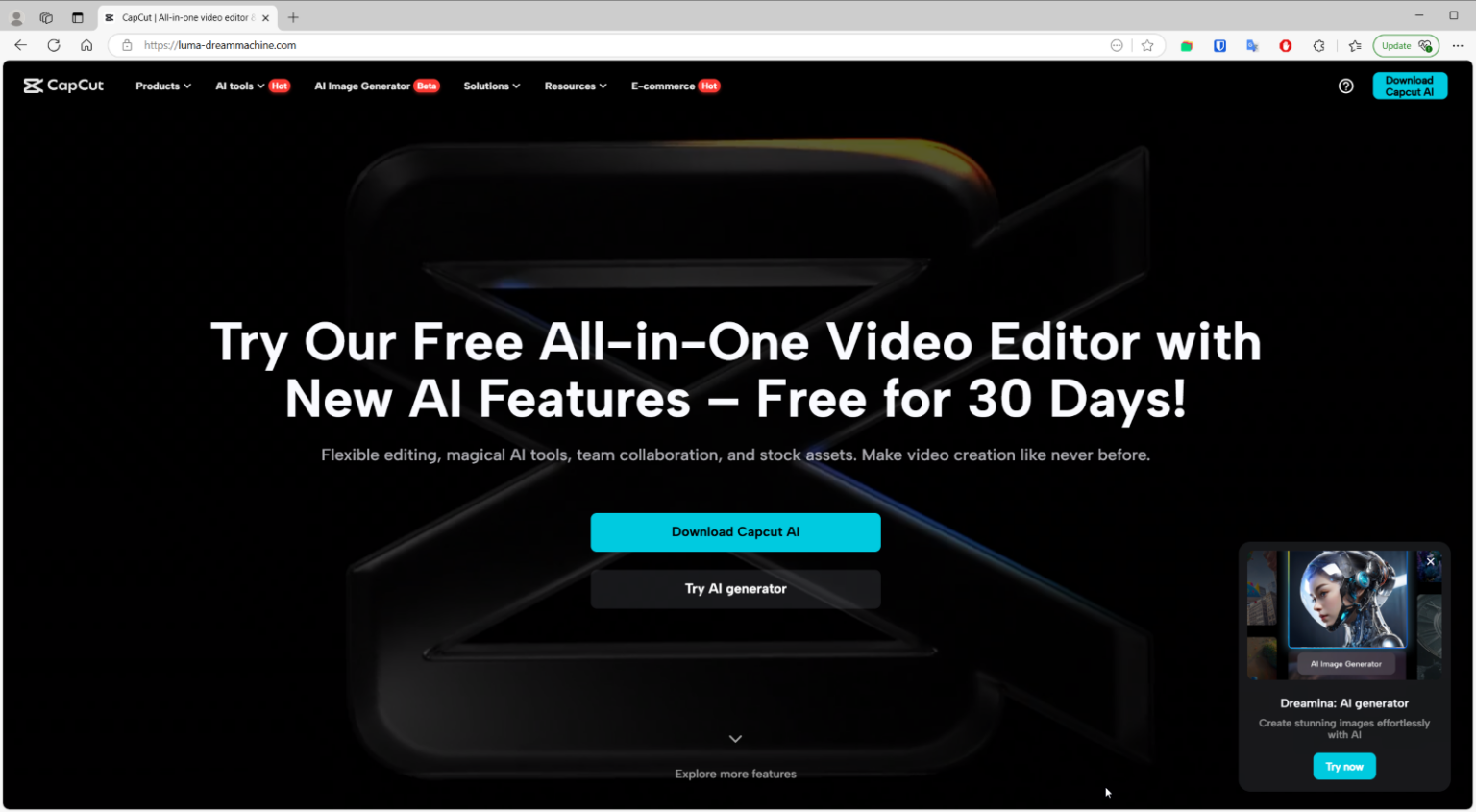
Threat actors use fake AI tools to deliver the information stealer Noodlophile Pierluigi Paganini May 12, 2025 Threat actors use…
In early May 2025, Cisco released software fixes to address a flaw in its IOS XE Software for Wireless LAN…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
A pair of vulnerabilities in Mitel’s 6800 Series, 6900 Series, and 6900w Series SIP Phones-including the 6970 Conference Unit-could enable…
The threat of ransomware continues to grow, with 150% more attacks this year compared to 2024. Organisations are scrambling to…
Cybersecurity expert Grant Smith wasn’t about to let it slide when scammers tried bilking his wife through a phony U.S. Postal Service…