Author: Cybernoz
A sophisticated supply chain attack targeting the popular npm package ‘rand-user-agent’ was discovered on May 5, 2025. The compromise affects…
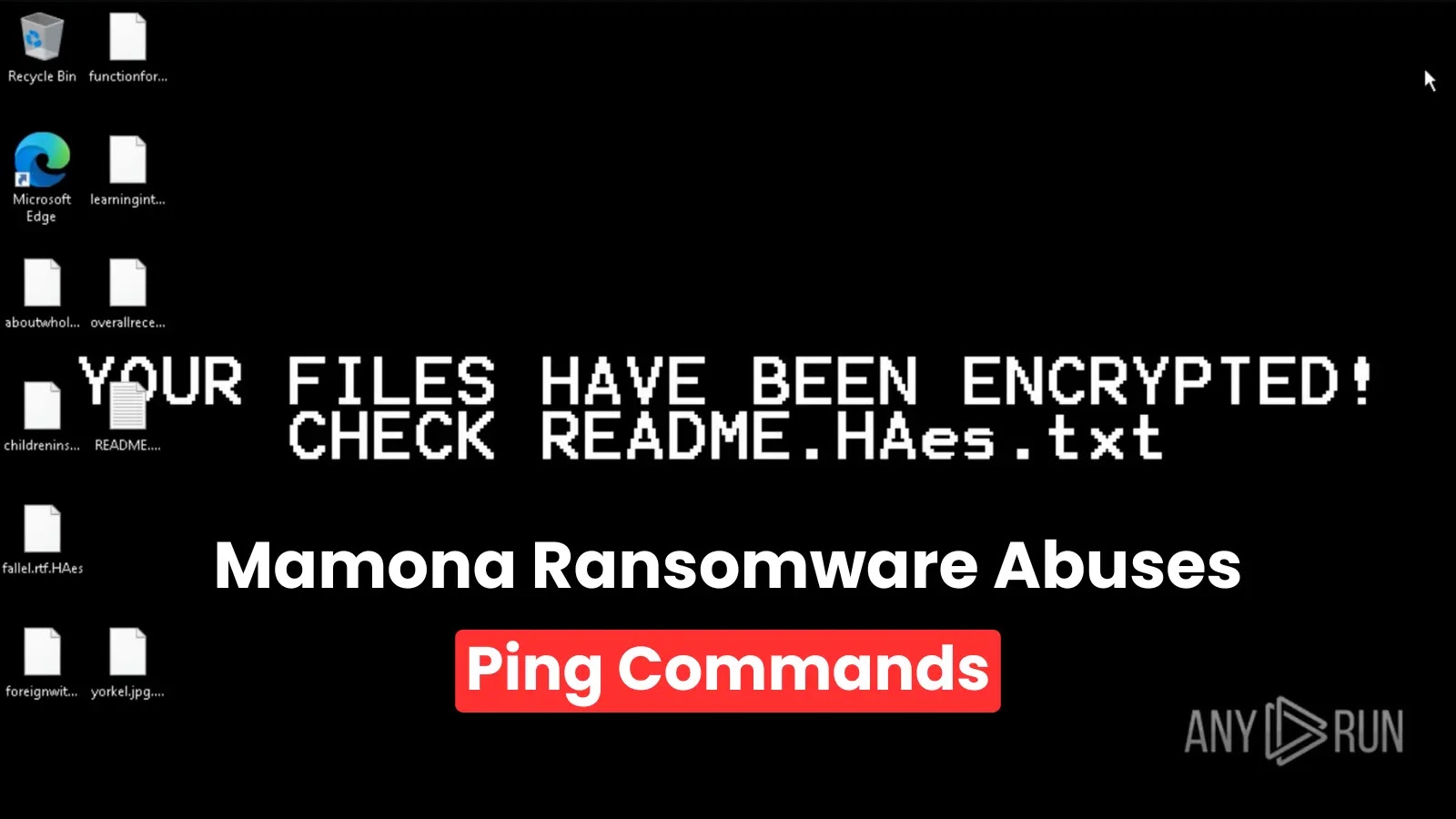
A new ransomware strain dubbed “Mamona” that operates entirely offline and leverages a clever attack strategy that abuses the Windows…
A seemingly innocent Python package has been unmasked as a sophisticated remote access trojan (RAT) targeting the Discord developer community….
Cybersecurity experts have uncovered a sophisticated attack campaign targeting IT administrators through search engine optimization (SEO) poisoning tactics. Threat actors…
A critical remote code execution vulnerability in SAP NetWeaver Visual Composer (CVE-2025-31324) is being actively exploited by a Chinese threat…
A significant surge in sophisticated recruitment scams has emerged, with cybercriminals exploiting economic vulnerabilities and the competitive job market to…
Vulnerabilities are proliferating in SonicWall devices and software this year, putting the vendor’s customers at risk of intrusion via secure…
In this third part of the series on secure programming in C and C++ I will be looking into some…
Join the authors and contributors of The Humanized Internet for an engaging discussion on the future of digital identity, privacy,…
A joint U.S.-Dutch law enforcement operation has taken down a botnet-for-hire that was comprised of thousands of end-of-life routers. The…
Law enforcement authorities have dismantled a botnet that infected thousands of routers over the last 20 years to build two…
An advanced supply chain attack has targeted the well-known npm package rand-user-agent, which receives about 45,000 downloads every week, in…