Author: Cybernoz
Every day, hundreds of new Common Vulnerabilities and Exposures (CVEs) are published, many of which target critical systems that keep…
As artificial intelligence (AI) continues its meteoric rise, 2025 is shaping up to be a transformative year in the realm…
A potential security flaw in IBM i Access Client Solutions (ACS) has raised serious concerns about password leakage, leaving users…
In this Help Net Security interview, Gerald Beuchelt, CISO at Acronis, discusses common backup strategy pitfalls, reasons for backup failures,…
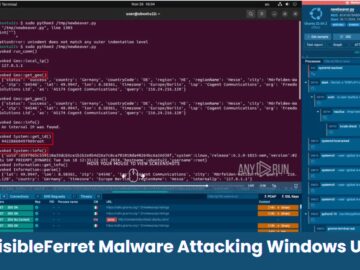
A new wave of North Korean cyberattacks, employing a sophisticated and coordinated approach, has targeted the technology, financial, and cryptocurrency…
Despite progress made in privacy staffing and strategy alignment, privacy professionals are feeling increasingly stressed on the job within a…
This list of ransomware-focused cybersecurity books is tailored for professionals seeking practical insights and deeper knowledge. Covering technical strategies, real-world…
Sixty-five per cent of organisations are embracing the power of multi-cloud environments. With these trends in mind, CIOs and decision-makers are…
Those allegations murder-for-hires, in fact, dissuaded the first Trump administration from granting clemency to Ulbricht: The White House in 2020…
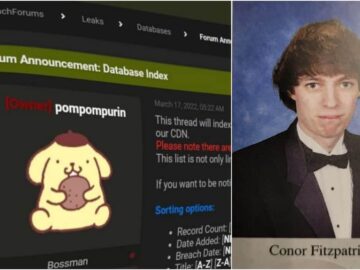
BreachForums admin Conor Fitzpatrick (Pompompurin) faces resentencing after his lenient 17-day sentence was vacated, highlighting the serious consequences of his…
Former CIA analyst pleaded guilty to leaking top-secret documents Pierluigi Paganini January 21, 2025 A former CIA analyst, Asif William…
President Donald Trump is due to announce private sector investment to build artificial intelligence infrastructure in the United States totalling…