Author: Cybernoz
Stalkerware researcher maia arson crimew strikes again. Big time. We know maia as a researcher that loves to go after…
Aug 19, 2024Ravie LakshmananMalvertising / Cybercrime Cybersecurity researchers have uncovered a surge in malware infections stemming from malvertising campaigns distributing…
Several Microsoft applications designed specifically for the Apple macOS operating system are at risk of being subverted by malicious actors,…
Flight tracking platform FlightAware is asking some users to reset their account login passwords due to a data security incident…
A recent analysis of a security vulnerability in Microsoft’s Secure Channel revealed a critical flaw that could be exploited for…
The notorious Lazarus hacker group has been identified as exploiting a zero-day vulnerability in Microsoft Windows, specifically targeting the Windows…
Torrance, United States / California, August 19th, 2024, CyberNewsWire AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced…
Own released Continuous Data Protection for Salesforce customers, further strengthening its product offering to include recovery and analysis capabilities. Own…
Aug 19, 2024Ravie LakshmananThreat Intelligence / Cryptocurrency A new type of malware called UULoader is being used by threat actors…
How To Balance the Two Sources In cybersecurity, threat intelligence covers a broad range of activities concerning collection, analysis, and…
19 Aug Palo Alto Networks CEO Says Hackers Can “Get In And Out” In Three Hours Posted at 08:34h in…
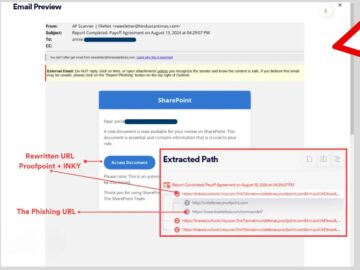
Hackers have found a way to exploit email URL rewriting features, a tool initially designed to protect users from phishing…