Author: Cybernoz
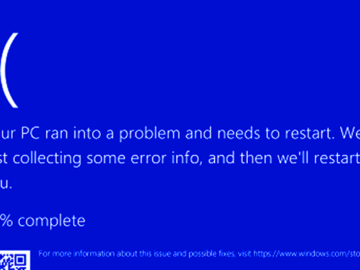
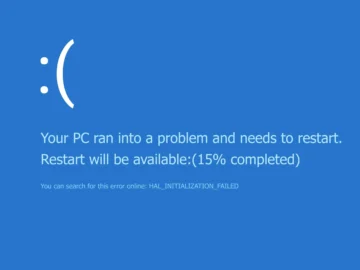
A faulty software update from cybersecurity vendor Crowdstrike crippled countless Microsoft Windows computers across the globe today, disrupting everything from…
Businesses across the world have been hit by widespread disruptions to their Windows workstations stemming from a faulty update pushed…
Today’s Microsoft outages, linked to a Crowdstrike update, shows the immense risk we face if we put all our eggs…
19 Jul Boardroom Executives Are Taking Cyberattacks As Seriously As Heart Attacks Posted at 09:00h in Blogs by Di Freeze…
On Friday 19 July 2024, the UK awoke to news of a fast-spreading IT outage, seemingly global in its nature,…
Microsoft has announced that a configuration change in Azure caused a significant global outage, disrupting Microsoft 365 services. The impact…
Two Russian individuals admitted to participating in many LockBit ransomware attacks, which targeted victims worldwide and across the United States….
Virtual Private Networks (VPNs) have become essential tools for internet users. However, the allure of free VPN services can sometimes…
The Crucial Role of Cyber-Resilient Microgrids The vulnerability of major metropolitan power grids to natural disasters has become a pressing…
Jul 19, 2024NewsroomVulnerability / Enterprise Security SolarWinds has addressed a set of critical security flaws impacting its Access Rights Manager…
Artificial intelligence (AI) workloads are new and different to those we’ve seen previously in the enterprise. They range from intensely…
Amidst the global outage affecting Microsoft Windows systems, the Indian Computer Emergency Response Team (CERT-In) has issued a critical advisory…