Author: Cybernoz
Telenor, the renowned Norwegian telecom giant, has launched Telenor Cyberdefense, marking its entry into the cybersecurity sector. This strategic move…
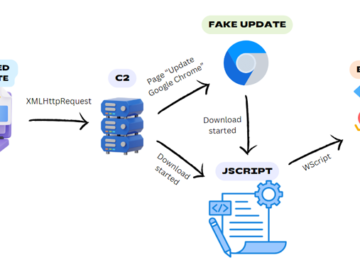
Jun 17, 2024NewsroomWeb Security / Malware Legitimate-but-compromised websites are being used as a conduit to deliver a Windows backdoor dubbed…
A critical vulnerability has been discovered in several models of ASUS routers. It allows unauthenticated remote attackers to execute arbitrary…
A 22-year-old British man was apprehended by authorities in Palma de Mallorca, Spain. The arrest, carried out by the United…
In today’s interconnected world, the advent of smart cars has brought convenience and innovation to the automotive industry. However, with…
Ghidra, a cutting-edge open-source software reverse engineering (SRE) framework, is a product of the National Security Agency (NSA) Research Directorate….
Jun 17, 2024NewsroomBotnet / Cryptocurrency Threat actors have been observed deploying a malware called NiceRAT to co-opt infected devices into…
Like a bad movie that seems to go on forever, SQL injection (SQLi) attacks have lingered since the late 1990s….
In this Help Net Security interview, Hillary Baron, Senior Technical Director for Research at CSA, highlights that the recent surge…
Major regional and global events – such as military exercises, political or economic summits, political conventions, and elections – drove…
A new speculative execution attack named “TIKTAG” targets ARM’s Memory Tagging Extension (MTE) to leak data with over a 95% chance…
Generative AI (GenAI) has become a transformative technology for enterprise businesses in more ways than one. Its widespread adoption will…