Author: Cybernoz
02 May The Early Days Of Digital Investigations – The Wild, Wild West Posted at 08:53h in Blogs by Di…
May 02, 2024NewsroomRansomware / Cyber Crime A Ukrainian national has been sentenced to more than 13 years in prison and…
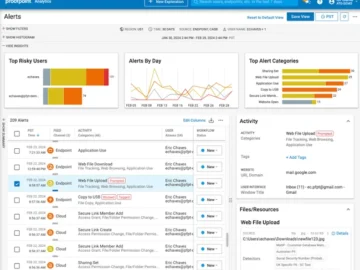
Proofpoint announced Data Loss Prevention (DLP) Transform, including GenAI use cases. Today, businesses struggle with the limitations of legacy DLP…
A never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security flaw with the…
Lawyers acting for the BBC have written to the Investigatory Powers Tribunal (IPT) over allegations that one of its journalists…
It’s World Password Day 2024! What’s clear is that passwords and creating and maintaining good password hygiene is still one…
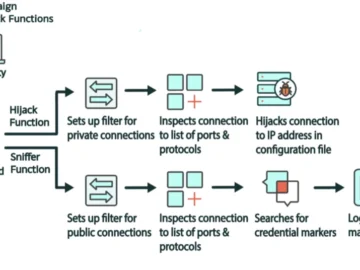
Cuttlefish, a new malware family that targets enterprise-grade small office/home office (SOHO) routers, is used by criminals to steal account…
May 02, 2024NewsroomCyber Attack / Data Breach Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign)…
Barnsley has become one of the first councils to roll out generative AI (GenAI) tools across its entire organisation as…
Cloud storage and file sharing company Dropbox disclosed a security breach that resulted in an unauthorized access to sensitive information,…
CISA adds GitLab flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini May 02, 2024 CISA adds GitLab Community and Enterprise Editions…
On this World Password Day, we should all pause and think about how we can adopt passkeys. Passkeys represent a significant…