Author: Cybernoz
Russia’s Prosecutor General’s Office has announced the indictment of six suspected “hacking group” members for using malware to steal credit…
The popular cybersecurity technology firm Bitdefender has patched a vulnerability that might lead to privilege escalation in its widely used…
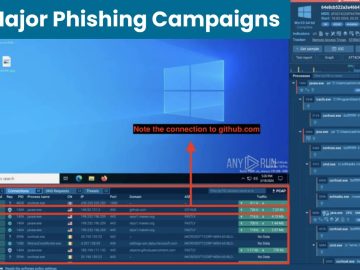
March saw many notable phishing attacks, with criminals using new tactics and approaches to target unsuspecting victims. It is time…
In recent times, the importance of maintaining efficient data backups as a defense against ransomware attacks has been repeatedly emphasized…
Prudential Financial, a stalwart in the financial services sector headquartered at 751 Broad Street, Newark, New Jersey, has reported a…
Maintaining uninterrupted services is vital for any organization. The backbone of ensuring this continuous uptime lies in the Incident Management…
[By Dov Lerner, Cybersixgill] Cybersecurity veterans often have a pessimistic view of the industry’s trends: attacks seem to be always…
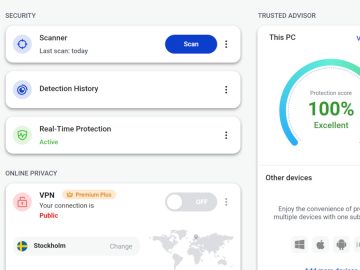
First released for Windows last year, the Malwarebytes Trusted Advisor dashboard is also now available on Mac, iOS and Android. Our…
Since October 2023, Microsoft unbundled Teams from its Microsoft 365 and Office 365 suites in the European Economic Area (EEA)…
Firmware security firm Binarly has released a free online scanner to detect Linux executables impacted by the XZ Utils supply…
Today, Congressman Eric Swalwell, CA-14, announced that he has partnered with Wolfsbane.ai to help prevent his 2024 election campaign content…
Today, Congressman Eric Swalwell, CA-14, announced that he has partnered with Wolfsbane.ai to help prevent his 2024 election campaign content…