Category: CyberSecurityNews
The Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) have released an updated joint cybersecurity advisory…
A sophisticated bulletproof hosting operation has emerged as a critical enabler of global malware campaigns, with cybersecurity researchers uncovering extensive…
The cybersecurity landscape witnessed a concerning evolution in June 2025 when the Qilin ransomware gang announced a groundbreaking addition to…
A severe authentication bypass vulnerability in Base44, a popular AI-powered vibe coding platform recently acquired by Wix, could have allowed…
The cybersecurity landscape continues to witness the emergence of sophisticated information-stealing malware, with 0bj3ctivityStealer representing one of the most recent…
A sophisticated new variant of the XWorm malware has emerged in the wild, introducing advanced anti-analysis capabilities and enhanced evasion…
A sophisticated Android banking trojan known as ToxicPanda has successfully infiltrated over 4500 mobile devices across Europe, representing one of…
A sophisticated North Korean cyber espionage operation known as TraderTraitor has emerged as one of the most formidable threats to…
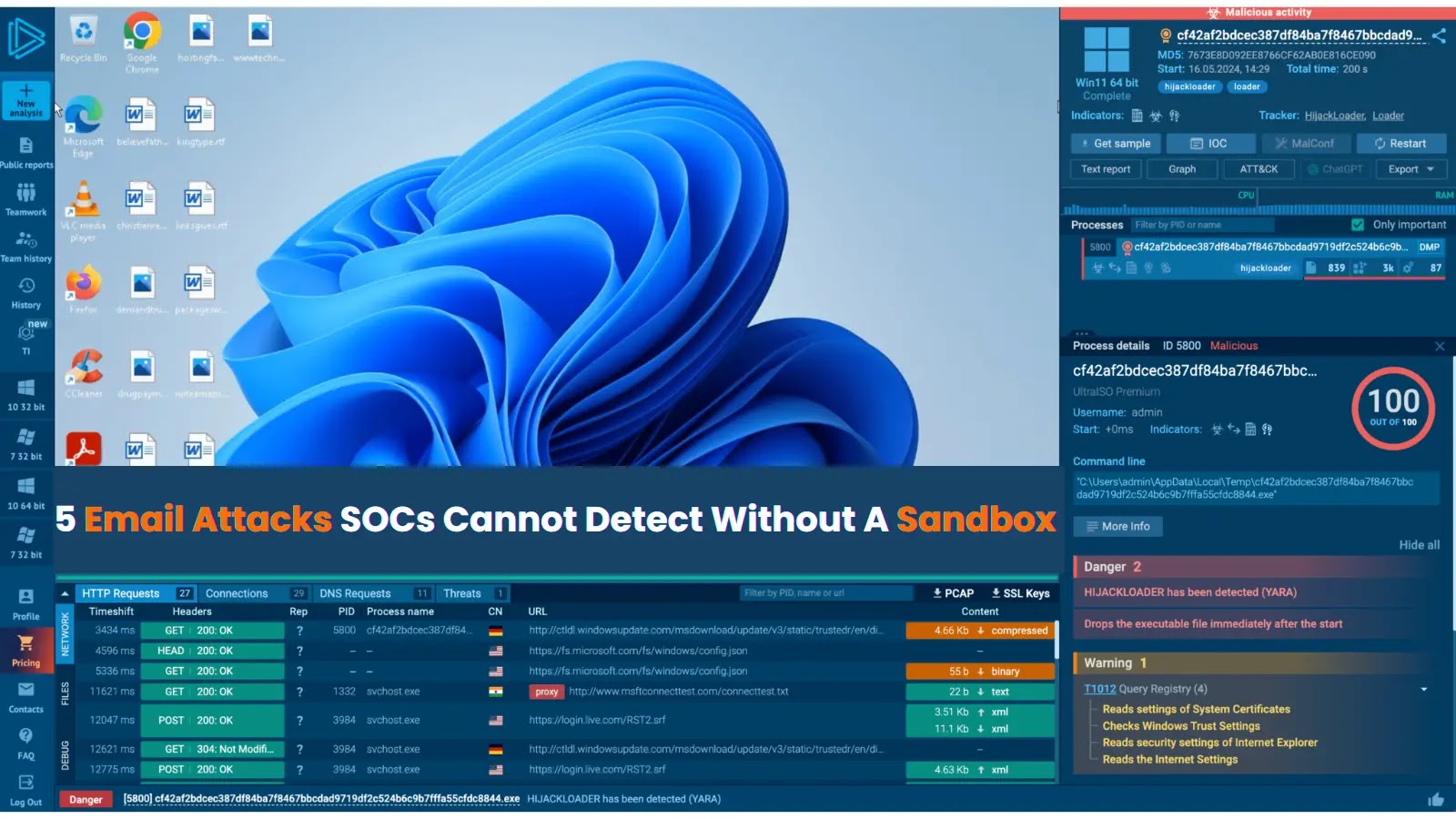
Even with Slack, Teams, and every new communication tool out there, email remains the top attack vector for businesses. Why?…
A threat actor, Tsar0Byte, allegedly claimed to have breached the company’s internal network through a vulnerable third-party link, exposing sensitive…
Palo Alto Networks, a leader in cybersecurity, announced today that it has agreed to buy CyberArk, a company known for…
Cybercriminals are increasingly leveraging malicious Windows Shortcut (LNK) files to deploy sophisticated backdoors, with a new campaign delivering an advanced…