Category: CyberSecurityNews
The UK government has announced comprehensive measures to tackle ransomware attacks, with public sector organizations and critical national infrastructure operators…
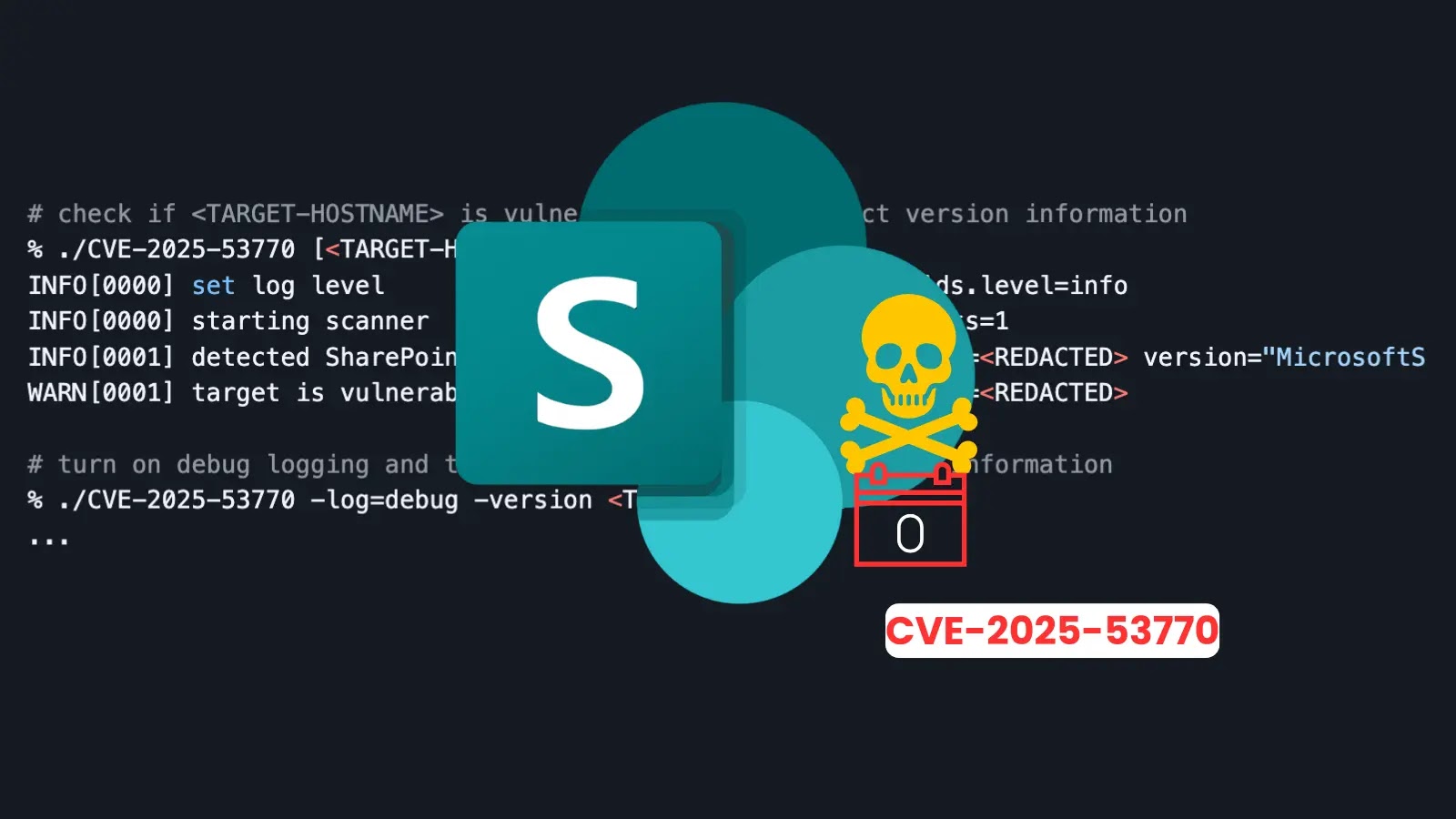
An open-source scanning tool has been released to identify SharePoint servers vulnerable to the critical zero-day exploit CVE-2025-53770. The newly…
Multiple security vulnerabilities affecting Sophos firewall products, with two enabling pre-authentication remote code execution that could allow attackers to compromise…
Cisco Systems has issued a critical security advisory warning of multiple remote code execution vulnerabilities in its Identity Services Engine…
The UK Government has imposed sanctions on Russian military intelligence units and 18 individuals following the exposure of a sophisticated…
A sophisticated new variant of DCHSpy Android surveillanceware, deployed by the Iranian cyber espionage group MuddyWater just one week after…
A fresh wave of malicious Android Package Kit (APK) files is weaving together two of cybercrime’s most reliable revenue streams—click-fraud…
Wireshark Foundation has announced the availability of Wireshark 4.4.8, the latest maintenance release of the world’s most widely used network-protocol…
A sophisticated new ransomware threat has emerged from the cybercriminal underground, targeting organizations across multiple operating systems with advanced cross-platform…
Christian Dior Couture, the luxury fashion house owned by Louis Vuitton, has begun notifying customers of a major cybersecurity incident…
Thousands of organizations worldwide face active cyberattacks targeting Microsoft SharePoint servers through two critical vulnerabilities, prompting urgent government warnings and…
A financially motivated threat group dubbed Greedy Sponge has been systematically targeting Mexican financial institutions and organizations since 2021 with…