Category: CyberSecurityNews
Cloud security has become a critical cornerstone for organizations migrating to or operating in public cloud environments. With cyberattacks increasing…
Intrusion Detection Systems (IDS) represent a critical component of modern cybersecurity infrastructure, serving as sophisticated monitoring tools that analyze network…
The endpoint security landscape in 2025 represents a sophisticated ecosystem of integrated technologies designed to protect increasingly diverse device environments….
Zero Trust Architecture (ZTA) represents a fundamental shift from traditional perimeter-based security models to a comprehensive security framework that assumes…
Modern cybersecurity threats have evolved far beyond traditional signature-based detection capabilities, demanding sophisticated approaches that combine artificial intelligence, behavioral analysis,…
Google has released a comprehensive security update for Android devices addressing multiple high-severity vulnerabilities that could allow privilege escalation and…
As cyber threats evolve at an unprecedented pace, organizations worldwide are racing to develop more effective and scalable cybersecurity training…
As organizations accelerate their digital transformation initiatives, threat modeling is rapidly becoming an indispensable practice within DevSecOps frameworks, driving significant…
A decade-old critical security vulnerability has been discovered in Roundcube Webmail that could allow authenticated attackers to execute arbitrary code…
As cybercrime costs surge toward an estimated $10.5 trillion annually by 2025, Chief Information Security Officers (CISOs) are stepping out…
As enterprises race to embrace digital transformation, many find themselves shackled to legacy systems—aging yet mission-critical technologies that power core…
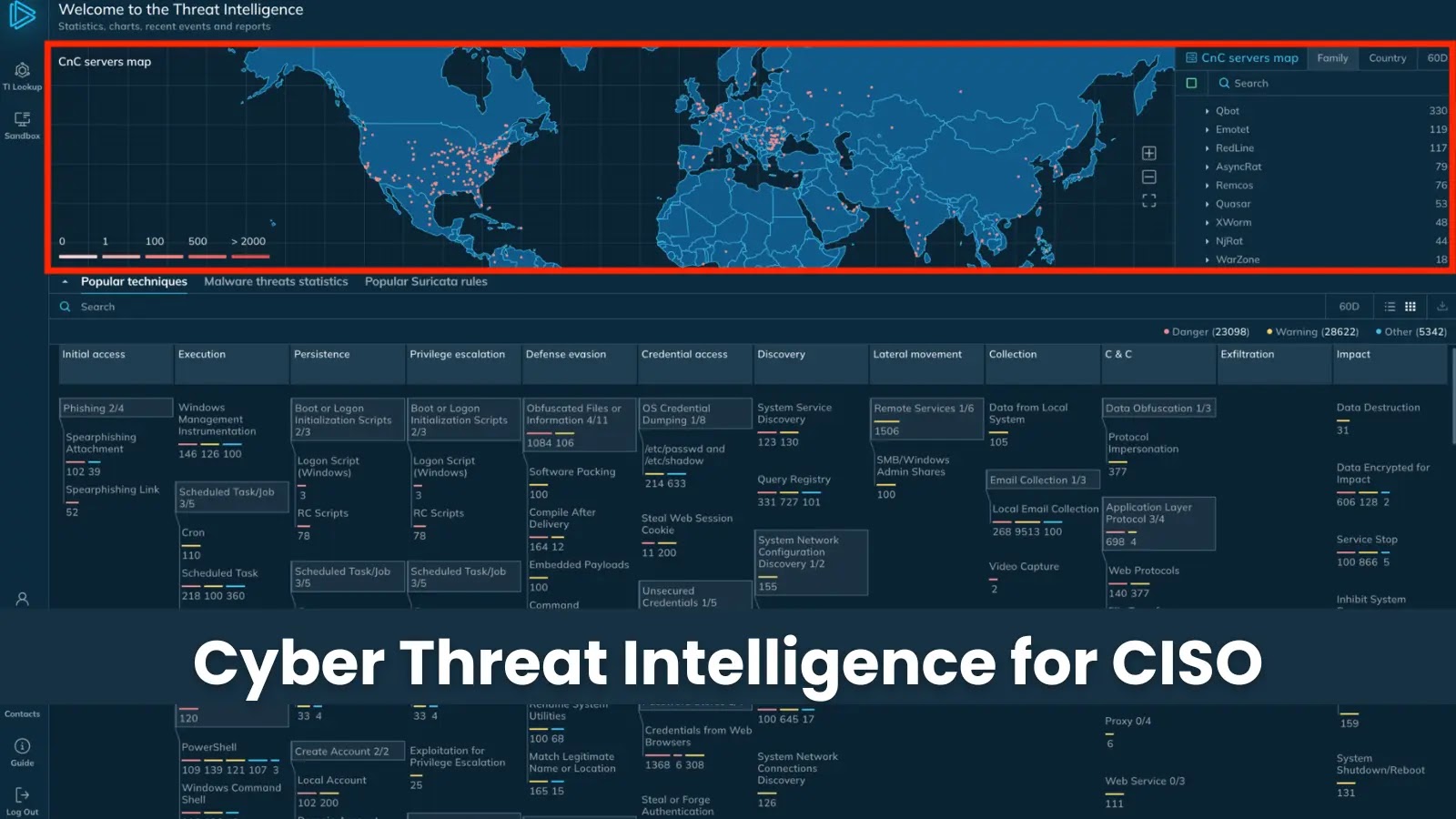
Cyber threat intelligence (CTI) is the practice of collecting, analyzing, and transforming data about cyber threats into actionable insights to…