Category: CyberSecurityNews
As 2025 unfolds, the digital battleground has never been more complex-or more consequential. Cyberattacks are no longer isolated incidents but…
Zscaler Inc. announced on May 27, 2025, a definitive agreement to acquire Red Canary, a leading Managed Detection and Response…
Cybercriminals leveraged critical vulnerabilities in remote monitoring software to breach a managed service provider and attack multiple customers. Cybersecurity researchers…
A critical security vulnerability in the popular TI WooCommerce Wishlist plugin has left over 100,000 WordPress websites exposed to potential…
Security researchers have uncovered a significant cybercrime operation involving 93.7 billion stolen browser cookies circulating on dark web marketplaces, representing…
As the digital threat landscape intensifies and new technologies reshape business operations, cybersecurity budgeting in 2025 will be significantly transformed….
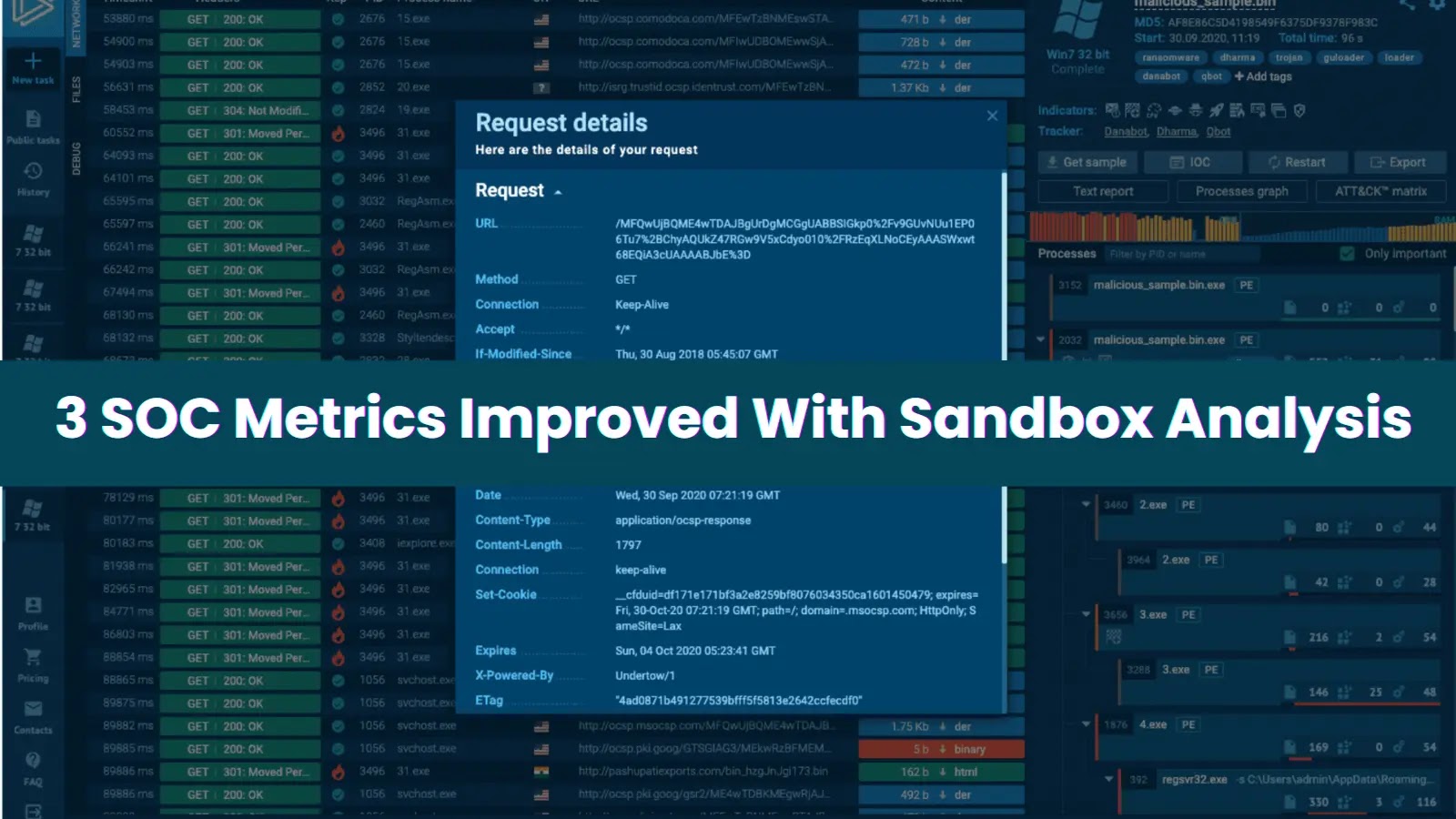
SOC teams are flooded with alerts, but what really matters is how quickly they can detect, investigate, and respond. When…
Cybercriminals have increasingly targeted Docusign, the popular electronic signature platform, to orchestrate sophisticated phishing campaigns aimed at stealing corporate credentials…
Three critical vulnerabilities in XenServer VM Tools for Windows allow attackers to execute arbitrary code and escalate privileges within guest…
As digital transformation accelerates across industries, the cybersecurity landscape is changing. 2025 marks a pivotal moment, with organizations worldwide facing…
A highly coordinated reconnaissance campaign that deployed 251 malicious IP addresses in a single-day operation targeting cloud-based infrastructure. The attack,…
A sophisticated phishing campaign targeting Italian and U.S. users through fake Microsoft OneNote login prompts designed to harvest Office 365…