Category: GBHackers
In the ever-evolving infostealer landscape, 0bj3ctivityStealer emerges as a formidable threat, blending advanced obfuscation with targeted data exfiltration. Discovered earlier…
The ToxicPanda Android banking trojan has emerged as a significant threat, compromising over 4,500 devices primarily in Portugal and Spain…
The North Korean state-sponsored advanced persistent threat (APT) known as TraderTraitor, a subgroup of the notorious Lazarus Group, has emerged…
Lumma, a sophisticated C++-based information stealer, has surged in prevalence over recent years, posing significant risks to both individuals and…
Palo Alto, California, July 29th, 2025, CyberNewsWire Despite the expanding use of browser extensions, the majority of enterprises and individuals…
Security researchers at Tracebit have discovered a critical vulnerability in Google’s Gemini CLI that enables attackers to silently execute malicious…
Security researchers have disclosed technical details of three previously patched vulnerabilities affecting SonicWall’s SMA100 series SSL-VPN appliances, highlighting concerning pre-authentication…
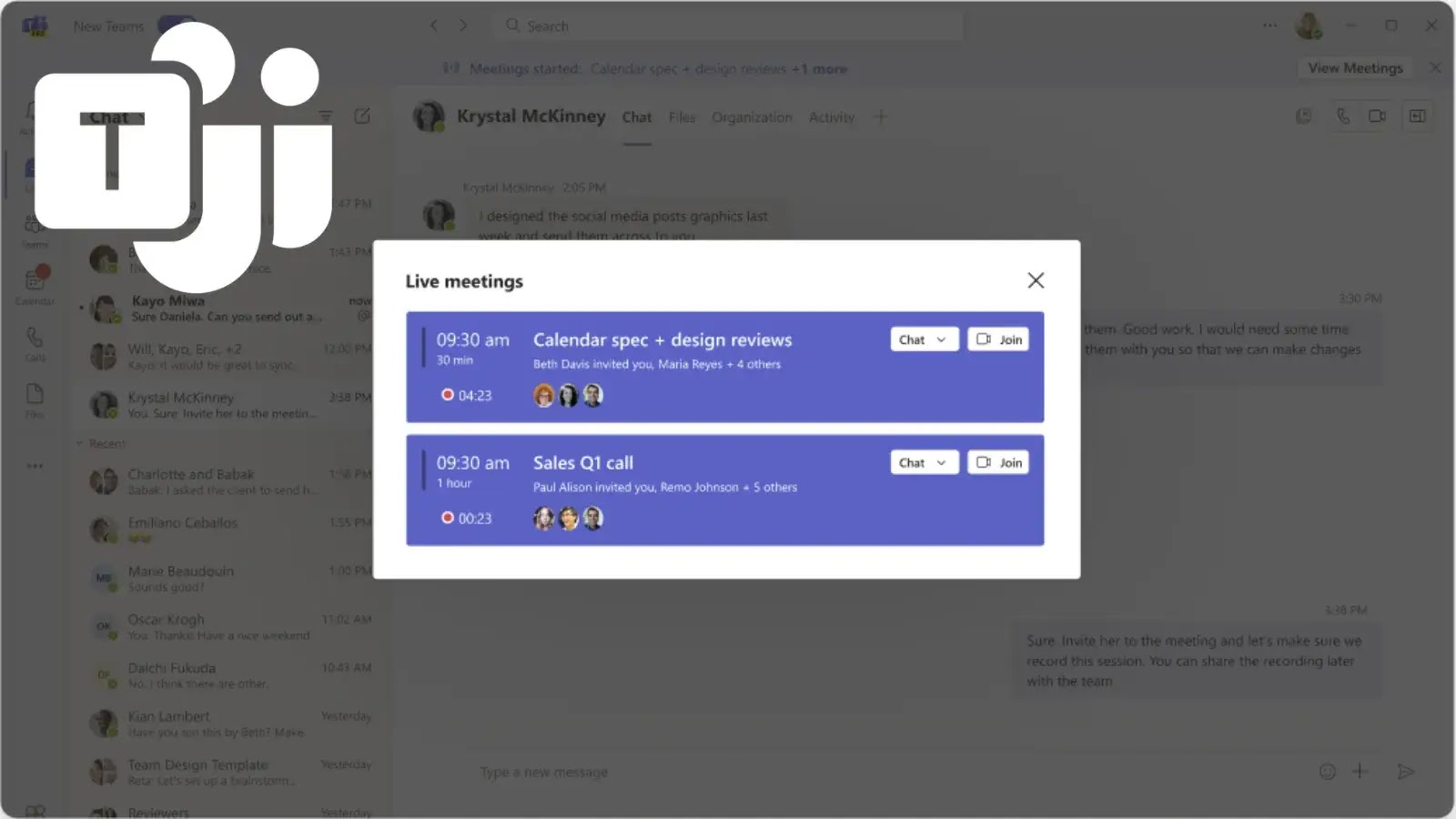
Microsoft Teams is rolling out a new meeting join banner designed to streamline the meeting experience for users who have…
Python developers are being warned about a sophisticated phishing campaign targeting users of the Python Package Index (PyPI) through fraudulent…
Linux creator Linus Torvalds announced the release of Linux kernel version 6.16 on July 27, 2025, marking the end of…
Outpost24’s threat intelligence researchers have uncovered the operations of Lionishackers, a financially motivated cyber threat actor specializing in the exfiltration…
Microsoft Threat Intelligence has uncovered a critical macOS vulnerability that enables attackers to bypass Apple’s Transparency, Consent, and Control (TCC)…