Category: GBHackers
Every security practitioner knows that employees are the weakest link in an organization, butthis is no longer the case. SquareX’s…
A newly disclosed vulnerability, CVE-2025-46647, has been identified in the openid-connect plugin of Apache APISIX, a widely used open-source API gateway….
A new wave of cyberattacks is targeting WordPress websites through malicious SEO plugins that can lead to complete site takeover….
Instagram has begun rotating its TLS certificates on a daily basis, with each certificate valid for just over a week….
Scattered Spider, also tracked under aliases such as UNC3944, Scatter Swine, and Muddled Libra, has emerged as a formidable financially…
A security researcher has uncovered a significant vulnerability affecting Lenovo computers: a writable file within the Windows directory that can…
A newly disclosed vulnerability, tracked as CVE-2025-34067, has been identified in HIKVISION’s widely deployed security management platform, applyCT (also known as…
HUMAN’s Satori Threat Intelligence and Research Team has dismantled a sprawling ad fraud operation named IconAds, which infiltrated the Google…
In a breakthrough that challenges the perceived safety of nonce-based Content Security Policy (CSP), security researchers have demonstrated a practical…
A major security lapse has exposed the credentials of over 62,000 users of Catwatchful, a full-featured Android spyware app that…
Security researchers have disclosed two significant vulnerabilities in PHP, the popular server-side scripting language, that could allow attackers to launch…
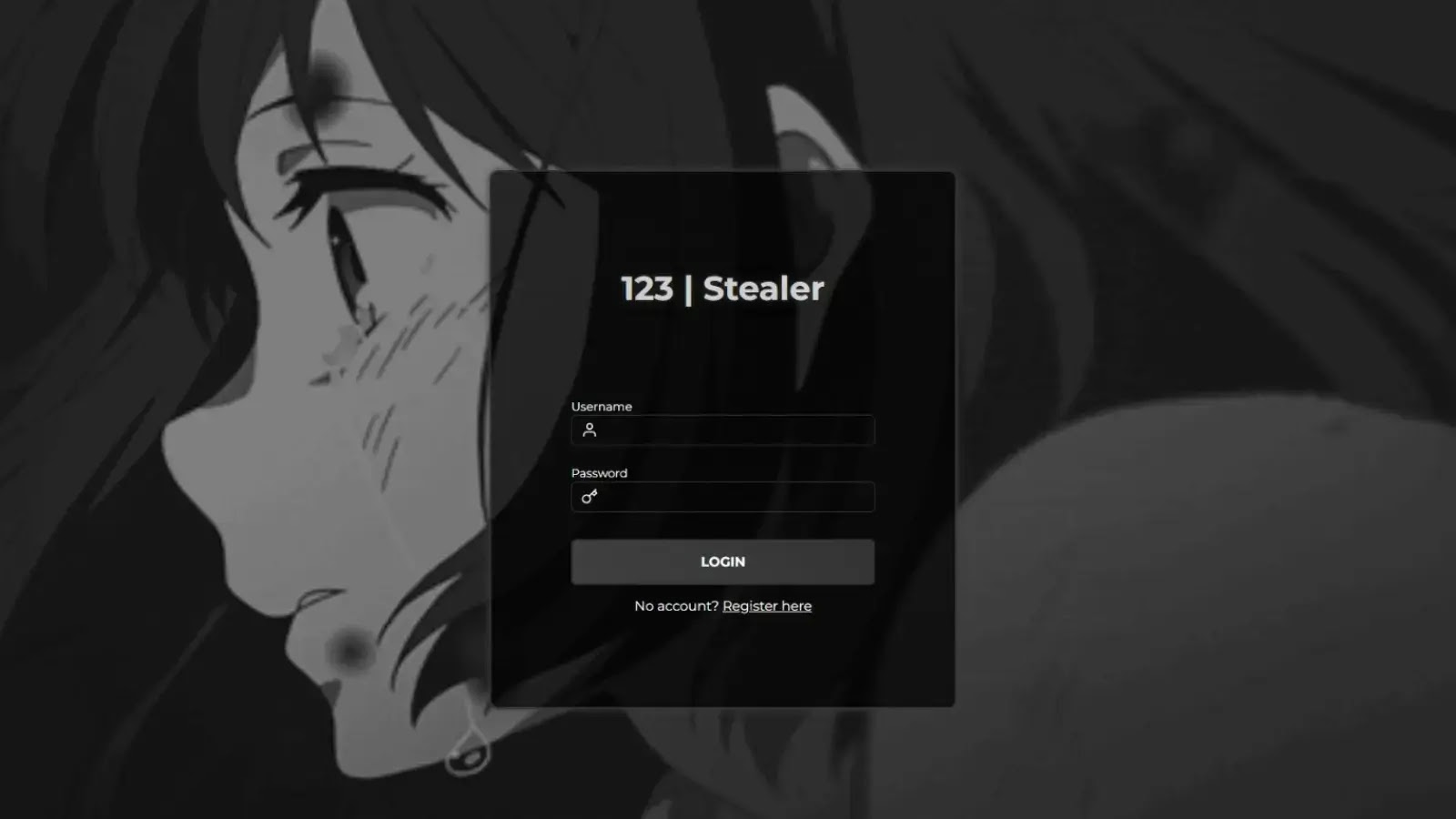
A new credential-stealing malware, dubbed “123 | Stealer,” has surfaced on underground cybercrime forums, with the threat actor known as #koneko offering…