Category: GBHackers
Microsoft announced that it will lay off approximately 9,000 employees worldwide, representing nearly 4% of its global workforce of 228,000…
A newly disclosed critical vulnerability in Wing FTP Server threatens thousands of organizations worldwide, enabling attackers to achieve full server takeover through unauthenticated remote…
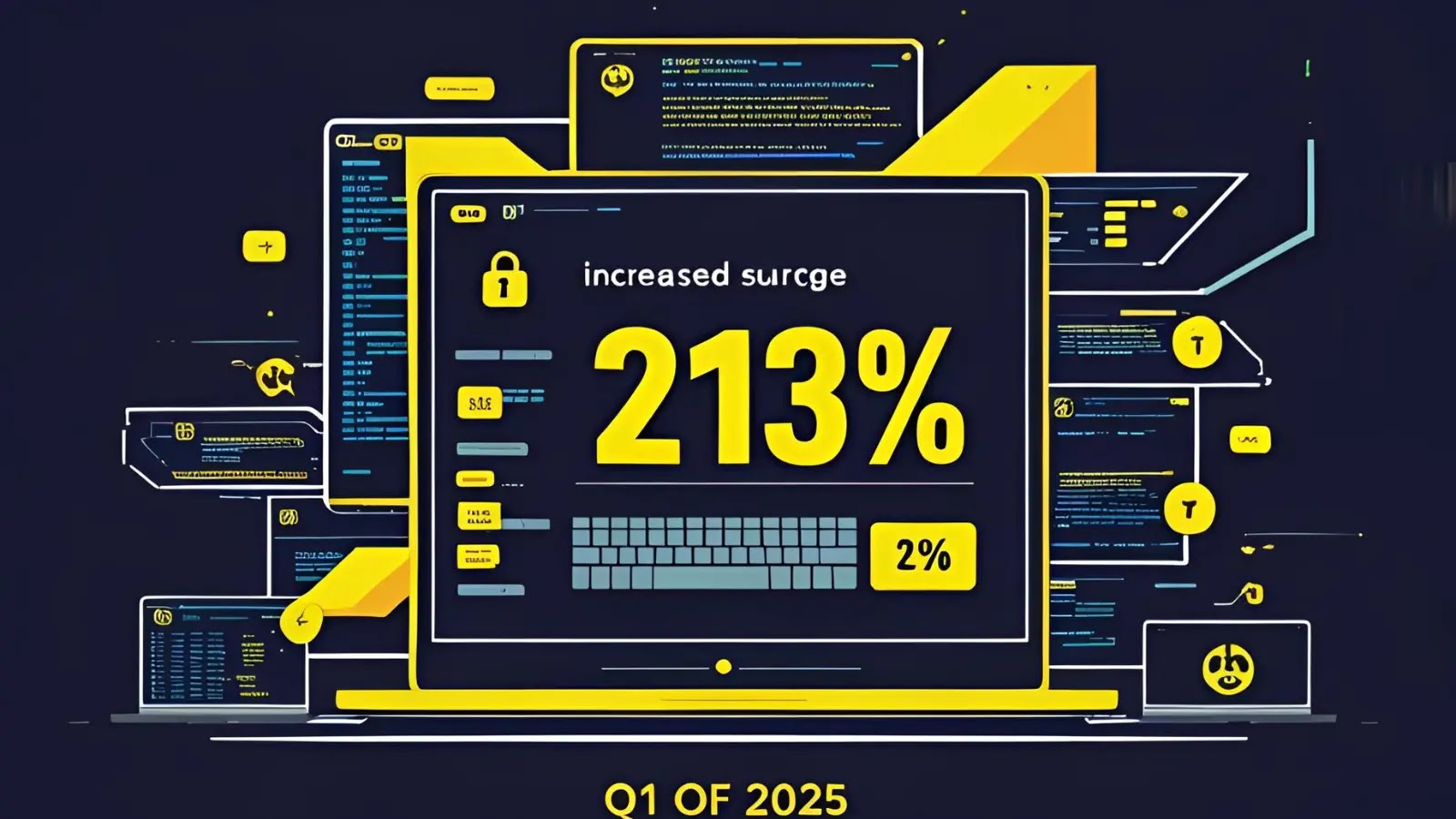
Ransomware assaults on businesses around the world have increased by 213% in the first quarter of 2025, with 2,314 victims…
A shadowy group known as Keymous+ has emerged as a formidable force in the cyber landscape, claiming responsibility for over…
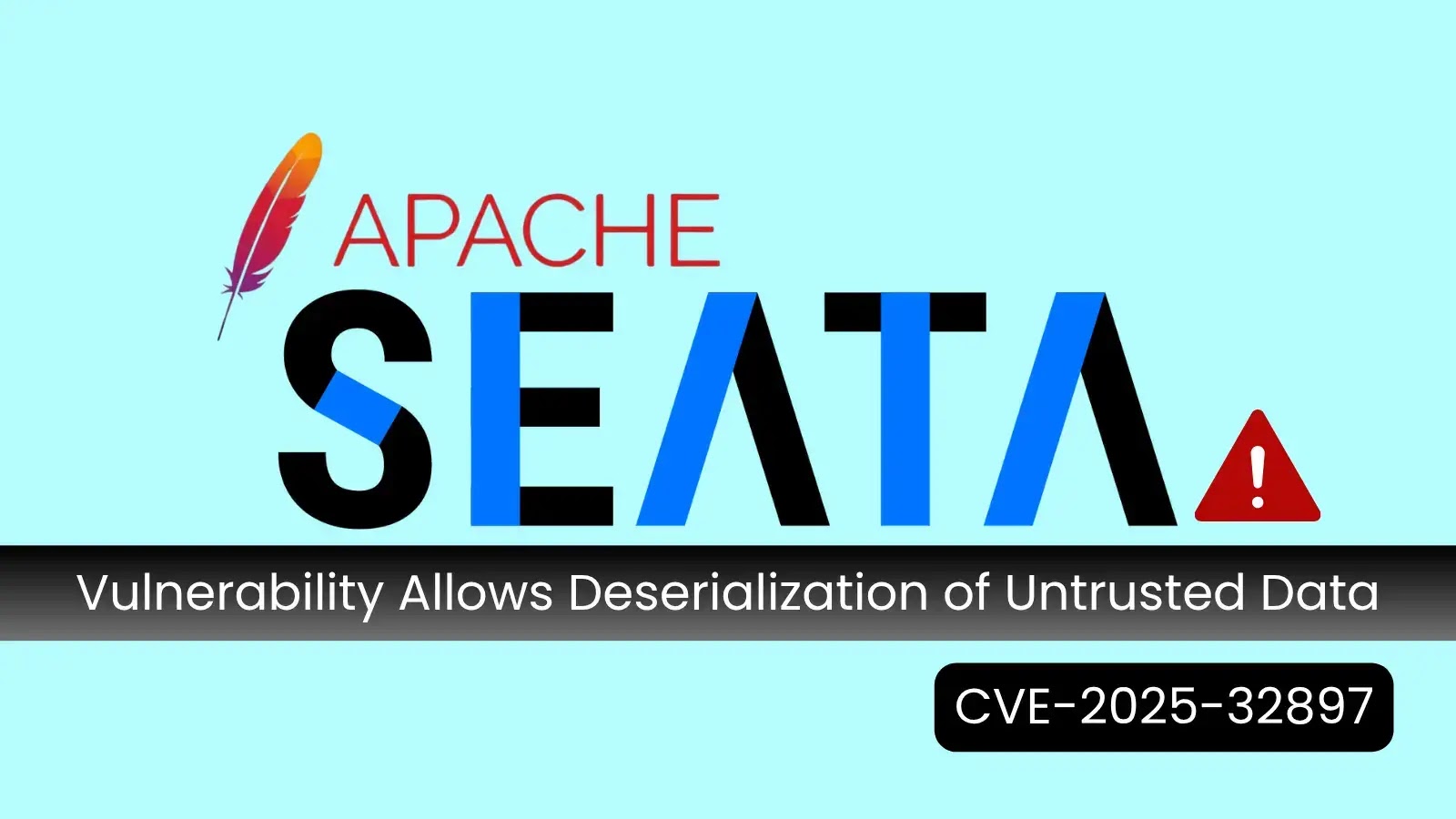
A newly disclosed vulnerability in Apache Seata, a popular open-source distributed transaction solution, has raised security concerns for organizations relying…
The weaponization of Windows shortcut (LNK) files for malware distribution has increased by an astounding 50%, according to telemetry data,…
A newly disclosed vulnerability in ModSecurity, a widely used open-source web application firewall (WAF), exposes servers to denial-of-service (DoS) attacks…
A newly disclosed vulnerability in the Python-based data-exfiltration utility used by the notorious Cl0p ransomware group has exposed the cybercrime…
Gamaredon, a Russia-aligned advanced persistent threat (APT) group attributed by Ukraine’s Security Service (SSU) to the FSB’s 18th Center of…
Ruichen Xiong, a student from China, has been sentenced to over a year in prison at Inner London Crown Court…
Microsoft has announced it will discontinue password management features in its widely used Authenticator app, marking a significant shift in…
Hackers are exploiting poorly managed Linux servers, particularly those with weak SSH credentials, to install proxy tools such as TinyProxy…