Category: GBHackers
LayerX, a cybersecurity firm, has uncovered a sophisticated network of malicious browser extensions, dubbed “sleeper agents,” that are currently installed…
IBM has issued a security bulletin highlighting multiple vulnerabilities in its QRadar Suite Software and Cloud Pak for Security platforms….
Authentication coercion remains a potent attack vector in Windows environments, enabling attackers with even low-privileged domain accounts to force targeted…
Forescout Research Vedere Labs has uncovered that nearly 35,000 solar power devices, including inverters, data loggers, and gateways from 42…
The North Korean state-sponsored hacking group APT37 has launched a sophisticated spear phishing campaign in March 2025, targeting activists focused…
Cybersecurity experts from Positive Technologies’ Security Expert Center have uncovered a sophisticated malicious campaign dubbed “Phantom Enigma,” primarily targeting Brazilian…
The Mobile Threat Intelligence (MTI) team identified a formidable new player in the mobile malware landscape: Crocodilus, an Android banking…
On May 15, 2025, Coinbase, the largest U.S. cryptocurrency exchange, publicly disclosed a major security breach that exposed the sensitive…
Threat actors have been found exploiting the ubiquitous “Prove You Are Human” verification systems to distribute malicious software. Specifically, this…
Researchers have unearthed a sophisticated supply chain attack targeting Ruby Gems, a popular package manager for the Ruby programming language….
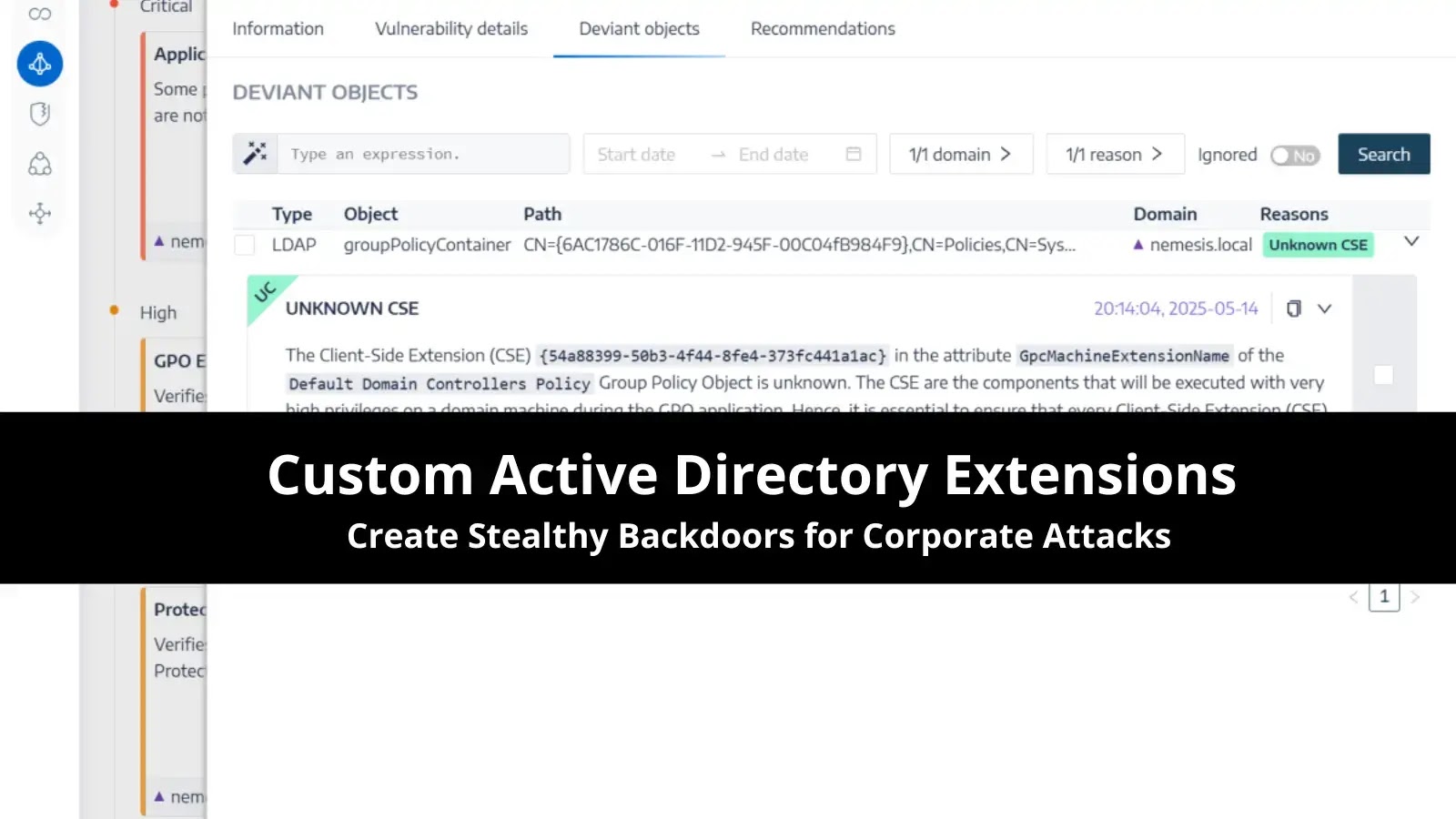
Active Directory (AD) Group Policy Objects (GPOs) are a cornerstone of centralized management for Windows environments, enabling administrators to configure…
Since 2016, the “DollyWay World Domination” campaign has quietly compromised more than 20,000 WordPress websites worldwide, exploiting vulnerabilities in plugins…