The Chinese APT hacking group “Mustang Panda” has been spotted abusing the Microsoft Application Virtualization Injector utility as a LOLBIN to inject malicious payloads into legitimate processes to evade detection by antivirus software.
This technique was discovered by threat researchers at Trend Micro, who track the threat group as Earth Preta, reporting that they have verified over 200 victims since 2022.
Mustang Panda’s targeting scope, based on Trend Micro’s visibility, includes government entities in the Asia-Pacific region, while the primary attack method is spear-phishing emails that appear to come from government agencies, NGOs, think tanks, or law enforcement.
The threat group was previously seen in attacks targeting governments worldwide using Google Drive for malware distribution, custom evasive backdoors, and a worm-based attack chain.
The emails spotted by Trend Micro contain a malicious attachment containing the dropper file (IRSetup.exe), a Setup Factory installer.
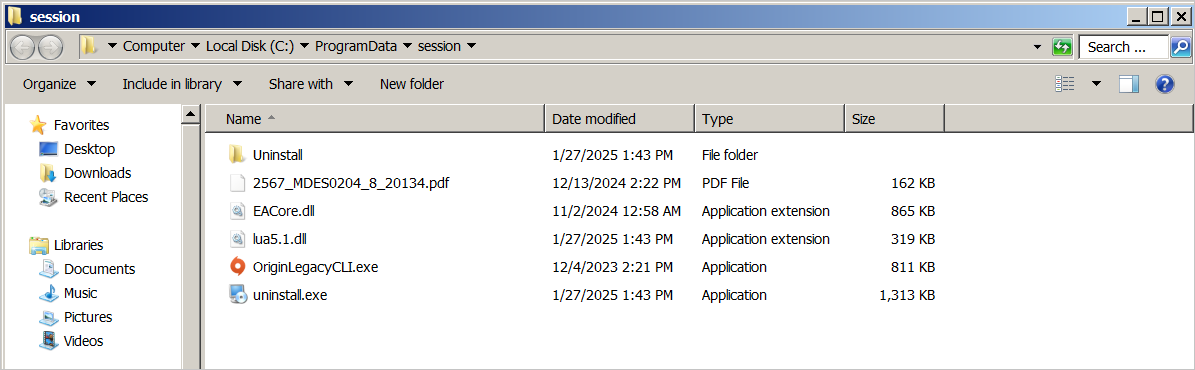
If executed by the victim, it will drop multiple files into C:ProgramDatasession, including legitimate files, the malware components, and a decoy PDF to serve as a diversion.
Source: Trend Micro
Evading antivirus
When ESET antivirus products are detected (ekrn.exe or egui.exe) on a compromised machine, Mustang Panda employs a unique evasion mechanism exploiting tools pre-installed on Windows 10 and later.
The abuse starts with the Microsoft Application Virtualization Injector (MAVInject.exe), a legitimate Windows system tool that allows the operating system to inject code into running processes.
It’s mainly used by Microsoft’s Application Virtualization (App-V) to run virtualized applications, but developers and admins can also use it to execute DLLs inside another process for testing or automation.
In 2022, cybersecurity firm FourCore reported that MAVInject.exe could be abused as a LOLBIN, warning that the executable should be blocked on devices not utilizing APP-v.
Mustang Panda abuses the executable to inject malicious payloads into ‘waitfor.exe,’ a legitimate Windows utility that comes pre-installed in Windows operating systems.
The legitimate function of waitfor.exe on Windows is to synchronize processes across multiple machines by waiting for a signal or command before executing a specific action.
It is primarily used in batch scripting and automation for delaying tasks or ensuring that specific processes finish before others start.
Being a trusted system process, the malware that is injected in it passes as a normal Windows process, so ESET, and potentially other antivirus tools, does not flag the malware’s execution.
The malware injected into waitfor.exe is a modified version of the TONESHELL backdoor, which comes hidden inside a DLL file (EACore.dll).
Once running, the malware connects to its command and control server at militarytc[.]com:443, and sends system info and victim ID.
.jpg)
Source: Trend Micro
The malware also provides attackers with a reverse shell for remote command execution and file operations, such as move and delete.
Trend Micro believes with medium confidence that this new variant is a custom Mustang Panda tool based on its functional characteristics and previously documented packet decryption mechanisms.
