SUMMARY
- Cicada3301 ransomware group claims to have breached Concession Peugeot, stealing 35GB of sensitive data.
- The group operates a Ransomware-as-a-Service (RaaS) model with a 20% commission.
- First observed in June 2024, their ransomware targets Windows and Linux/ESXi systems.
- Cicada3301 shares similarities with BlackCat, using ChaCha20 encryption and similar tactics.
- Leaked data includes invoices, passport copies, and internal communications.
Cicada3301, a ransomware group, has claimed responsibility for a data breach targeting Concession Peugeot (concessions.peugeot.fr), a prominent French automotive dealership linked to the Peugeot brand. The group claims to have stolen 35GB of sensitive data, marking a continuation of their aggressive cyber campaigns.
The alleged breach was announced by the group over the weekend (Sunday, December 15, 2024) on its official dark web leak site. It is also worth noting that the name Cicada3301 was historically associated with cryptographic puzzles in the early 2010s, it has since been co-opted by the ransomware group operating under a Ransomware-as-a-Service (RaaS) model.
This model enables affiliates to carry out attacks by renting the ransomware infrastructure and splitting the proceeds with the operators. Check Point’s report in September 2024, also discusses Cicada3301 who posted an advertisement on a Russian-language underground forum offering ransomware-as-a-service. The group demands a 20% commission on successful attacks and even provides negotiation mechanisms for disputes among partners.
The Cicada3301 ransomware group was first identified by cybersecurity firm Truesec and observed in June 2024. Written in Rust, the ransomware can target both Windows and Linux/ESXi systems, showcasing its cross-platform capabilities.
Cicada3301 has notable similarities to ALPHV/BlackCat ransomware, including the use of ChaCha20 encryption, identical commands to shut down virtual machines, and the -ui commands that provide graphic output for encryption. Both groups also share a similar file-naming pattern and key parameters used to decrypt ransom notes. These overlaps suggest a shared connection or the adoption of proven techniques to maximize efficiency and impact.
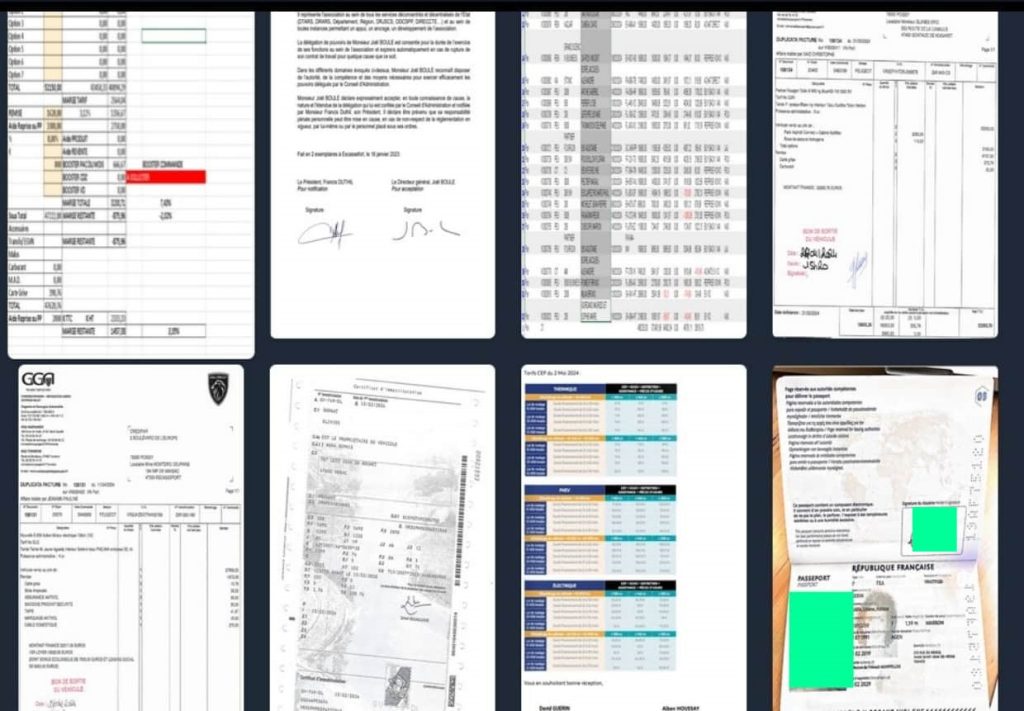
The attack on Concession Peugeot aligns with Cicada3301’s strategy of targeting high-value organizations to maximize impact. The theft of 35GB of data is particularly concerning, as a screenshot of the leaked files, reviewed by Hackread.com, reveals official and internal communications, invoices, passport copies, and even recipes.
Editor’s Note
The fact that Concession Peugeot operates under the official subdomain concessions.peugeot.fr creates a closer association with the larger Peugeot brand. Big companies like Peugeot often let their authorized dealerships use subdomains to maintain a consistent online presence and make it easier for customers to trust their services.
However, this setup means that an attack on a dealership can easily look like an attack on the main company. While this breach only targeted the dealership, the use of Peugeot’s domain could lead to confusion and raise questions about security across the brand.
RELATED TOPICS
- 13GB Data of Automobile Insurance Giant AA Exposed Online
- French automobile Citroën breached, user login details leaked
- Hackers Can Access Mazda Vehicle Controls Via System Flaws
- Contractor Database Exposes Irish Police Vehicle Seizure Records
- Nissan Confirms Data Breach Affected 100K Customers, Employees
- ALPHV Ransomware Used Vishing to Scam MGM Resorts Employee
